Table of Contents
Introduction
Zero Trust Security Model Introduction
The Zero Trust security model is a framework that promotes the idea of “never trust, always verify” when it comes to access to resources within an organization’s network. It assumes that all users and devices, whether inside or outside the network, should be treated as untrusted and should be required to prove their identity and the legitimacy of their actions before being granted access to resources.
Importance of security in virtual desktop environments
In the context of Azure Virtual Desktop (AVD), the Zero Trust model can be implemented using a combination of Microsoft Services and 3rd Party firewall.
Azure AD can be used to establish user identity and enforce access controls, while Azure AD Identity Protection can be used to monitor for suspicious activity and alert administrators of potential threats, also some other azure services that can be leveraged to improve security in virtual desktop environments.
Azure services that can be leveraged to implement the Zero Trust model in AVD:
Identity and access management
- Azure Conditional Access (Azure AD CA): This service allows administrators to set policies that specify the conditions under which users are allowed to access AVD resources.
- Azure multi-factor authentication (MFA): Use MFA to require users to provide additional authentication factors, such as a code sent to their phone, before accessing AVD resources.
- Azure AD Identity Protection: This service helps you to protect your organization from identity-based threats. It uses advanced machine learning and behavioral analytics to identify and mitigate potential threats to your organization’s identities, such as compromised accounts, risky sign-ins, and suspicious IP addresses.
Data and Threat Protection
- Azure Disk Encryption: This feature allows you to encrypt the OS and data disks of virtual machines (VMs) running in Azure. It uses the industry-standard BitLocker feature of Windows and the DM-Crypt feature of Linux to provide volume encryption for the OS and data disks.
- Microsoft Information Protection (MIP): This service can be used to classify and protect sensitive data within AVD.
- Windows Information Protection (WIP): This service helps to protect against data leaks and unauthorized access to sensitive information. In Azure Virtual Desktop (AVD), you can use WIP to protect data on session hosts and ensure that users have appropriate access to sensitive data.
- Azure Advanced Threat Protection (ATP): help to identify and mitigate advanced threats and attacks in your AVD environment, improving the overall security posture of your AVD resources.
By implementing the Zero Trust model in AVD, organizations can significantly reduce the risk of unauthorized access to their virtual desktop resources and ensure that only authorized users are able to access sensitive data.
Security and Compliance
- Microsoft Defender for Cloud: This service can be used to implement security and compliance recommendations, as well as track the progress and effectiveness of your security efforts.
- Azure Firewall: Implement Azure Firewall to protect against external threats and control access to AVD resources.
- Azure Network Security Groups (NSG): These can be used to control inbound and outbound network traffic to AVD resources.
- Azure Bastion: This service enables secure and seamless RDP and SSH access to virtual machines in Azure. It allows you to connect to your virtual machines using a browser, eliminating the need to open inbound ports or use a VPN to access your resources.
- Azure Policy: This service in Azure allows you to enforce compliance and governance standards across your Azure resources and ensure that resources are deployed in compliance with organizational standards.
Monitoring
- Azure Sentinel: This service can be used to monitor and protect Azure Virtual Desktop (AVD) environments by collecting, analyzing, and storing data from a variety of sources, including logs from AVD resources, Azure AD, and Azure Defender.
- Azure Log analytics: This service allows you to collect and analyze log data from AVD resources and provides you with a centralized view of the performance and health of your resources.
- Azure Monitor: This service provides a set of tools and capabilities to monitor, troubleshoot, and optimize your AVD environment. It allows you to collect and analyze telemetry data from AVD resources, such as session hosts and user sessions.
- Azure Alerts: This service allows you to create, manage, and receive notifications for specific conditions on your Azure resources and enables you to monitor your resources and take action when specific conditions occur, such as resource thresholds being exceeded, or security breaches being detected.
Identity and Access Management best practice for AVD
Control user access in Azure Virtual Desktop sessions
There are several built-in roles for use with Azure Virtual Desktop which is a collection of permissions. To control user access in Azure Virtual Desktop (AVD) sessions, you can follow these steps:
Add a new role assignment.
- Go to the Azure portal and navigate to the AVD resource group.
- Select “Access control (IAM)” and add a new role assignment.
- Choose one of built-in roles for Azure Virtual Desktop like:
- Virtual Machine User Login
- Virtual Machine Administrator Login
- Desktop Virtualization User
- Desktop Virtualization Power On Off Contributor

- Assign it to the desired users.
RBAC roles to manage and control Azure Virtual Desktop
Here is a table of some RBAC roles that are available for managing and controlling Azure Virtual Desktop (AVD):
| Role | Description |
| Desktop Virtualization User | Allows users to connect to AVD sessions, use applications and resources in the sessions, and perform some basic management tasks such as resetting their own password or updating their profile. |
| Desktop Virtualization User Session Operator | allows users to send messages, disconnect sessions, and use the “logoff” function to sign sessions out of the session host. However, this role doesn’t let users perform session host management like removing session host, changing drain mode, and so on. This role can see assignments but can’t modify admins. |
| Desktop Virtualization Host Pool Contributor | allows users to manage all aspects of host pools, including access to resources. You’ll also need the Virtual Machine Contributor role to create virtual machines. You will need Desktop Virtualization Application Group Contributor and Desktop Virtualization Workspace Contributor roles to create host pools using the portal, or you can use the Desktop Virtualization Contributor role. |
| Desktop Virtualization Contributor | allows users to manage all aspects of the deployment. However, it doesn’t grant users access to compute resources. You’ll also need the User Access Administrator role to publish application groups to users or user groups. |
| Desktop Virtualization Reader | allows users to view everything in the deployment but doesn’t let them make any changes. |
| Desktop Virtualization Power On Off Contributor | allows the Azure Virtual Desktop Resource Provider to start and stop virtual machines. |
| Desktop Virtualization Virtual Machine Contributor | allows the Azure Virtual Desktop Resource Provider to create, delete, update, start, and stop virtual machines. |
Set up MFA and Azure AD Conditional Access policies:
Configure Azure AD Conditional Access
- Go to the Azure portal and navigate to the “Azure Active Directory” service.
- Select “Conditional access” and create a new policy.
- Configure the desired access controls, such as requiring multi-factor authentication or blocking access from certain locations.
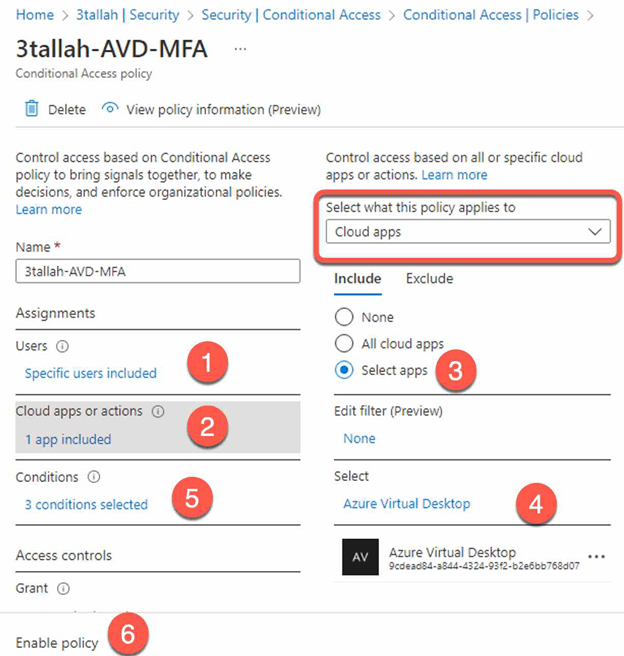
Test the access controls:
- Log in to an AVD session as a user who is subject to the access controls.
- Verify that the access controls are enforced as expected.
By following these steps, you can restrict access to the session hosts and ensure that only authorized users are able to log in. This can help to prevent unauthorized access to the session hosts and protect your data.
Enable SSO and Passwordless authentication on AVD
The latest upgrade to Microsoft Azure Virtual Desktop (AVD) now allows users to access the service through single sign-on (SSO) and passwordless authentication. This feature is currently in public preview and can be enabled with Azure AD. Additionally, users can utilize Windows Hello and security devices like FIDO2 keys for passwordless authentication, as explained by Microsoft’s David Belanger in a recent blog post.
Note: These features are currently in preview and only available on on Windows 11 22H2 Enterprise Preview (mono and multi session) X64 Gen 2 as session host
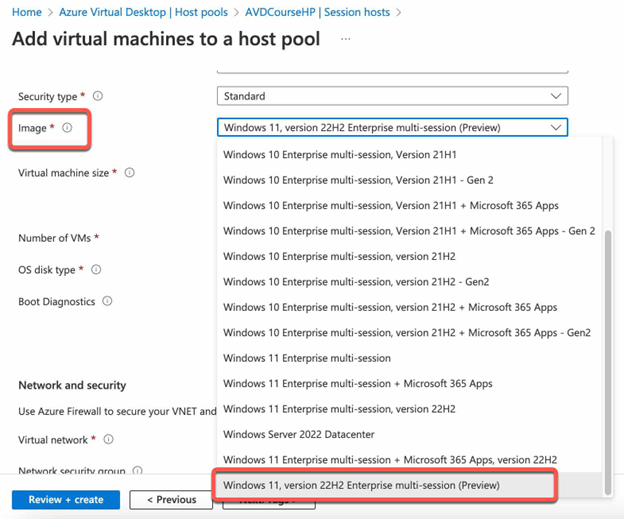
Configure SSO for Azure Virtual Desktop:
- Ensure that you are using Azure AD Joined or Hybrid Joined (Active Directory) virtual machines; SSO does not support Azure AD Domain Services joined virtual machines.
- If using Hybrid Joined VM, first enable Azure AD for Kerberos support (https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-security-key-on-premises#create-a-kerberos-server-object)
- Use the latest version of Windows Desktop Client (https://docs.microsoft.com/en-us/azure/virtual-desktop/user-documentation/connect-windows-7-10#install-the-windows-desktop-client)
- Customize the RDP property by setting the Azure AD Authentication to “RDP will attempt to use Azure AD Authentication to sign in“
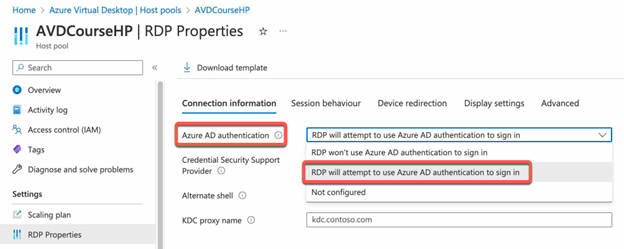
- Or set the enablerdsaadauth RDP properties to 1 like this enablerdsaadauth:i:1
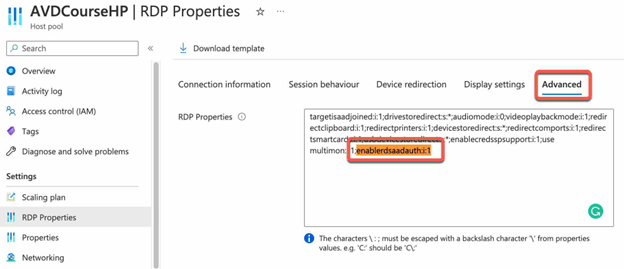
- The first time the user logs onto the session host, they will be prompted to authenticate with Azure AD and allow the remote desktop connection.
- Azure AD will remember up to 15 hosts for 30 days before a new authentication prompt
Configure Passwordless for Azure Virtual Desktop:
- Use Windows Hello for Business to enable passwordless authentication
- In addition to the session host-supported version listed above, use one of these versions as your local OS
- Windows 11 Enterprise single or multi-session with the 2022-09 Cumulative Updates for Windows 11 Preview (KB5017383) or later installed.
- Windows 10 Enterprise single or multi-session, versions 20H2 or later with the 2022-09 Cumulative Updates for Windows 10 Preview (KB5017380) or later installed.
- Windows Server 2022 with the 2022-09 Cumulative Update for Microsoft server operating system preview (KB5017381) or later installed.
- Edit the RDP properties to configure the WebAuth redirection option to “WebAuth requests in the remote session are redirected to the local computer”
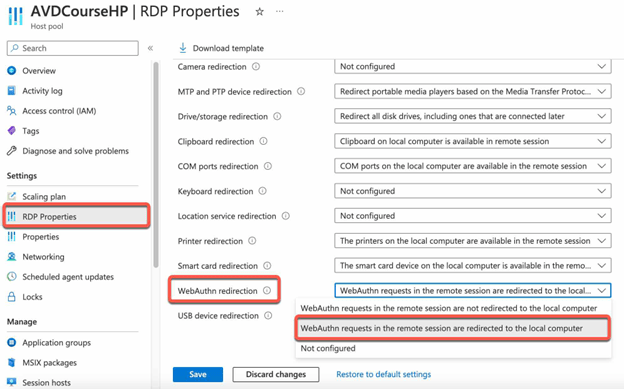
- Or set the redirectwebauthn RDP properties to 1 like this redirectwebauthn:i:1

- To enable FIDO2 keys, configure it as an authentication method for your users – see https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-security-key#enable-fido2-security-key-method
Note that you need to make sure that you are using the correct version of Windows and RDP properties to enable these features on AVD.
For more information check:
- https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-passwordless
- https://learn.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview
Control session behavior, and more using RDP properties for AVD
To control device redirection and Remote Desktop Protocol (RDP) properties for Azure Virtual Desktop (AVD), you can follow these steps:
Configure RDP properties from AVD Portal
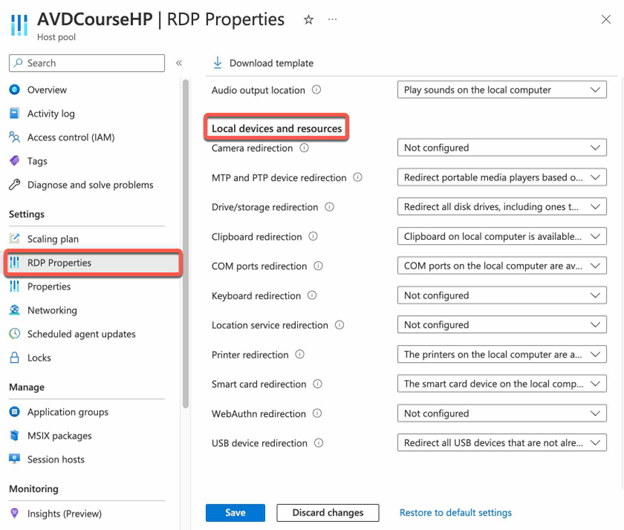
You can centrally set Remote Desktop Protocol (RDP) properties in Azure Virtual Desktop to control how connections behave. These properties include options for device redirection, display settings, session behavior, and more. For further details, refer to the documentation on customizing RDP properties for a host pool.
To configure RDP properties in the Azure portal:
- Sign into the select Azure Virtual Desktop.
- At the Azure Virtual Desktop page, select host pools in the menu on the left side of the screen.
- Select the name of the host pool you want to update.
- Select RDP Properties in the menu on the left side of the screen.
- Set the property you want.
Also, you can open the Advanced tab and add your RDP properties in a semicolon-separated format like the below.
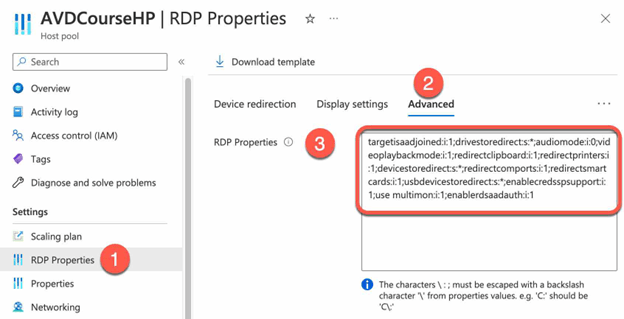
For more information, see Supported RDP properties with Azure Virtual Desktop – Azure Virtual Desktop | Microsoft Learn
Set up Group Policy for Device and Resource Redirection:
- Open the Group Policy Management Console on a domain controller.
- Create a new GPO and link it to the organizational unit (OU) or domain containing the AVD users.
- Configure device redirection:
- In the GPO, go to “Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Device and Resource Redirection”.
- Enable or disable the desired device redirection policies like:
- Allow audio and video playback redirection
- Allow audio recording redirection
- Allow time zone redirection
- Do not allow COM port redirection
- Do not allow Clipboard redirection
- Do not allow LPT port redirection
- Do not allow smart card device redirection
- Do not allow supported Plug and Play device redirection
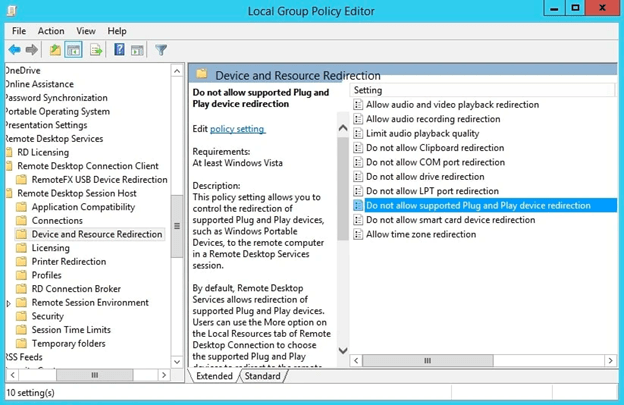
- Save
Set up Group Policy for Remote Desktop Session Host:
- In the GPO, go to “Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host”.
- Enable or disable the desired RDP properties like:
- Set client connection encryption level
- Set time limit for active but idle Remote Desktop Services sessions
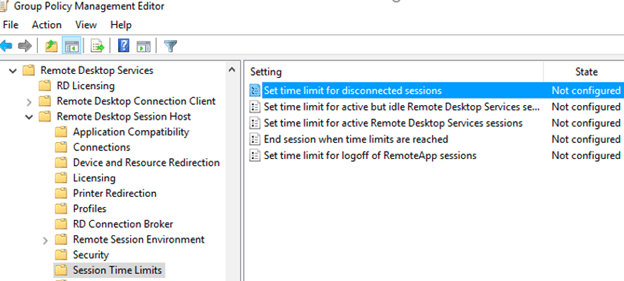
Test the policies.
- Log in to an AVD session as a user who is subject to the policies.
- Verify that the policies are enforced as expected and that the device redirection and RDP properties are as desired.
By following these steps, you can control device redirection and RDP properties for AVD. This can help improve the security and efficiency of your AVD environment by
Set up screen locks for idle sessions for AVD users
To set up screen locks for idle sessions for Azure Virtual Desktop (AVD) users, you can follow these steps:
- Set up Group Policy:
- Open the Group Policy Management Console on a domain controller.
- Create a new GPO and link it to the organizational unit (OU) or domain containing the AVD users.
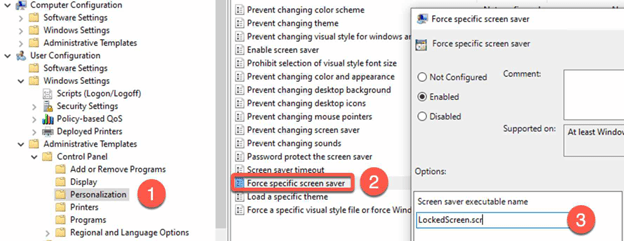
Configure the screen lock policy:
- In the GPO, go to “Computer Configuration > Policies > Administrative Templates > Control Panel > Personalization”.
- Enable the “Force specific screen saver” policy and set the desired screen saver (e.g. “LockedScreen.scr”).
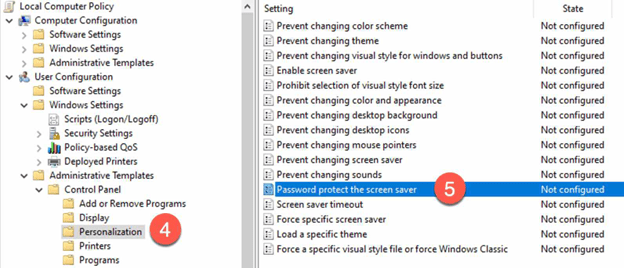
- Enable the “Password protect the screen saver” policy.
Configure the idle timeout:
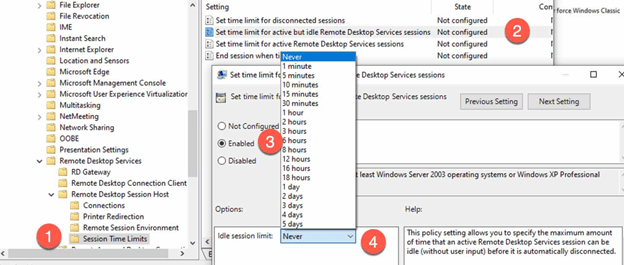
- In the GPO, go to “Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Session Time Limits”.
- Enable the “Set time limit for active but idle Remote Desktop Services sessions” policy and set the desired idle timeout.
Test the policies:
- Log in to an AVD session as a user who is subject to the policies.
- Verify that the policies are enforced as expected and that the screen lock is activated after the specified idle timeout.
By following these steps, you can set up screen locks for idle sessions for AVD users. This can help improve the security of your AVD environment by requiring users to reauthenticate after a period of inactivity.
Set maximum inactive time and session end policies for AVD Users
To create a Group Policy object (GPO) to establish maximum inactive time and disconnection policies for Azure Virtual Desktop (AVD) users, you can follow these steps:
- Set up Group Policy:
- Open the Group Policy Management Console on a domain controller.
- Create a new GPO and link it to the organizational unit (OU) or domain containing the AVD users.
Configure the maximum inactive time policy:
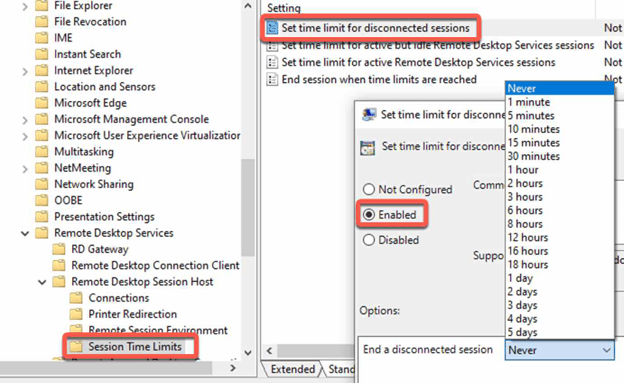
- In the GPO, go to “Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Session Time Limits”.
- Enable the “Set time limit for disconnected sessions” policy and set the desired maximum inactive time.
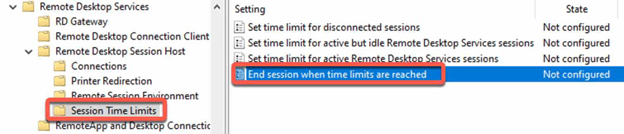
Configure the session end policy:
- In the GPO, go to “Computer Configuration > Policies > Administrative Templates > Windows Components > > Remote Desktop Services > Remote Desktop Session Host > Session Time Limits”.
- Enable the “End session when time limits are reached ” policy.
Test the policies:
- Log in to an AVD session as a user who is subject to the policies.
- Verify that the policies are enforced as expected and that the maximum inactive time and disconnection behavior are as desired.
By following these steps, you can create a GPO to set the maximum inactive time and session end policies for AVD users. This can help improve the security and efficiency of your AVD environment by limiting the amount of time that users can be inactive or disconnected before their sessions are terminated.
Enable External identity to access your AVD
Azure Virtual Desktop currently doesn’t support external identities, you could think about creating user account in your AD for External identities with limited access to separated AVD Resources
- The user must be sourced from the same Active Directory that’s connected to Azure AD. Azure Virtual Desktop does not support B2B or MSA accounts.
- The UPN you use to subscribe to Azure Virtual Desktop must exist in the Active Directory domain the VM is joined to.
Data encryption and Threat Protection best practice for AVD
Enable Azure Disk Encryption for Session host disks
When deploying Session host (virtual machines) in Microsoft Azure, they are not enabled with Bitlocker by default. To address this issue and comply with corporate security policies, Azure Disk Encryption (ADE) can be utilized. ADE provides volume encryption for Azure VMs through the use of Bitlocker or DM-Crypt.
As there is no TPM present, ADE requires a secret for encrypting data. This secret is obtained from Azure Key Vault, a cloud-based service for securely storing and accessing secrets. To ensure the protection of this secret, a key can be generated from Azure Key Vault or brought in from an external hardware security module (HSM) device. we will explore the configuration of both services to encrypt a Windows Azure VM.
Create an Azure key vault:
- From the Azure portal select “Create a resource”.
- In the Search box, enter “Key Vault”
- On the Key Vault section, choose “Create”
- On the Create key vault section provide the following information:
- Name: A unique name is required.
- Subscription: Choose a subscription.
- Under Resource Group, choose “Create new” and enter a resource group name.
- In the Location pull-down menu, choose a location.
- Leave the other options to their defaults.
- Select “Create” to finish creating the vault.
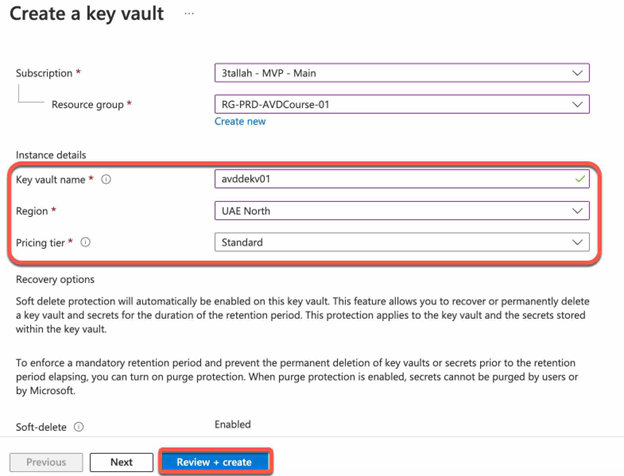
Note that you need to provide a unique name and choose the right subscription, location and resource group to create a vault on Azure.
Configure Azure Key Vault:
- Navigate to your Azure Key Vault and select “Access Policies” to configure access for Azure Disk Encryption
- In Access Policies, be sure that Azure Disk Encryption for volume encryption is enabled.
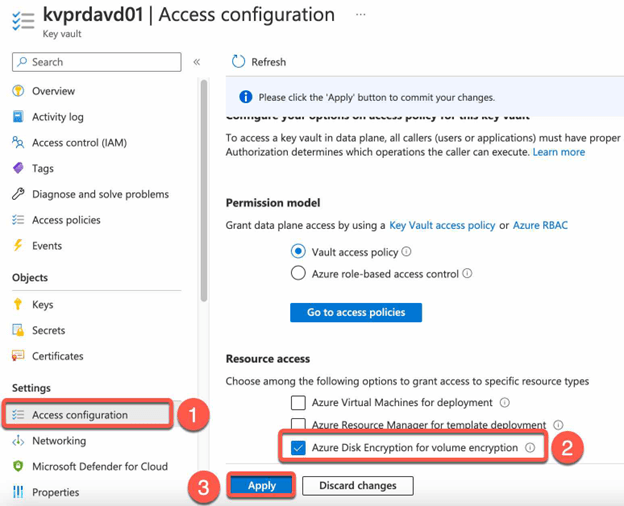
- Next, we need a key. For that navigate to Keys in Azure Key Vault. Select Generate / Import.
- In the Access Policies menu, there are two options available for securing your data: generating a key managed by Microsoft or importing a key exclusive to your organization. For sensitive information, it is recommended to import your own key.
- For the purpose of this example, a key will be generated. As of now Windows Server 2022 and Windows 11 include a newer version of BitLocker and currently doesn’t work with RSA 2048-bit Key Encryption Keys. Until resolved, Microsoft Recommend to use an RSA 3072 or RSA 4096-bit keys.

- At this point, Azure Key Vault is configured and ready for Azure Disk Encryption.
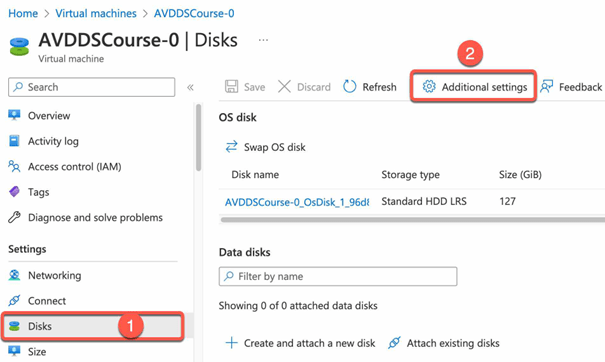
Enable Azure Disk Encryption
- To activate Azure Disk Encryption, the Azure VM must be in a powered-on state. To proceed, navigate to the Azure VM and select “Disks” then “Additional settings”.
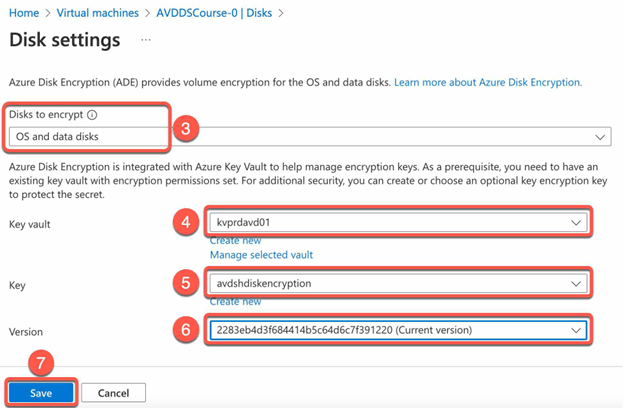
- In the Additional settings, select the disk that you wish to encrypt and then choose the appropriate key vault, key and version.
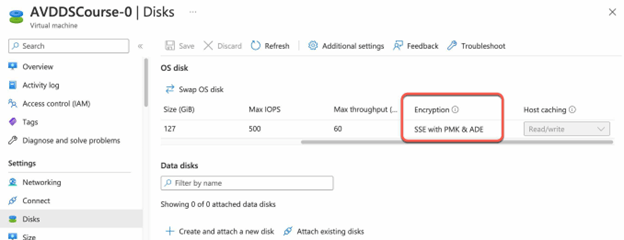
- Once the settings have been applied in Azure Disk Encryption, Bitlocker will be enabled on the Azure VM and the disk will begin encrypting.
Manage your AVD Data on Azure Files Share using Microsoft Purview
Prerequisites
For the prerequisites and registering Azure Files account in your data catalog, follow these steps: https://learn.microsoft.com/en-us/azure/purview/register-scan-azure-files-storage-source#prerequisites
Scan Azure Files and classify data using Microsoft Purview:
- Select the Data Map tab on the left pane in the Microsoft Purview governance portal.
- Select the Azure Files source that you registered.
- Select “New scan”.
- Select the account key credential to connect to your data source.
- Scope your scan to specific databases by choosing the appropriate items in the list.
- Select a scan rule set. You can choose between the system default, existing custom rule sets, or create a new rule set inline.
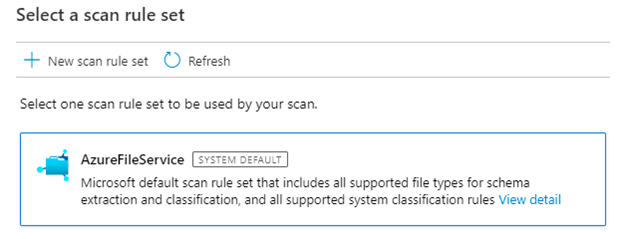
- Choose your scan trigger. You can set up a schedule to reoccur or run the scan once.
- Review your scan and select “Save and run”.
View existing scans:
- Go to the Microsoft Purview governance portal.
- Select the Data map tab on the left pane.
- Select the desired data source. You can view a list of existing scans on that data source under “Recent scans”, or you can view all scans on the “Scans” tab.
- Select the scan that has results you want to view. The page shows you all of the previous scan runs, along with the status and metrics for each scan run.
- Click the run ID to check more about the scan run details.
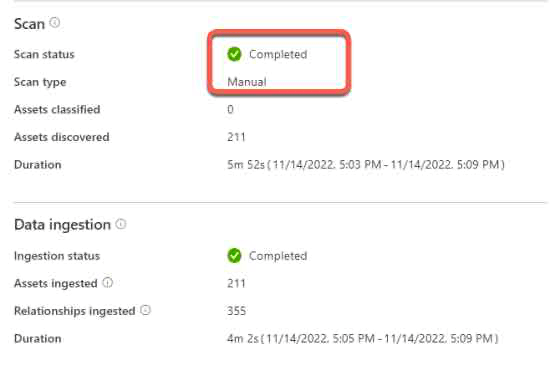
For more details check this article: https://learn.microsoft.com/en-us/azure/purview/register-scan-azure-files-storage-source
Control how users copy and transfer data on AVD
To control how users copy and transfer data on Azure Virtual Desktop (AVD), you can follow these steps:
- Set up Group Policy:
- Open the Group Policy Management Console on a domain controller.
- Create a new GPO and link it to the organizational unit (OU) or domain containing the AVD users.
Configure clipboard redirection:
- In the GPO, go to “Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Device and Resource Redirection”.
- Enable or disable the “Do not allow clipboard redirection” policy as desired.
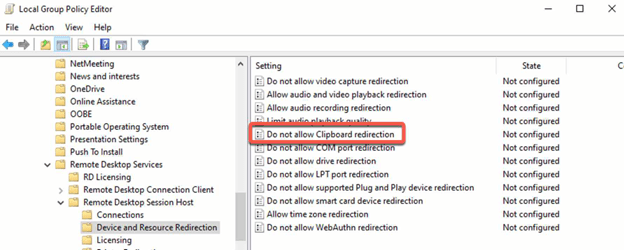
Configure file transfer:
- In the GPO, go to “Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Device and Resource Redirection”.
- Enable or disable the “Do not allow drive redirection” policy as desired.
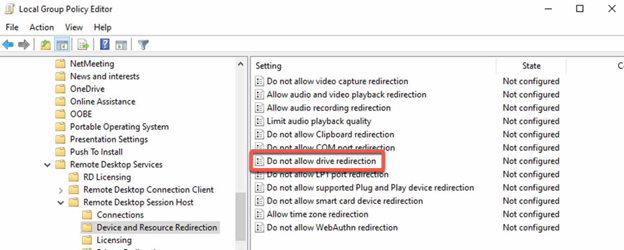
Test the policies:
- Log in to an AVD session as a user who is subject to the policies.
- Verify that the policies are enforced as expected and that clipboard redirection and file transfer are controlled as desired.
By following these steps, you can control how users copy and transfer data on AVD. This can be particularly useful for preventing unauthorized data transfers or for limiting the amount of data that users can copy and paste between the session hosts and their local devices.
Restrict access for a local and remote drives on user session
To restrict access to local and remote drives on user sessions, you can follow these steps:
- Set up Group Policy:
- Open the Group Policy Management Console on a domain controller.
- Create a new GPO and link it to the organizational unit (OU) or domain containing the users.
Configure drive redirection:
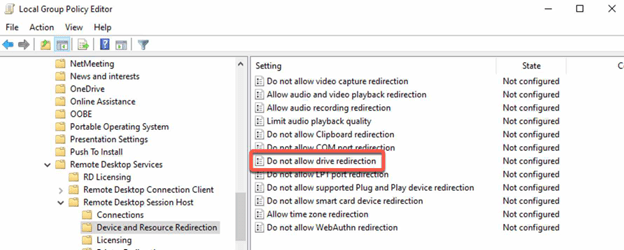
- In the GPO, go to “Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Device and Resource Redirection”.
- Enable or disable the “Do not allow drive redirection” policy as desired.
Configure mapped drives:
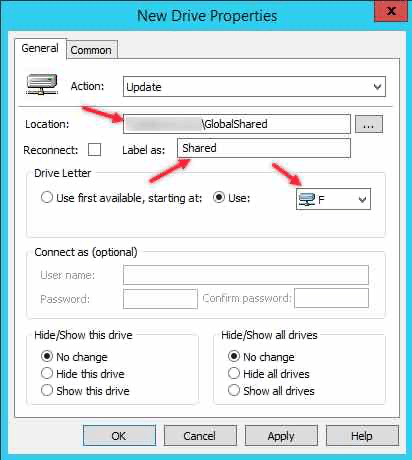
- In the GPO, go to “User Configuration > Preferences > Windows Settings > Drive Maps”.
- Create a new drive mapping and configure the desired drive letter, network path, and other settings.
Test the drive restrictions:
- Log in to a user session as a user who is subject to the drive restrictions.
- Verify that the drive restrictions are enforced as expected and that the mapped drives are available as desired.
By following these steps, you can restrict access to local and remote drives on user sessions, helping to improve the security and efficiency of your environment. This can be particularly useful for preventing unauthorized access to data on the local or remote drives or for limiting the amount of data that users can access on these drives.
Enable screen capture protection for AVD
To use screen capture protection on Azure Virtual Desktop, you must use one of the following clients:
- The Windows Desktop client supports screen capture protection for full desktops only.
- The macOS client (version 10.7.0 or later) supports screen capture protection for both RemoteApps and full desktops.
It is important to use the correct client to access screen capture protection feature on Azure Virtual Desktop.
To configure screen capture protection on Azure Virtual Desktop follow the below steps
- Download the Azure Virtual Desktop policy templates file (AVDGPTemplate.cab): https://aka.ms/avdgpo and extract the contents of the cab file and zip archive.
- Copy the terminalserver-avd.admx file to the %windir%\PolicyDefinitions folder.
- Copy the en-us\terminalserver-avd.adml file to the %windir%\PolicyDefinitions\en-us folder.
- Open the Group Policy Editor and navigate to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Azure Virtual Desktop. You should see one or more Azure Virtual Desktop policies.

- Open the “Enable screen capture protection” policy and set it to “Enabled”.
- You can also install administrative templates to the group policy Central Store in your Active Directory domain. For more information, check this: https://learn.microsoft.com/en-us/troubleshoot/windows-client/group-policy/create-and-manage-central-store
Implement Windows Defender Application Control for AVD
Windows Defender Application Control is a way to whitelist applications and DLLs on your Windows 10 Professional and Enterprise environments.
To implement Windows Defender Application Control using Microsoft Mobile Device Management (Intune) on Azure Virtual Desktop (AVD) session hosts, you can follow one of these steps:
- From the Endpoint Manager Portal, choose Devices > Configuration Profiles
- Click on Create Profile > Profile: Windows 10 or later
- Select Profile Type: Templates > Template Name: Endpoint Protection.
- In the Basics tab provide a name for the Policy
- In the Configuration settings tab expand (Configure Microsoft Defender Application Control)
- Enforce application control code integrity
- Enable Trusted Apps with a good reputation

- In the Assignments tab (Select the target Group for AVD User) then create
NOTE: Only Windows components, Microsoft store apps, and reputable apps as defined by the Intelligent Security Graph will be allowed to run
By deploying WDAC policies following highlighted steps, you can effectively implement Windows Defender Application Control on your AVD session hosts, helping to protect against malware and other threats by controlling which applications are allowed to run on the virtual desktop resources. This can help improve the security and stability of your AVD environment.
Security and Compliance best practice for AVD
Network Security Configuration for AVD
Azure Network Security Groups (NSG) rules for traffic in AVD:
Here is a table of some example Network Security Group (NSG) rules for inbound and outbound traffic in Azure Virtual Desktop (AVD):
| Rule name | Direction | Protocol | Port range | Source (inbound) or Destination (outbound) | Description |
| Azure Services traffic | Outbound | TCP | 443 | Azure services | Allows outgoing traffic from AVD session hosts and host pools to Azure services over ports 80 and 443. This is necessary for AVD host resources to access Azure resources and services, such as Azure Monitor or Azure Log Analytics. |
| Management traffic | Inbound | TCP | 3389 | Management subnet | Allows incoming RDP traffic from the management subnet to AVD session hosts and host pools over port 3389. This is necessary for administrators to connect to AVD host resources for management and maintenance purposes. |
| Windows Update traffic | Outbound | TCP | 80, 443 | Microsoft Update services | Allows outgoing traffic from AVD session hosts and host pools to Microsoft Update services over ports 80 and 443. This is necessary for AVD host resources to receive updates and patches from Microsoft. |
| File and printer sharing | Outbound | TCP | 139, 445 | File share and printer Network | Allows outgoing File and Printer Sharing traffic to AVD session hosts and host pools over ports 139 and 445. This is necessary for users to access shared files and printers on AVD host resources. |
| Internet browsing traffic | Outbound | TCP | 80, 443 | Internet | Allows outgoing traffic from AVD session hosts and host pools to the internet for internet browsing purposes over ports 80 and 443. This is necessary for users to access internet resources and services from AVD host resources. |
| Management traffic | Inbound | TCP | 22 | Management subnet | Allows incoming Secure Shell (SSH) traffic from the management subnet to AVD session hosts and host pools over port 22. This is necessary for administrators to connect to AVD host resources for management and maintenance purposes using SSH. |
These are just a few examples of NSG rules that may be necessary for AVD. You can customize the NSG rules for your AVD environment to meet your specific security and networking requirements.
Protect your Azure Virtual Desktop using Azure Firewall
To use internal firewalls and User Defined Routes (UDRs) for Azure Virtual Desktop (AVD) users, you can follow these steps:
Set up the internal firewalls:
- Go to the Azure portal and navigate to Virtual network.
- Select the AVD Virtual network.
- Create a subnet named AzureFirewallSubnet, with an address range of at least /26.
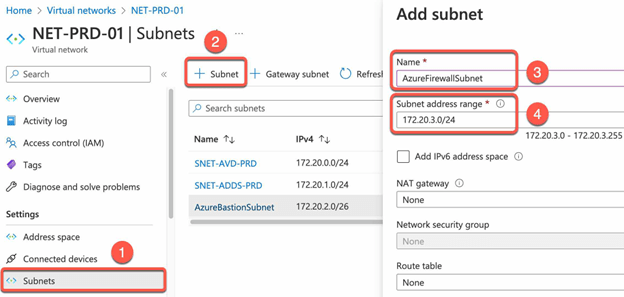
- Create An additional dedicated subnet named AzureFirewallManagementSubnet (minimum subnet size /26) is required with its own associated public IP address.
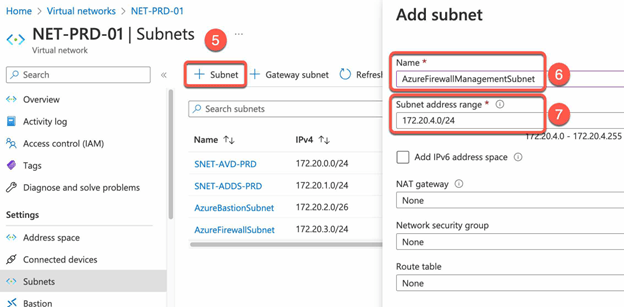
- Navigate back to AVD Virtual network and click on the “Firewall” tab.
- Click on add a new firewall.
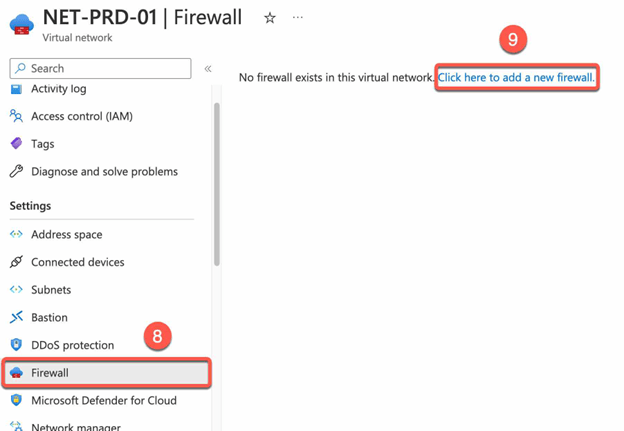
- Set firewall Name and region.

- Select the desired Firewall SKU
- Create a new firewall policy with the default settings and select AVD Virtual Network.
- Create Public IP for the Firewall Services and Public IP for the Firewall Management.
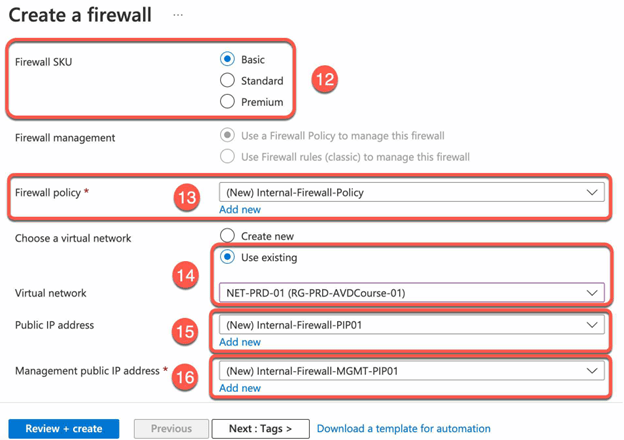
- Review and Create
Configure firewall rules:
- Navigate to the Firewall Manager | Azure Firewall Policies
- Select the Internal-Firewall-Policy that we created in the previous step.
- Select the desired firewall settings like (Network rules or DNAT rules or Application rules).
- In this example, we will configure Network rules and Application rules
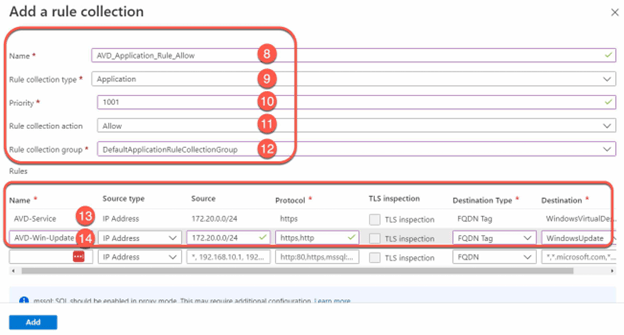
- Select Network rules and add a rule collection.
- In this network rule collection, we create a new rule to allow DNS access from your Active Directory Domain Services (ADDS) and KMS access servers subnet range (172.20.1.0/24) from your virtual machines to Windows Activation Service.

- Create an application rule collection and add a rule to enable the WindowsVirtualDesktop FQDN tag. The source IP address range is the host pool virtual network, the protocol is https, and the destination is WindowsVirtualDesktop.
- Add another rule to enable the WindowsUpdate FQDN tag. The source IP address range is the host pool virtual network, the protocol is https, http, and the destination is WindowsUpdate.
Set up UDRs:
- Go to the Azure portal and navigate to Route Tables.
- Create New Route Table.
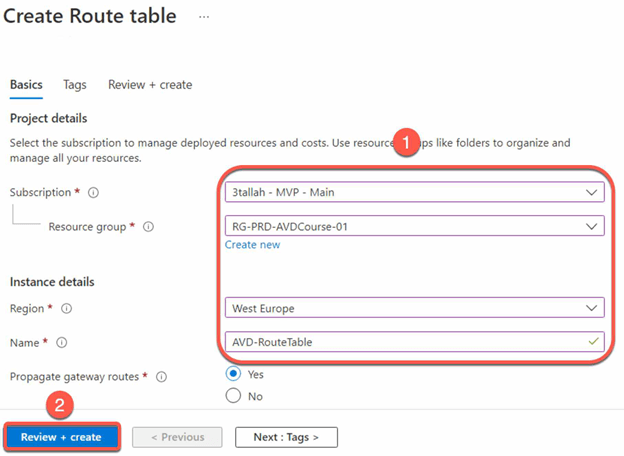
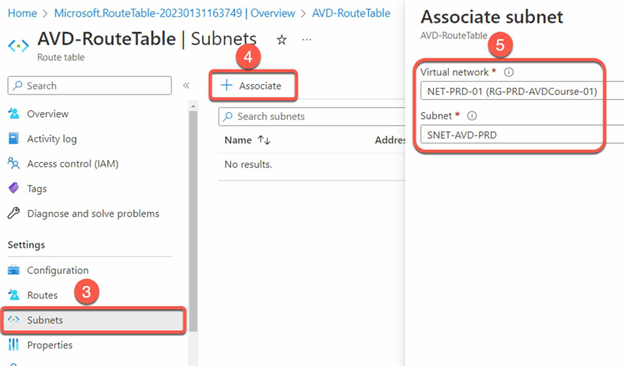
- Associate the desired subnets (e.g. AVD and ADDS subnets)
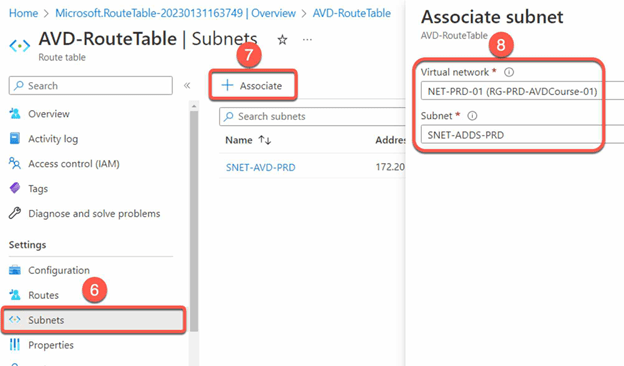
- Create the desired routes (e.g. routes to AVD and ADDS subnets or to Azure Firewall).
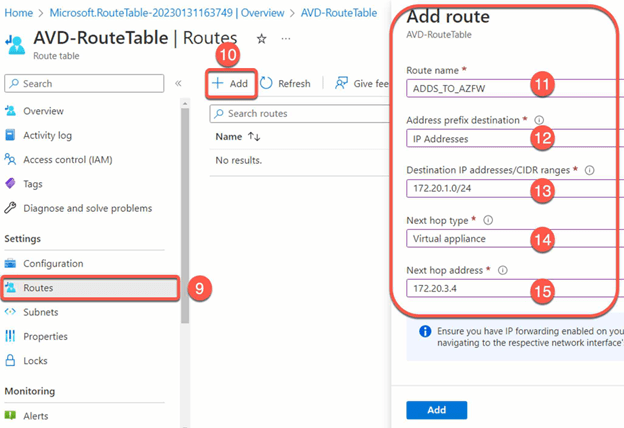
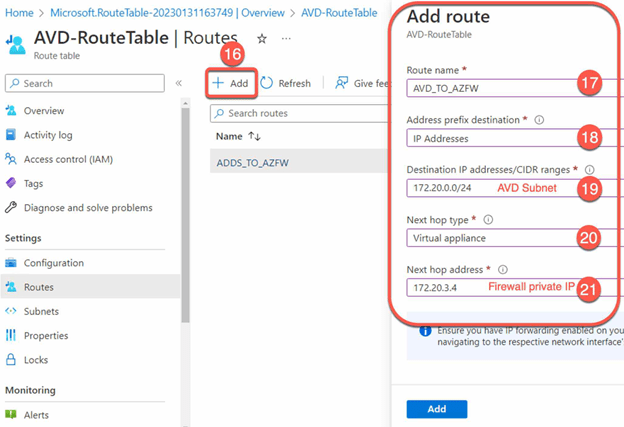
Test the firewalls and UDRs:
- Log in to an AVD session as a user and verify that the firewalls and UDRs are working as expected.
By following these steps, you can use internal firewalls and UDRs for AVD users, helping to improve the security and connectivity of your virtual desktop environment. The internal firewalls can help to block unwanted traffic, while the UDRs can help to route traffic as desired. This can be particularly useful for connecting AVD users to on-premises resources or for segmenting the virtual desktop network.
Firewall policies that we can apply to control AVD host sessions and user access
Here is a table of some firewall policies that can be applied to control Azure Virtual Desktop (AVD) host sessions and user access:
| Policy name | Description | |
| Block incoming connections | Blocks all incoming connections to AVD host resources, such as session hosts and host pools, except those that are explicitly allowed. This can help to prevent unauthorized access and protect against security threats. | |
| Allow outgoing connections | Allows all outgoing connections from AVD host resources, such as session hosts and host pools, except those that are explicitly blocked. This can help to ensure that the resources can communicate with other resources and services as needed. | |
| Allow specific incoming IPs | Allows incoming connections to AVD host resources, such as session hosts and host pools, from specific IP addresses or ranges. This can help to allow connections from trusted sources, while blocking connections from untrusted sources. | |
| Allow specific outgoing domains | Allows outgoing connections from AVD host resources, such as session hosts and host pools, to specific domains. This can help to allow access to certain websites or services, such as business or education sites, while blocking access to other websites or services. | |
| Allow specific outgoing IP addresses | Allows outgoing connections from AVD host resources, such as session hosts and host pools, to specific IP addresses. This can help to allow access to certain devices or locations, such as business partners or trusted networks, while blocking access to other devices or locations. | |
By implementing these firewall policies, you can further control user internet access on your AVD host resources. This can help to meet compliance requirements, prevent the use of unauthorized or inappropriate websites or services, and protect against security threats.
Allow secure outbound internet access for your users
You might need to create more Azure Firewall applications and network rules when you want to allow users outbound internet access.
If you have a well-defined list of allowed destinations, like Microsoft 365, use Azure Firewall application and network rules to route end-user traffic directly to the destinations. For information about the Office 365 IP address and URL web service, see the resources listed at the end of this module: you can refer to this link for the mandatory rules to allow outbound access to the control plane and core dependent services: https://learn.microsoft.com/en-us/azure/firewall/protect-azure-virtual-desktop?tabs=azure#host-pool-outbound-access-to-azure-virtual-desktop
Configure Azure Bastion and just-in-time (JIT) for administrative access to AVD session hosts.
Prerequisites:
- An Azure subscription.
- An Azure Administrator account with the necessary RBAC roles.
- An existing Azure Bastion host.
- An existing virtual network (VNet), and a subnet with an associated network security group (NSG).
- An existing virtual machine (VM), is connected to the above subnet.
- Defender for Servers Plan 2
To configure Azure Bastion and just-in-time (JIT) for administrative access to Azure Virtual Desktop (AVD) session hosts, you can follow these steps:
Set up JIT:
- On the Microsoft Defender for Cloud page (blade) select Workload protections.
- On the Defender for Cloud coverage page, scroll down to Advanced protection area, and select Just-in-time VM access.
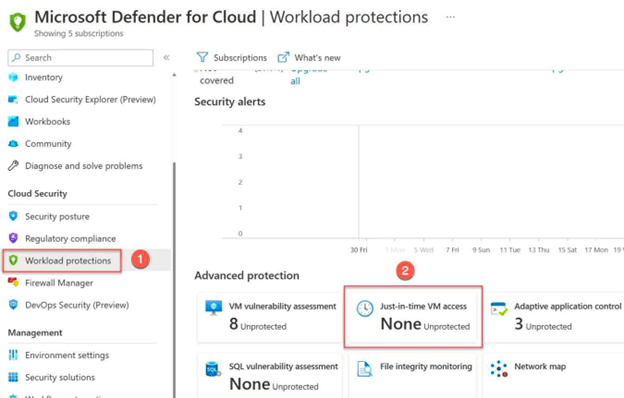
- On the Just-in-time VM access page click on the Not Configured tab
- Select the VM that you want to protect with JIT and click on the Enable JIT on VM button.

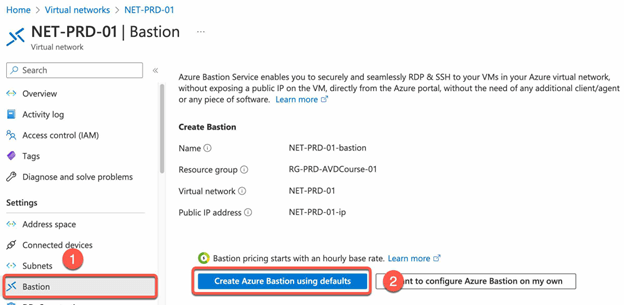
Set up Azure Bastion:
- Sign into the Azure portal.
- Go to your virtual network and select AVD VNET.
- On the page for your virtual network, in the left pane, select Bastion to open the Bastion page.
- On the Bastion page, select Create Azure bastion using defaults.
Assign the appropriate permissions:
- Required Permission:
- Reader role on the target VM.
- Reader role on the network interface (NIC) with private IP of the VM.
- Reader role on the Azure Bastion resource.
- Reader Role on the virtual network (VNet) of the target virtual machine
You can scope these roles at whatever level you want:
- Management Group
- Subscription
- Resource Group
- Resource
- Required inbound ports:
- For Windows VMs – RDP (3389)
- For Linux VMs – SSH (22)
Connect to the AVD session hosts:
- Connect to the AVD session hosts by navigating to the Azure portal, selecting the session host of from Azure virtual machine’s connect page,
- Click Connect and select RDP or SSH, depending on the type of VM (Windows or Linux) you want to connect to.

- On top of the Connect page, will explain that you need to select Request access before connecting.
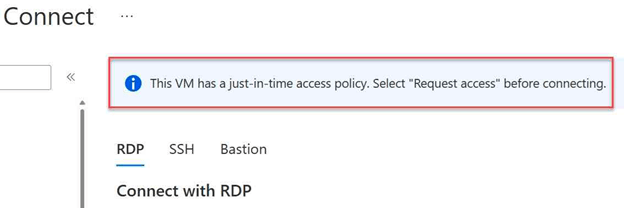
- To do so, scroll down and click on Request access.
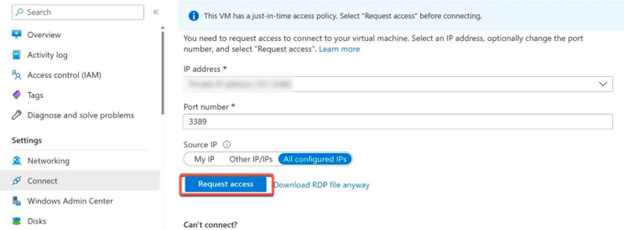
- You will be prompted to request access and provide a reason for the connection.
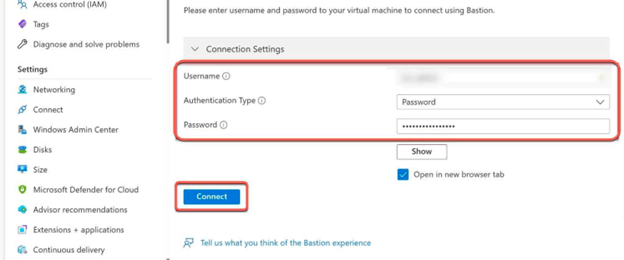
- After the request is approved for the VM (which can take up to around one minute), click on the Bastion tab.
- Then Click Use Bastion.
- On the Bastion page, enter the required authentication credentials, and then click Connect.
- To monitor and manage your JIT-enabled Bastion session, you can go to your Azure Bastion resource and select Sessions from the Azure Bastion page.
By following these steps, you can configure Azure Bastion and JIT for administrative access to AVD session hosts, allowing authorized users to remotely manage and troubleshoot the virtual desktop resources. This can help improve the security and efficiency of your AVD environment.
Azure Policies for Azure Virtual Desktop
To use Azure Policy built-in definitions to configure the diagnostics settings for Azure Virtual Desktop (AVD) resources like workspaces, application groups, and host pools, you can follow these steps:
Set up Azure Policy:
- Go to the Azure portal and navigate to the “Azure Policy” service.
- Select “Definitions” and search for the desired diagnostics policy (e.g. “MFA should be enabled for accounts with write permissions on your subscription”).
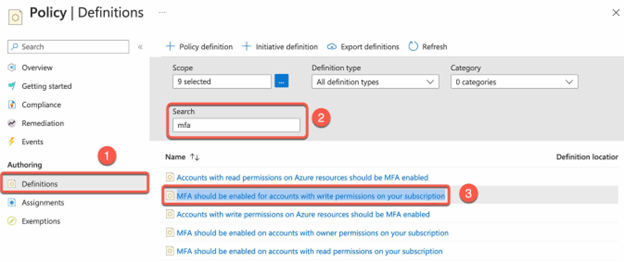
- Click on the policy and choose “Assign”.
Configure the policy:
- In the “Assign policy” blade, select the target the scope (e.g. a specific subscription or a specific resource group).
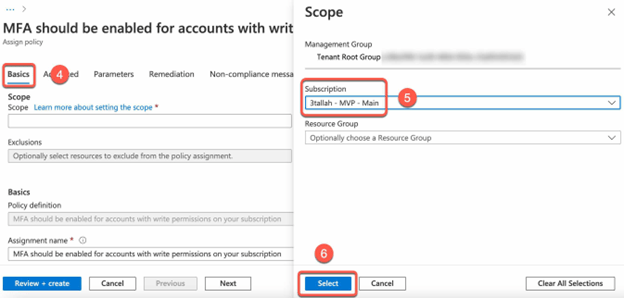
- In the Remediation tab create or select existing Managed Identity.
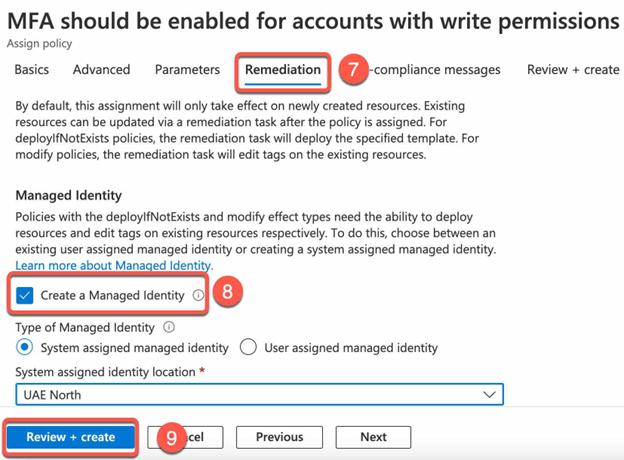
- Review and Create
Test the policy:
- Go to Azure Policy Compliance blade and check if any created policy Non-compliant
- Click on the policy to run the remediation.
By following these steps, you can use Azure Policy built-in definitions to configure the diagnostics settings for AVD resources. This can help to improve the monitoring and troubleshooting of your virtual desktop environment by ensuring that the appropriate diagnostics data is collected and stored. You can use the Azure Policy service to automate the configuration of the diagnostics settings and ensure that they are consistently applied across your AVD resources.
List of Azure Policies for AVD
Here is a table of some Azure policies that can be applied to Azure Virtual Desktop (AVD):
| Policy name | Description | |
| Enable MFA | Accounts with write permissions on Azure resources should be MFA enabled | |
| Restrict public IPs for AVD hosts | AVD host network interfaces should not have public Ips,This can help to prevent unauthorized access and protect against security threats. | |
| Require AVD session host tags | Requires that all AVD session host resources, such as session hosts and host pools, have specific tags applied to them. This can help to ensure that the resources are properly classified and managed. | |
| Enable endpoint protection | Install Endpoint Protection installed on all AVD session host resources, such as session hosts, DCs and Azure VMs for AVD Apps. | |
| Enforce AVD network, security groups | Enforces the use of network security groups (NSGs) on AVD resources to control inbound and outbound network traffic. This can help to prevent unauthorized access and protect against security threats. | |
| Enforce AVD encryption | Enforces the use of encryption on AVD resources, such as session hosts and data disks to protect sensitive data. This can help to meet compliance requirements and prevent data leaks. | |
| Require AVD security updates | Requires the application of security updates on AVD resources, such as session hosts, to keep the resources up-to-date and protect against security vulnerabilities. | |
| Block AVD resource deletion | Blocks the deletion of AVD resources, such as session hosts and host pools, unless they meet specific criteria. This can help to prevent the accidental or unauthorized deletion of resources and ensure that they are properly managed. | |
By implementing these Azure policies, you can improve the security, compliance, and management of your AVD environment. You can use the policies to enforce organizational policies, prevent unauthorized access and resource deletion, and ensure that your AVD resources meet the required standards.
Microsoft Defender for Cloud for Azure Virtual Desktop
To use Microsoft Defender for Cloud to apply extra compliance standards to Azure Virtual Desktop (AVD), you can follow these steps:
- Enable Microsoft Defender for Cloud for AVD:
- Sign into the Azure portal.
- Search for and select Microsoft Defender for Cloud.
- In the Defender for Cloud menu, select Environment settings.
- Select the subscription or workspace that you want to protect.
- Select Enable all to enable all of the plans for Defender for Cloud, or enable Defender plan for Servers Only.
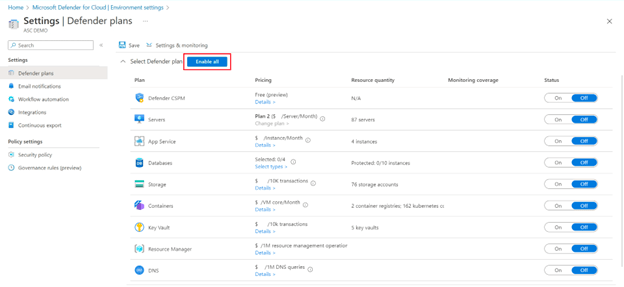
- Select Save.
If you want to disable any of the plans, turn the plan off. The extensions used by the plan are not uninstalled but, after a short time, the extensions stop collecting data.
By following these steps, you can use Microsoft Defender for Cloud to apply extra compliance standards to AVD. Microsoft Defender for Cloud can help to ensure that your virtual desktop environment meets various compliance requirements, such as those related to security, data protection, and governance. This can be particularly useful for meeting regulatory requirements or for demonstrating compliance to customers or partners.
Microsoft Defender Secure Score for AVD
To improve the Microsoft Defender Secure Score for Azure Virtual Desktop (AVD), you can follow these steps:
Set up Microsoft Defender for Cloud:
- Go to the Azure portal and navigate to the “Microsoft Defender for Cloud” service.
- Follow the prompts to set up Microsoft Defender for Cloud, including configuring the desired policies and settings.
Review the Secure Score:
- Navigate to the “Security posture” blade.
- Review “Secure Score” per environment like Azure, AWS and GCP.
- Validate the unhealthy resources.
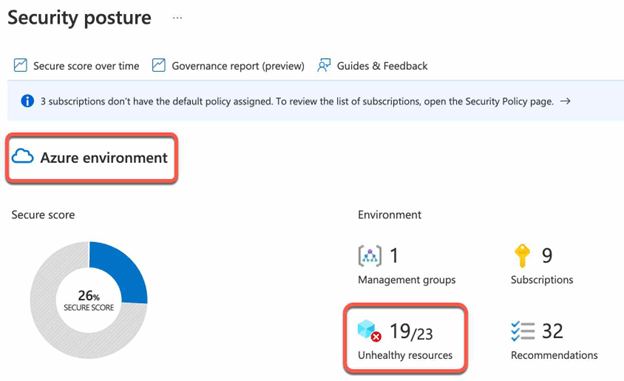
Review the Secure Score recommendations:
- Click on the “Recommendations” tab to see a list of recommendations for improving the Secure Score.

- Review the recommendations and consider implementing them to improve the Secure Score.
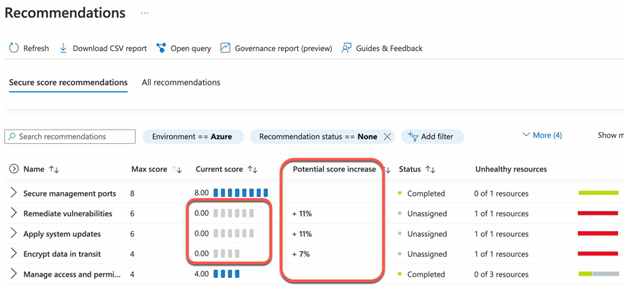
By following these steps, you can improve the Microsoft Defender Secure Score for AVD. The Secure Score is a composite score that reflects the security posture of your AVD environment, taking into account various factors such as identity protection, data protection, device security, and more. By implementing the Secure Score recommendations, you can help to improve the overall security posture of your AVD environment and increase the Secure Score.
Defender recommendations for AVD host sessions
Here is a table of some recommendations for Microsoft Defender for Cloud that can be applied to Azure Virtual Desktop (AVD) host sessions:
| Recommendation | Description |
| Compute | Recommendations to Protect the data on your Azure virtual machines with Azure Backup, and remediate vulnerabilities in security configuration on machines to protect them from attacks. |
| Security posture | Recommendations for improving the overall security posture of AVD host sessions, such as enabling additional security features, configuring security policies, and applying software updates. |
| Network security | Recommendations for improving the network security of AVD host sessions, such as configuring network security groups, enabling firewall rules, and implementing virtual private networks (VPNs). |
| Application security | Recommendations for improving the application security of AVD host sessions, such as configuring application control policies, enabling application whitelisting, and disabling unwanted applications. |
| Data security | Recommendations for improving the data security of AVD host sessions, such as enabling data encryption, configuring data access controls, and implementing data backup and recovery strategies. |
| Compliance and governance | Recommendations for improving the compliance and governance of AVD host sessions, such as configuring auditing and monitoring settings, applying compliance standards, and implementing governance policies. |
For the lists the recommendations you might see in Microsoft Defender for Cloud check this link: https://learn.microsoft.com/en-us/azure/defender-for-cloud/recommendations-reference
Compliance standards for Azure Virtual Desktop
There are many compliance standards that can be applied to Azure Virtual Desktop (AVD). Here is a table of some examples:
| Compliance standard | Description |
| ISO 27001 | International standard for information security management, covering the security of information assets such as financial data, intellectual property, and personal data. |
| PCI DSS | Payment Card Industry Data Security Standard, covering the security of cardholder data and the requirements for merchants and service providers to accept and process payment card transactions. |
| HIPAA | Health Insurance Portability and Accountability Act, covering the protection of sensitive medical information. |
| NIST Cybersecurity Framework (CSF) | National Institute of Standards and Technology Cybersecurity Framework, covering the management of cybersecurity risk in the context of an organization’s risk management strategy. |
| SOC TSP | SOC 2 Reporting and the Trust Services Principles (TSP). SOC 2 Type 2 Compliance entails the use of what’s known as the Trust Services Principles (TSP) – a set of professional attestation and advisory services containing essential criteria-based information for assessing service organizations. |
| Azure CIS | The CIS Microsoft Azure Foundations Benchmark is the security guidance provided by the Center for Internet Security for establishing a secure baseline configuration for Azure. The scope of the benchmark is to establish the foundation level of security while adopting Azure Cloud. |
| FedRAMP | Federal Risk and Authorization Management Program, covering the security requirements for cloud service providers serving the US federal government. |
By applying one of these compliance standards to AVD based on business needs, you can ensure that your AVD environment meets the requirements for data security, privacy, and compliance. This can help to protect sensitive information and meet the regulatory requirements of your industry or organization.
For the full list of compliance standards are available in Defender for Cloud check this link: https://learn.microsoft.com/en-us/azure/defender-for-cloud/update-regulatory-compliance-packages#what-regulatory-compliance-standards-are-available-in-defender-for-cloud
Session host Security Configuration for AVD
Prevent unwanted software from running on session hosts using GPO.
To prevent unwanted software from running on session hosts, you can follow these steps:
Set up Group Policy:
- Open the Group Policy Management Console on a domain controller.
- Create a new GPO and link it to the organizational unit (OU) or domain containing the session hosts.
Configure software restrictions:
- In the GPO, go to “Computer Configuration > Policies > Security Settings > Software Restriction Policies”.
- Create a new software restriction policy.
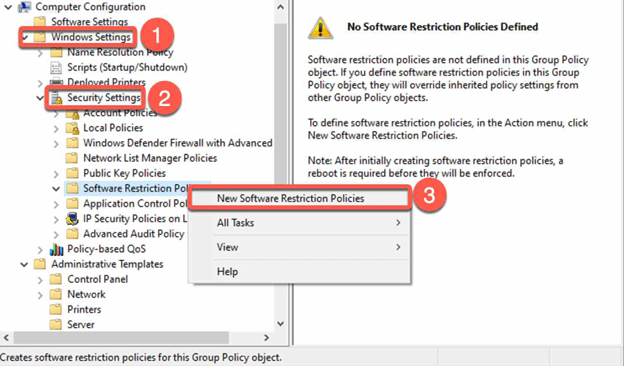
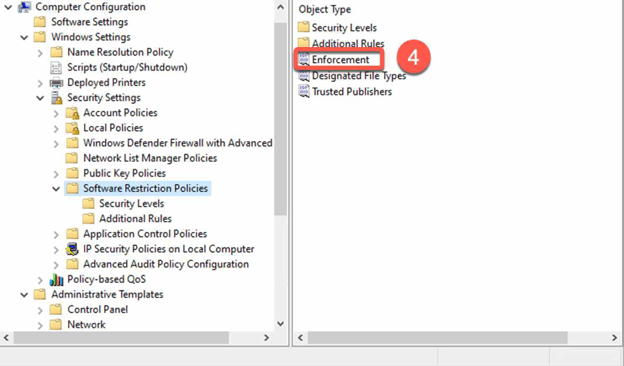
- Once the software restriction policy is created, notice you have now a couple of new GPO folders and options.
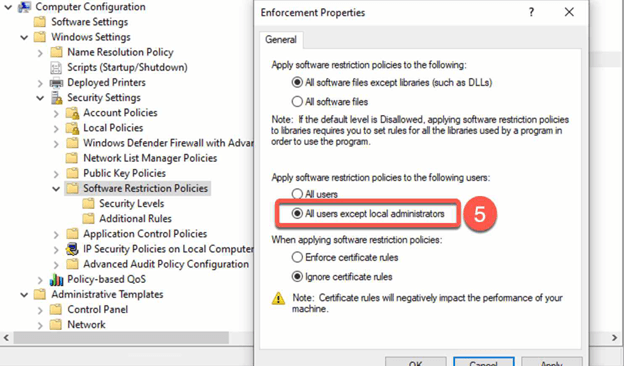
- Edit the Enforcement GPO Option to grant administrator privileges while restricting non-admin users from running unauthorized software. Simply right-click on Enforcement and choose Properties, then follow the steps outlined in the provided screenshot for optimal results.
- Configure the desired settings (e.g. “Disallowed” rule for specific executables or “Unrestricted” rule for trusted locations).
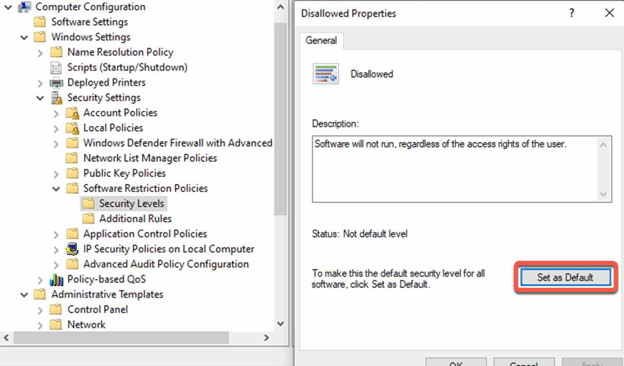
Test the policy:
- Log in to a session host as a user who is subject to the policy.
- Attempt to run unwanted software and verify that it is blocked as expected.
By following these steps, you can prevent unwanted software from running on session hosts, helping to improve the security and stability of your environment. This can be particularly useful for preventing malware or unauthorized software from running on the session hosts.
Deploy the Trusted Launch to the Azure VM (AVD session host)
Here is a PowerShell script that you can use Deploy the Trusted Launch on Azure Virtual Desktop (AVD) session hosts:

By following these steps, you can enable Trusted Launch for AVD session hosts, helping to improve the security of your virtual desktop environment. Trusted Launch helps to Securely deploy virtual machines with verified boot loaders, OS kernels, and drivers, securely protect keys, certificates, and secrets in the virtual machines, Gain insights and confidence of the entire boot chain’s integrity and Ensure workloads are trusted and verifiable.
Install and enable Defender on AVD using PowerShell script.
Here is a PowerShell script that you can use to enable and install Microsoft Defender for Cloud on Azure Virtual Desktop (AVD) session hosts:
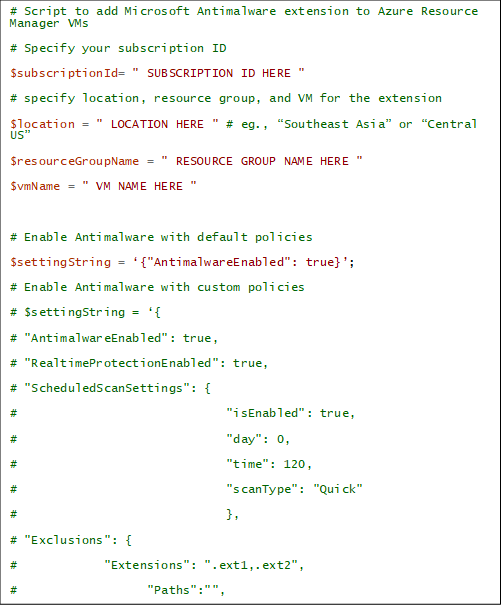
To use this script, you will need to replace the following placeholders with your own values:
- $subscriptionId: The ID of the Azure subscription containing the AVD resources.
- $resourceGroupName: The name of the resource group containing the AVD resources.
- $location: # eg., “Southeast Asia” or “Central US”
- $vmName: Session host or VM Name
- $settingString = ‘{“AntimalwareEnabled”: true}: # Enable Antimalware with default policies
Apply OS and application updates to an image
To apply OS and application updates to an image, you can follow these steps:
- Create a base image:
- Install the desired operating system and applications on a virtual machine or physical computer.
- Configure the image as desired, such as setting up user accounts and installing any necessary drivers.
- Create a snapshot or backup of the base image:
- Take a snapshot or create a backup of the base image, so that you have a copy of the original image in case something goes wrong during the update process.
- Install updates:
- Connect to the base image and install any available OS and application updates.
- You can use Windows Update or other update tools (e.g. Windows Server Update Services) to install updates.
- Test the updates:
- Test the updated image to ensure that all updates have been installed correctly and that the image is functioning as expected.
- Capture the updated image:
- If the updates were installed successfully and the image is functioning as expected, capture the updated image.
- You can use tools such as Sysprep or ImageX to capture the image.
- Store the image in Azure Compute Gallery:
- For Gallery details, select the gallery or create a new gallery by selecting Create new.
- In Operating system state select generalized or specialized.
- Select an image definition or select create new and provide a name and information
- Enter an image version number. If this is the first version of this image, type 1.0.0.
By following these steps, you can apply OS and application updates to an image, ensuring that the image is up to date and fully patched. This can help ensure that the image is secure and reliable when deployed in production.
Monitoring best practices for AVD
Azure Monitor and Log Analytics for Azure Virtual Desktop
Azure Monitor and Log Analytics are tools that can be used to monitor and troubleshoot Azure Virtual Desktop (AVD) environments.
Azure Monitor is a service that provides real-time monitoring and alerting for Azure resources. It allows administrators to view metrics, logs, and alerts for AVD resources, as well as set up custom alerts and notifications based on specific conditions.
Log Analytics is a service that enables administrators to collect and analyze log data from AVD resources and other Azure services. It provides a searchable repository of data that can be used to identify trends, detect issues, and generate reports.
Together, Azure Monitor and Log Analytics provide a powerful toolset for monitoring and troubleshooting AVD environments. They can be used to identify performance issues, track resource usage, and detect security threats, among other things.
To use Azure Monitor and Log Analytics for AVD, administrators can:
- Enable monitoring for AVD resources, such as virtual machines and session host pools, using Azure Monitor.
- Configure Azure Monitor to collect logs and metrics from AVD resources and send them to Log Analytics.
- Use Log Analytics to search and analyze log data, create custom queries and reports, and set up alerts and notifications.
By using Azure Monitor and Log Analytics for AVD, administrators can gain visibility into the performance and health of their virtual desktop environment and proactively identify and resolve issues.
Create Log analytics and enable AVD insights to collect the logs
To create a Log Analytics workspace and enable AVD insights to collect the logs, you can follow these steps:
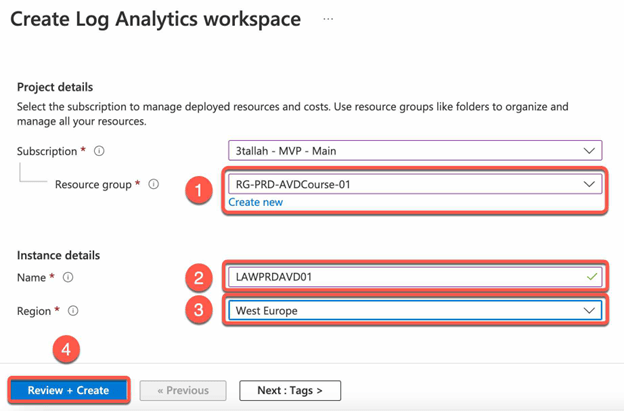
Create a Log Analytics workspace:
- Go to the Azure portal and navigate to the “Log Analytics workspaces” service.
- Click on the “Create” button to create a new Log Analytics workspace.
- Follow the prompts to create the workspace, including selecting a resource group, location, and pricing tier.
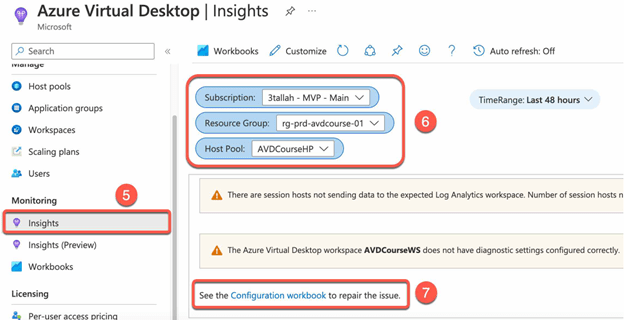
Enable AVD insights:
- Go to the Azure portal and navigate to the Azure Virtual Desktop.
- Click on Insights.
- Select the target Subsection, Resource Group and host pool.
- Then Click on configuration workbook.
- On the diagnostic settings for host pool Choose the Log Analytics workspace that you created in the previous step and click Configure host pool
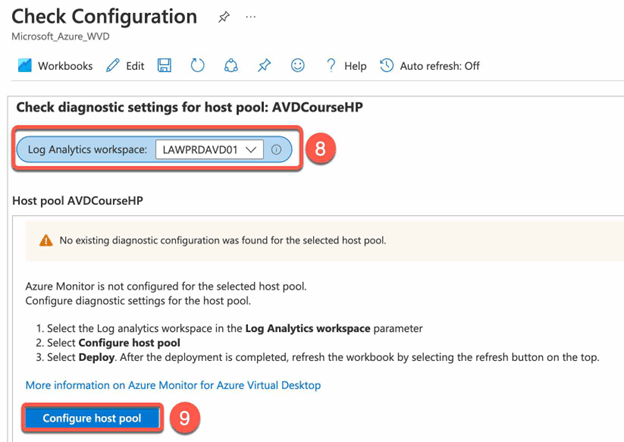
- In Deploy Template Blade click Deploy
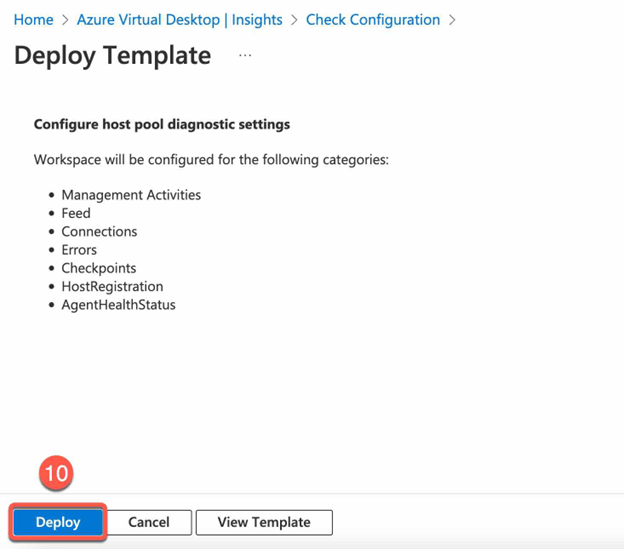
- Back to diagnostic settings for host pool and click in the Workspace Section click configure Log Analytics workspace for the selected workspace.
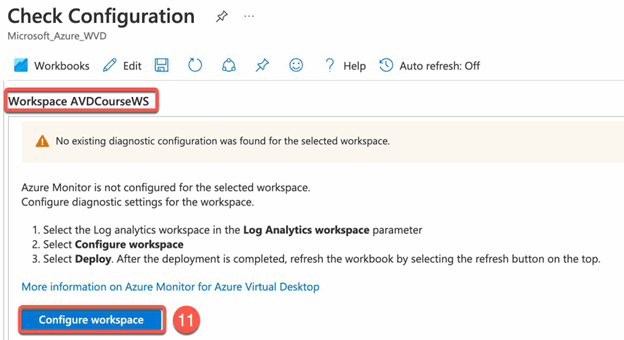
- In Deploy Template Blade click Deploy
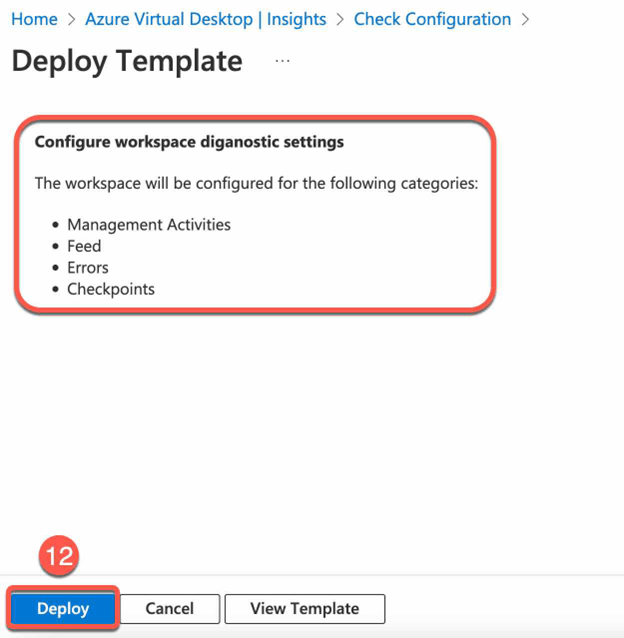
Review Azure Virtual Desktop Insights:
- Go to the Azure portal and navigate to Azure Virtual Desktop
- Select “Insights (Preview)” from the menu on the left.
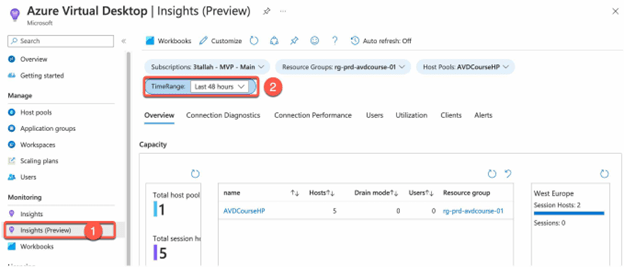
- As shown in the above screenshot session and user logs and data start showing up on the insights page, where you can utilize that info for your monitoring and troubleshooting.
Review the collected logs:
- Go to the Azure portal and navigate to the Log Analytics workspace.
- Select “Logs” from the menu on the left.
- Use the search bar to search for the collected logs (e.g. “WVDFeeds”, “WVDConnections” or “WVDSessionHostManagement”).
- Review the logs to see the collected data.
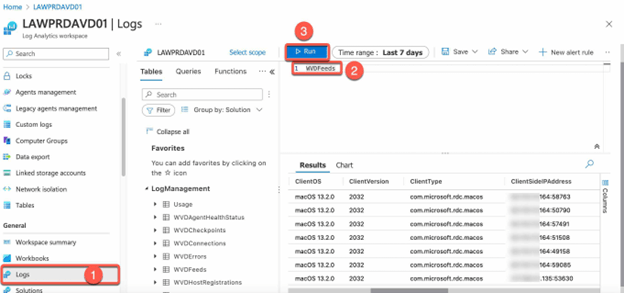
Here are some additional points for advanced configuration of AVD insights:
- Configure custom logs: You can configure AVD insights to collect custom logs by creating custom log queries in the Log Analytics workspace. This can be useful for collecting specific data or for analysing data that is not included in the default AVD logs.
- Configure alerts: You can use the collected logs to create alerts in the Log Analytics workspace. For example, you can create an alert that triggers when a specific error is logged, or when a certain threshold is reached (e.g. number of failed connections).
- Use Power BI integration: You can use the Power BI integration to visualize the collected logs in a more interactive and user-friendly way. This can be useful for presenting the data to stakeholders or for identifying trends and patterns in the data.
- Use Azure Monitor integration: You can use the Azure Monitor integration to use the collected logs as the data source for Azure Monitor alerts and dashboards. This can be useful for monitoring the health and performance of your AVD environment in real-time.
By configuring these advanced features, you can improve the capabilities and usefulness of AVD insights for monitoring and analyzing your AVD environment. These features can help you to better understand the usage patterns and performance of your AVD environment, as well as to identify and respond to potential issues or problems.
Table for audit logs for AVD that we can collect.
Here is a table of all the audit logs that can be collected for Azure Virtual Desktop (AVD):
| Log name | Description |
| WVDConnections | Records information about user connections to AVD, including the user’s identity, the connection method, and the session ID. |
| WVDSessionHostManagement | Windows Virtual Desktop session host management data, The source for the Azure virtual machine – either Marketplace or Custom, The desired Azure virtual machine size (e.g.: Standard_D2s_v4) after the host pool update. |
| WVDAgentHealthStatus | Azure Virtual Desktop agent health status data like The number of disconnected, or logged off sessions on the VM, The version of the WVD Agent running on the Virtual Machine |
| WVDErrors | Windows Virtual Desktop Error Activity, like the user for which the error happened, The source of the error. |
| WVDFeeds | Windows Virtual Desktop Feed Activity, like the remote IP address from the client side, Client Type, Client Version |
| WVDManagement | Windows Virtual Desktop Management Activity, like the user that initiated the management request and the remote IP address from the client side. |
| WVDHostRegistrations | Windows Virtual Desktop Host Registration Activity, like the name and IP address of the session host that was registered with the WVD service. |
Create alerts for Azure Virtual Desktop
To create and configure alerts for Azure Virtual Desktop (AVD), you can follow these steps:
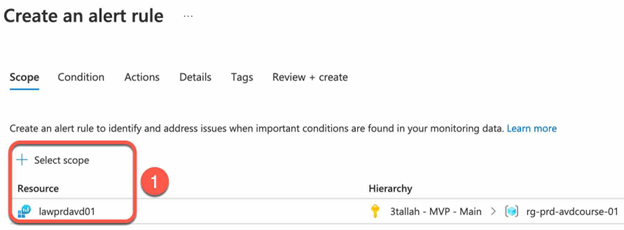
Create an alert:
- Go to the Azure portal and navigate to the “Alerts” service.
- Select “Alert rules” and create a new alert rule.
- Select the Scope
- Configure the alert rule to trigger when certain conditions are met (e.g. when a session host goes offline or experiences a problem is detected).
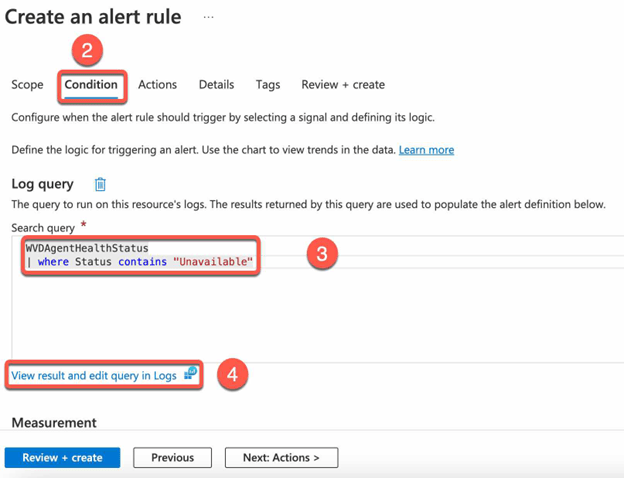
- Validate the query result

- Choose the desired actions for the alert, such as sending an email or triggering an Azure Automation runbook.
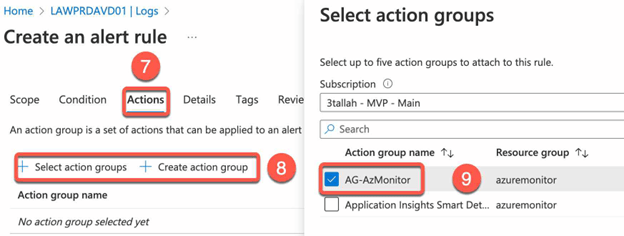
Test the alerts:
- Log in to an AVD session as a user and trigger a alerts condition (e.g. powering off the host).
- Verify that the alert is triggered, and the desired actions are taken.
By following these steps, you can configure alerts and automated responses in Microsoft azure to ensure the overall compliance of AVD.
Alerts list ideas that can be applied on your Azure Virtual Desktop environment
There are many alerts that can be applied to Azure Virtual Desktop (AVD) to monitor the health and performance of your environment. Here is a table of some examples:
| Alert type | Description | |
| Session host status | Triggers an alert when a session host goes offline or experiences a problem. | |
| User connection | Triggers an alert when a user experiences a problem connecting to an AVD session, such as a failed login attempt. | |
| Resource usage | Triggers an alert when a resource, such as CPU or memory, reaches a certain threshold. | |
| Application usage | Triggers an alert when an application is used in an unusual way, such as a sudden increase in usage or an unusual error. | |
| Security breach | Triggers an alert when a security breach is detected, such as unauthorized access to an AVD resource. | |
| Compliance violation | Triggers an alert when a compliance violation is detected, such as the unauthorized access of sensitive data. | |
| System update failure | Triggers an alert when a system update fails, indicating that the update may need to be reattempted. | |
| Performance degradation | Triggers an alert when the performance of an AVD resource, such as a session host, begins to degrade. | |
| Application error | Triggers an alert when an application error is detected, indicating that the application may need to be troubleshooted. | |
| Network connectivity issue | Triggers an alert when a network connectivity issue is detected, indicating that users may be unable to connect to AVD sessions. | |
| Resource exhaustion | Triggers an alert when a resource, such as CPU or memory, becomes exhausted, indicating that additional resources may be needed. | |
| User session termination | Triggers an alert when a user session is terminated, indicating that the session may need to be investigated. | |
| Resource quota exceeded | Triggers an alert when a resource quota is exceeded, indicating that additional resources may be needed. | |
By configuring these additional alerts, you can further enhance the monitoring and management of your AVD environment. You can use the alerts to identify and respond to potential issues or problems, ensuring that your AVD environment is operating smoothly and efficiently. You can also use the alerts to meet compliance requirements, such as by triggering an alert when a security breach is detected.
Azure Sentinel for Azure Virtual Desktop
Azure Sentinel is a cloud-native, security information and event management (SIEM) platform that helps organizations detect and respond to threats in real-time. It can be used to monitor and protect Azure Virtual Desktop (AVD) environments by collecting, analyzing, and storing data from a variety of sources, including logs from AVD resources, Azure AD, and Azure Defender.
Some of the key benefits of using Azure Sentinel for AVD include:
- Real-time threat detection: Azure Sentinel uses machine learning algorithms to analyze data in real-time and alert administrators of potential threats.
- Centralized log management: Azure Sentinel provides a single view of all logs generated by AVD resources, making it easier for administrators to track and analyze security events.
- Integration with other Azure services: Azure Sentinel can be integrated with other Azure security services, such as Azure Defender and Azure AD, to provide a comprehensive view of the security posture of an AVD environment.
- Automated response: Azure Sentinel can be configured to automatically take actions, such as blocking access or quarantining resources, in response to detected threats.
Connect Azure Virtual Desktop data to Microsoft Sentinel
| Data Type | Action |
| Windows event logs | To stream Windows event logs from the Azure Virtual Desktop environment into a Microsoft Sentinel-enabled Log Analytics workspace, install the Log Analytics agent on your Windows machine and set it up to send the Windows event logs to the workspace. This process is similar to how event logs from other Windows machines are sent to Log Analytics workspaces. You can refer to the previous section on how to collect your AVD Log using LAW |
| Microsoft Defender for Endpoint alerts | The procedure for setting up Defender for Endpoint on an Azure Virtual Desktop is the same as for any other Windows endpoint. For additional guidance, refer to the resources on setting up a Microsoft Defender for Endpoint deployment and connecting data from Microsoft 365 Defender to Microsoft Sentinel. – Set up Microsoft Defender for Endpoint deployment |
| Azure Virtual Desktop diagnostics | Azure Virtual Desktop diagnostics is a built-in feature that logs activity when an individual with an assigned Azure Virtual Desktop role uses the service. These logs include information about the Azure Virtual Desktop role involved in the activity, error messages that occurred during the session, tenant and user details. The diagnostics feature also logs both user and administrative actions. |
Connect Azure Virtual Desktop data
To push Azure Virtual Desktop data into Microsoft Sentinel, follow the guidance provided in the earlier section (Create Log analytics and enable AVD insights to collect the logs).





