Introduction
Welcome to our comprehensive series on Azure Web Application Firewall (WAF) security! In this final installment, we’ll be diving deep into protecting against data exfiltration attempts. This hands-on tutorial is part of a four-part series designed to demonstrate Azure WAF’s capabilities in identifying and mitigating various cyber threats.
Series Overview
- Part 1: Lab Setup – Building Your Azure WAF Testing Environment
- Part 2: Reconnaissance Playbook – Testing Azure WAF Protection
- Part 3: Vulnerability Exploitation Playbook – Azure WAF vs XSS
- Part 4: Data Disclosure and Exfiltration Playbook (This post)
What You’ll Learn
In this tutorial, you’ll:
- Simulate a SQL Injection (SQLi) attack against an OWASP Juice Shop application
- Compare application behavior with and without Azure WAF protection
- Analyze WAF logs using Azure Monitor Workbooks
Prerequisites
Before starting this tutorial, ensure you have:
- Completed the Azure WAF security lab setup
- Finished the previous tutorials in this series
- Familiarity with Burp Suite and Firefox (setup instructions provided)
Lab Scenario: Protecting Against SQL Injection
We’ll explore two scenarios:
- Direct attack on the vulnerable application
- Attack attempt through Azure WAF protection
Scenario 1: Direct SQLi Attack
- Access the Kali VM
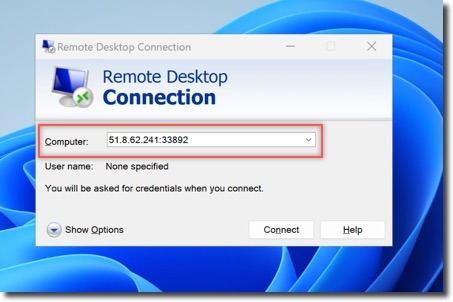
- Launch Burp Suite
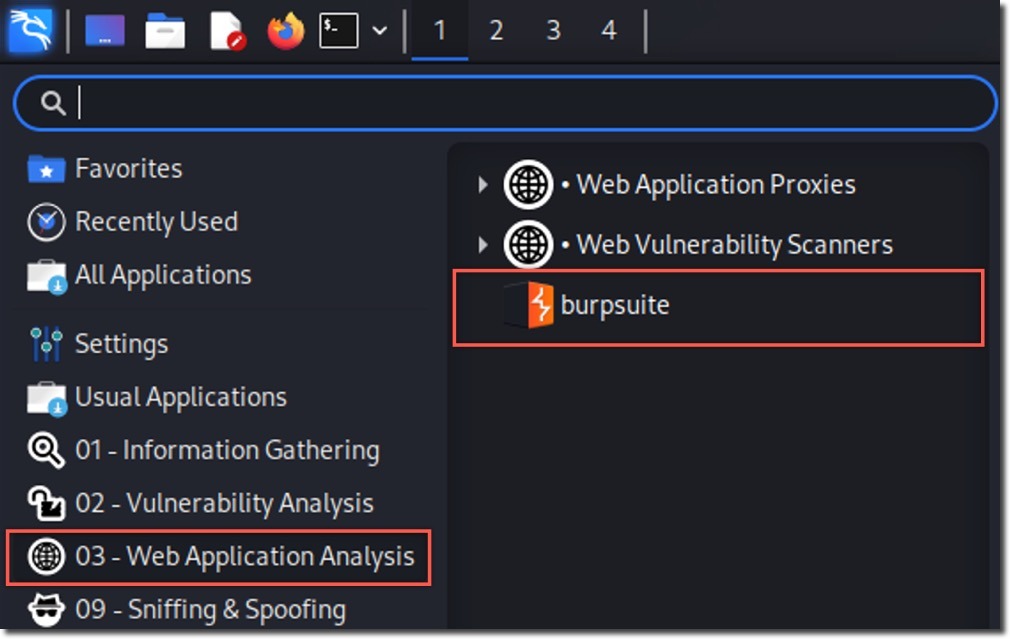
- Ensure you have Burp Suite configured and running as described in the Configuring Burp Suite and Firefox section of the Vulnerability Exploitation Playbook
- Browse to the Juice Shop application (http://owaspdirect-<deployment guid>.azurewebsites.net)
- In the search bar on the Juice Shop website, type “apple”
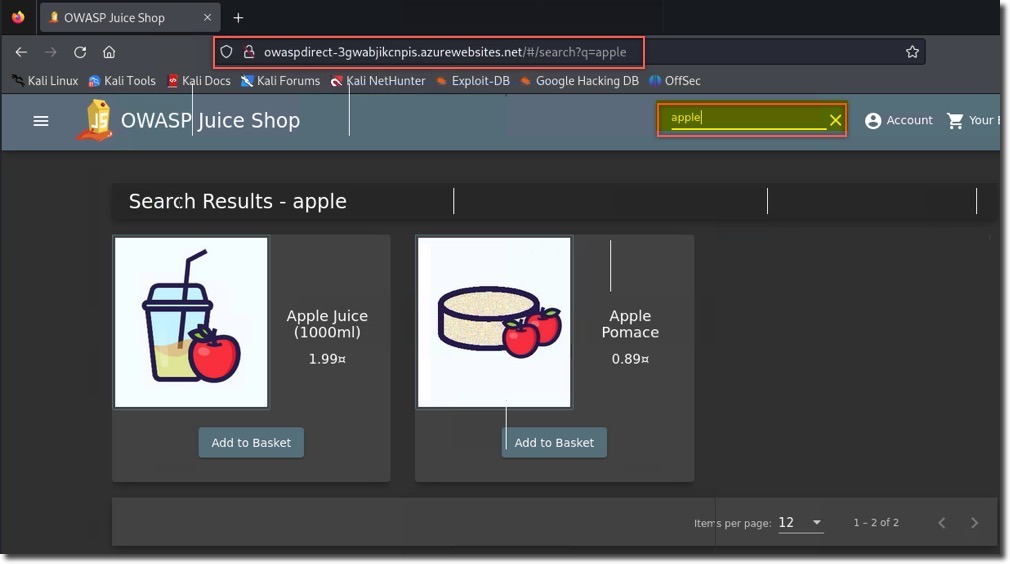
- In Burp Suite, check the Proxy –> HTTP history tab for the request and response data for this website
- Identify the vulnerable
/rest/products/searchendpoint 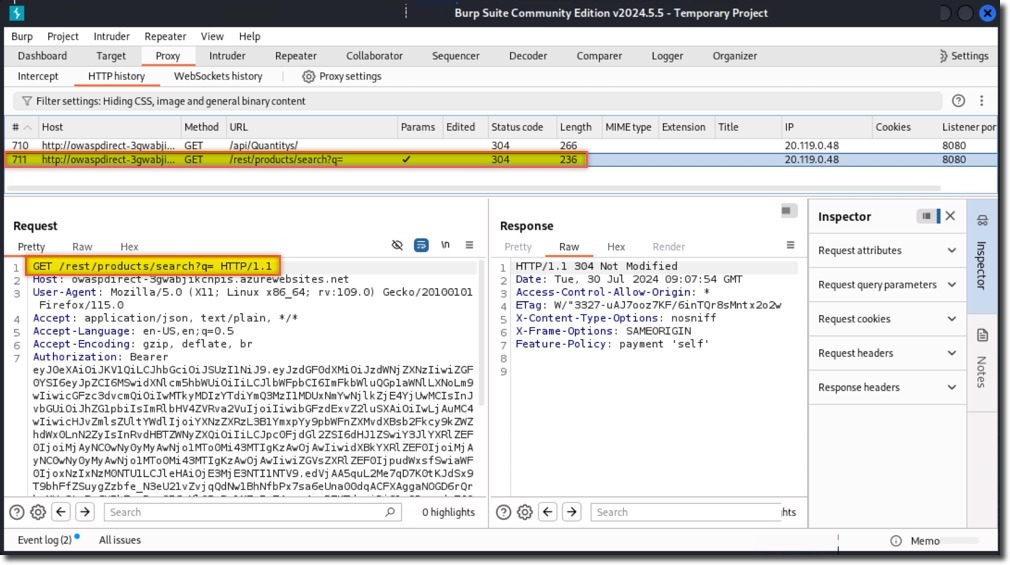
- The
/rest/products/searchendpoint of the OWASP Juice Shop application is vulnerable to SQL injection, we will be exploiting the SQLi vulnerability in this endpoint
- The
- Examine the request and response in Burp Suite
- Use Burp Suite’s Repeater to inject a malicious SQL query
- Right-click one of the GET requests to the
/rest/products/searchendpoint and then click Send to Repeater 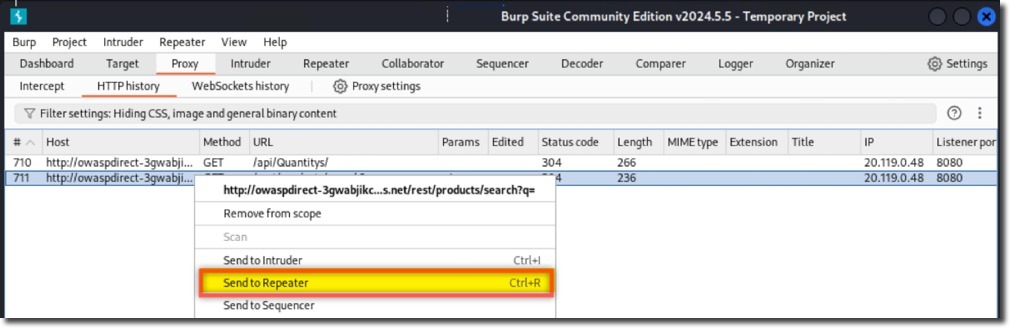
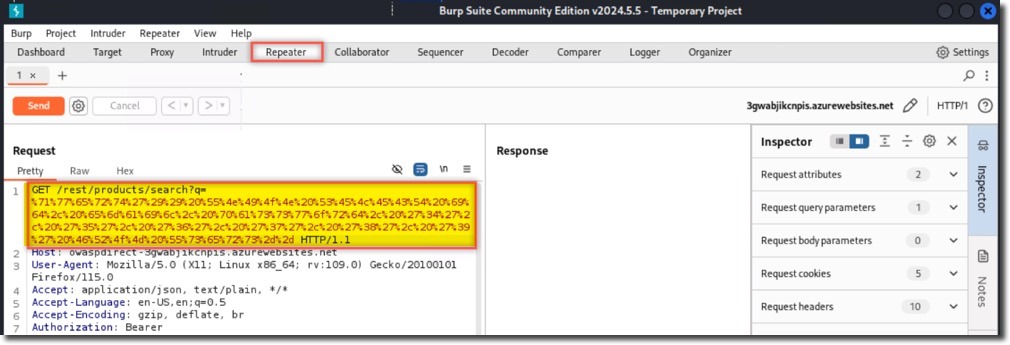
- In the Burp Repeater window. In the Request URI, locate the parameter /rest/products/search?q=. After the “=” sign, paste your encoded SQL query. This appends the query to the existing search parameter.
%71%77%65%72%74%27%29%29%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%69%64%2c%20%65%6d%61%69%6c%2c%20%70%61%73%73%77%6f%72%64%2c%20%27%34%27%2c%20%27%35%27%2c%20%27%36%27%2c%20%27%37%27%2c%20%27%38%27%2c%20%27%39%27%20%46%52%4f%4d%20%55%73%65%72%73%2d%2d
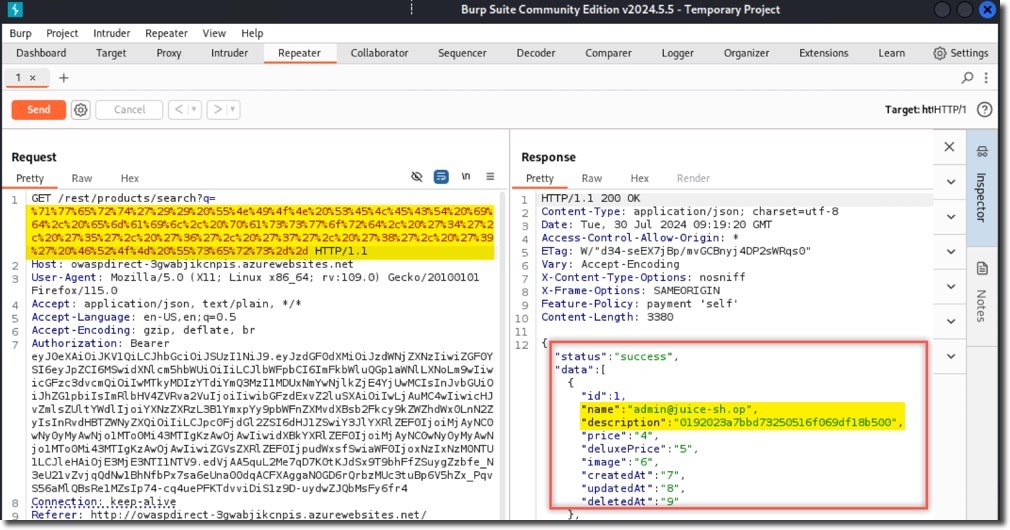
- After pasting your encoded SQL query into the search parameter, click the “Send” button to submit the request.
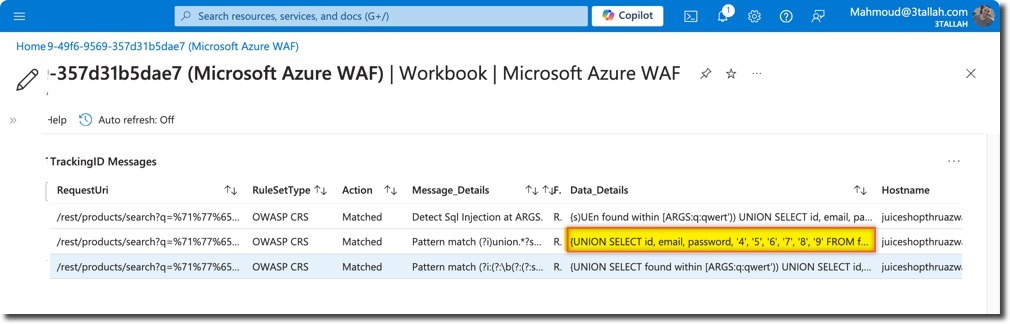
- Observe the successful data exfiltration
Scenario 2: SQLi Attack Through Azure WAF
- Launch a new Burp Suite instance
- Browse to the protected application (http://juiceshopthruazwaf.com)
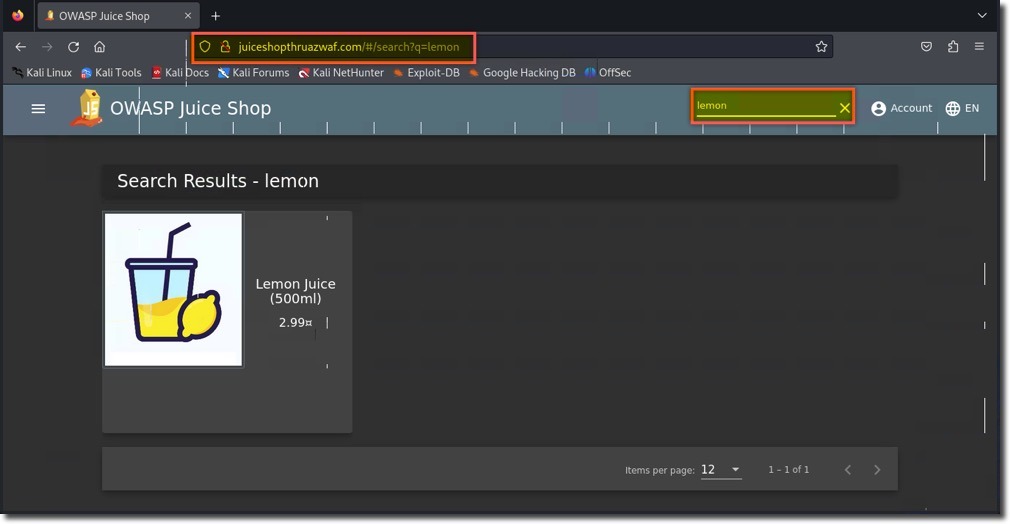
- Attempt the same SQL injection
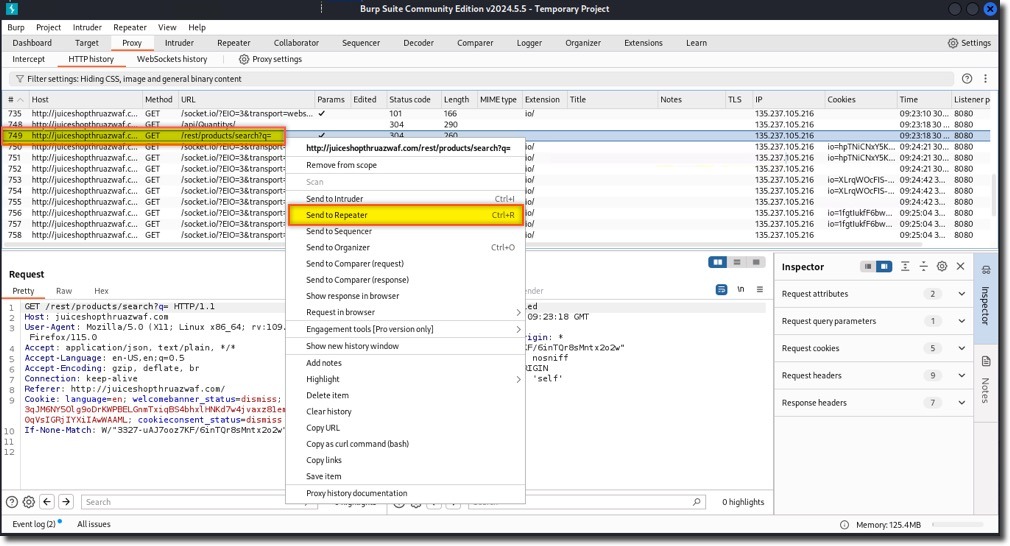
- Observe Azure WAF blocking the malicious request
Analyzing WAF Logs
We’ll use the Azure Monitor Workbook for WAF to gain insights:
- Access the WAF workbook in Azure Portal
- Set appropriate filters (time range, WAF type)
- Examine key sections:
- WAF actions
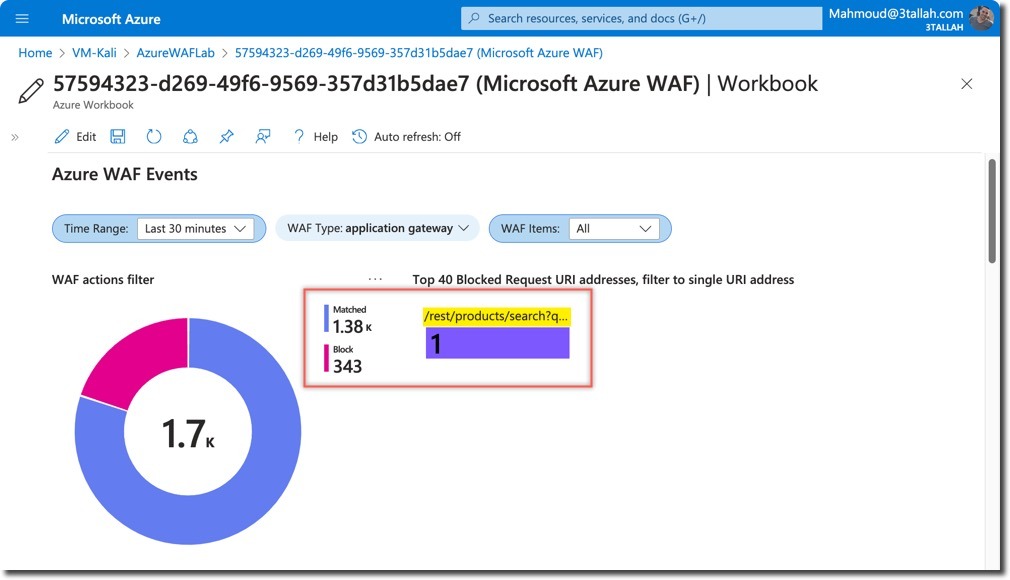
- Blocked Request URIs
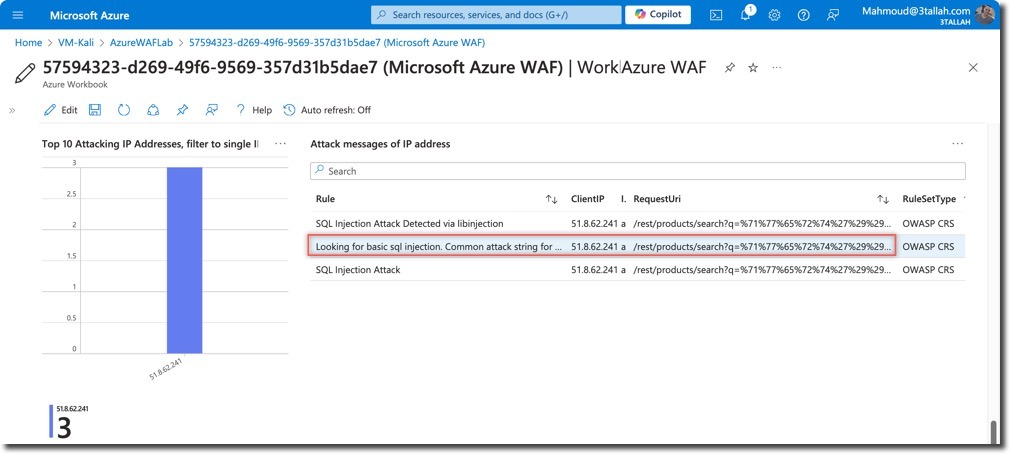
- Top event triggers
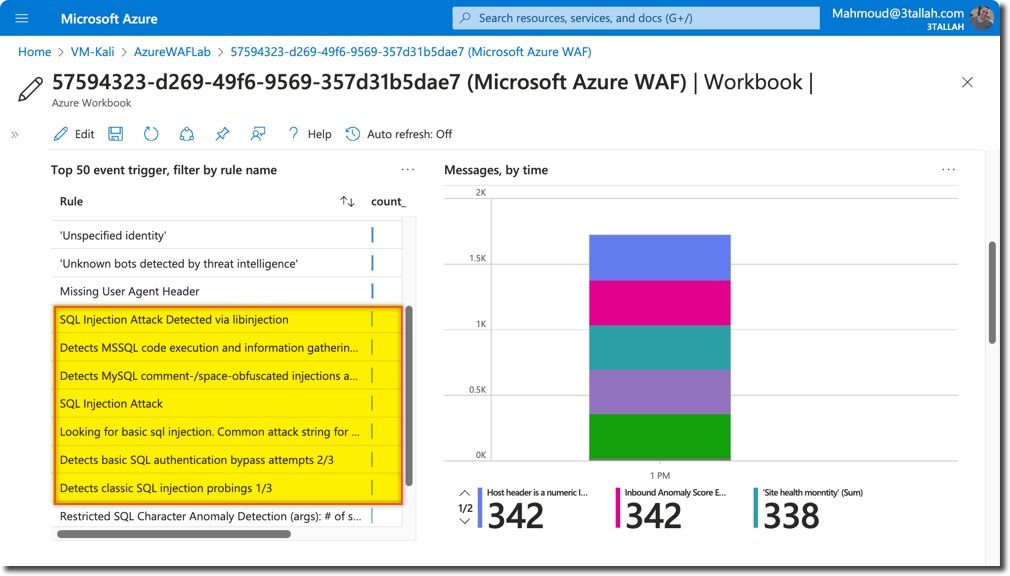
- Detailed messages
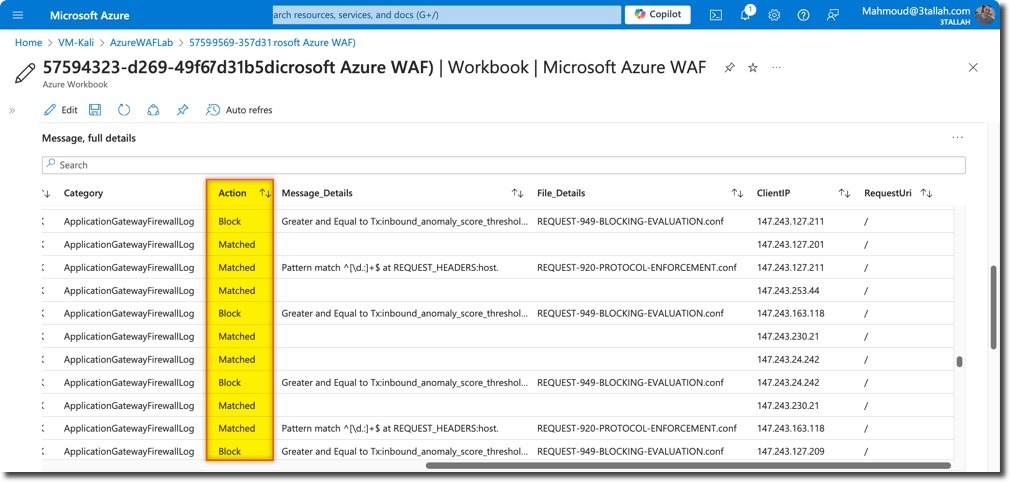
- WAF actions
Key Takeaways
- SQL Injection remains a critical web application vulnerability
- Azure WAF provides robust protection against SQLi attacks
- WAF can detect and block suspicious queries at the network edge
- Proper log analysis is crucial for understanding attack patterns
Next Steps
- Practice identifying other types of attacks in your lab
- Explore additional WAF configuration options for your specific use cases
By completing this series, you’ll have gained valuable hands-on experience in setting up, testing, and analyzing Azure WAF protection against various cyber threats.
Stay tuned for more in-depth Azure security tutorials and happy securing!