Introduction
In today’s digital landscape, protecting web applications from sophisticated attacks is crucial. Azure Web Application Firewall (WAF) offers robust security features, but many organizations want to validate its effectiveness before deploying it in mission-critical environments. That’s where our four-part Azure WAF Security Lab tutorial series comes in.
Series Overview
This in-depth tutorial series is designed to demonstrate Azure WAF’s capabilities in identifying, detecting, and protecting against suspicious activities and potential attacks on your web applications. By the end of this series, you’ll have hands-on experience with:
- Configuring a test environment with all necessary components
- Simulating different attacks on a vulnerable web application
- Analyzing Azure WAF’s detection and protection mechanisms
- Interpreting Azure Monitor Workbook for WAF to understand its processing logic
Let’s break down what each part of the series covers:
Part 1: Lab Setup – Building Your Azure WAF Testing Environment
In this crucial first step, we’ll guide you through:
- Lab Architecture Diagram
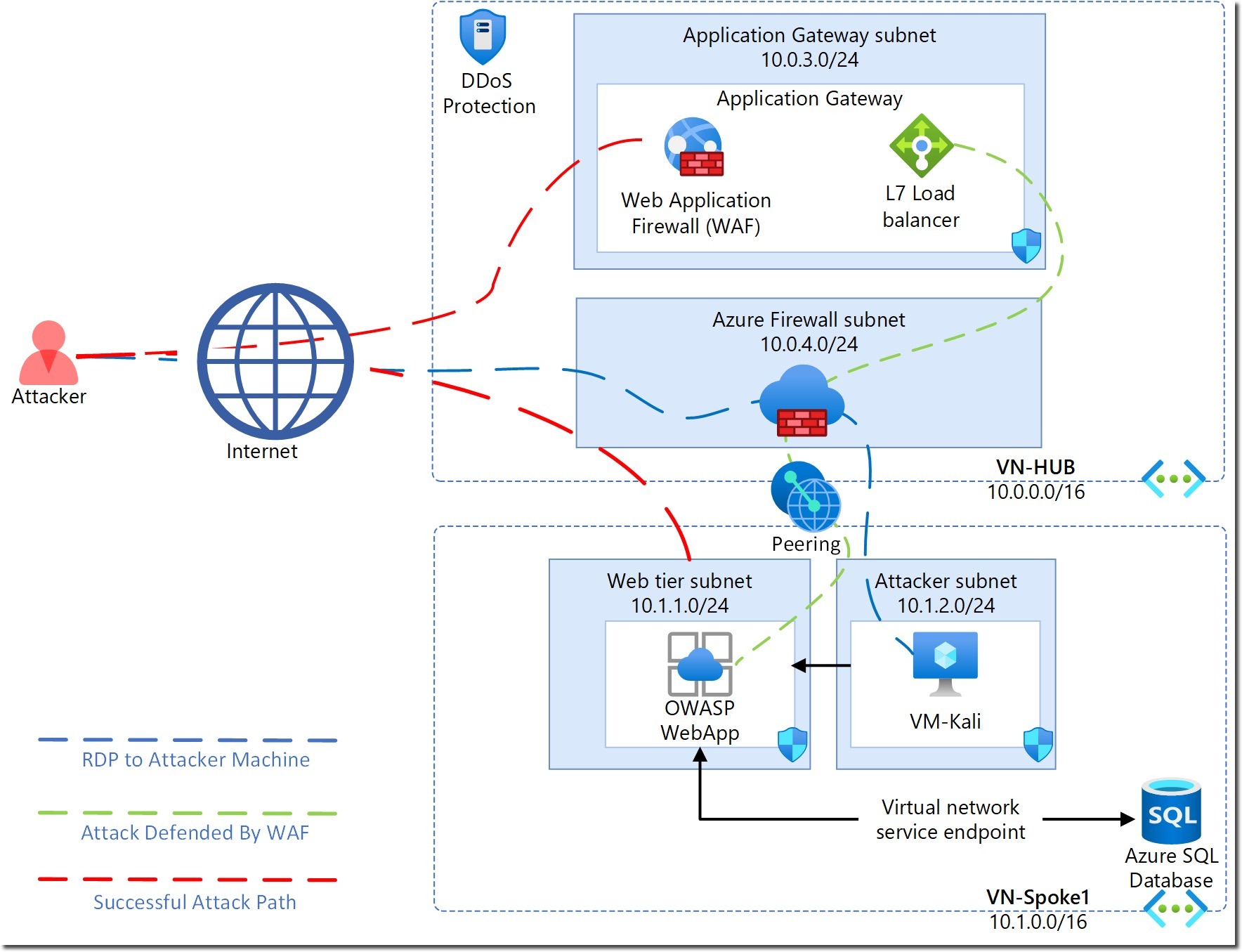
- Deploying all required Azure resources
- Setting up the vulnerable OWASP Juice Shop web application
- Configuring Azure WAF on Application Gateway
- Preparing your attack machine with the necessary tools
This comprehensive setup ensures you have a controlled environment that mimics real-world scenarios, allowing for accurate testing of Azure WAF’s capabilities.
Part 2: Reconnaissance Playbook – Mapping the Target
Reconnaissance is often the first step in an attacker’s playbook. In this section, we’ll:
- Demonstrate common recon techniques using publicly available tools
- Show how Azure WAF detects and responds to suspicious mapping activities
- Provide step-by-step instructions for simulating these attacks
- Analyze Azure WAF logs to understand its detection mechanisms
You’ll gain insights into how Azure WAF can thwart attempts to gather information about your web applications before an attack even begins.
Part 3: Vulnerability Exploitation Playbook – Cross-Site Scripting (XSS) Attacks
This section focuses on one of the most common web application vulnerabilities: Cross-Site Scripting (XSS). You’ll:
- Execute XSS exploits against the unprotected Juice Shop application
- Observe how Azure WAF detects and blocks these attacks
- Analyze WAF rules triggered by XSS attempts
- Interpret Azure Monitor Workbook data for deeper insights
By the end of this playbook, you’ll understand how Azure WAF serves as a crucial line of defense against XSS vulnerabilities.
Part 4: Data Disclosure and Exfiltration Playbook – SQL Injection (SQLi) Attacks
In the final part of our series, we’ll tackle SQL Injection (SQLi), a severe threat that can lead to unauthorized data access. This playbook will:
- Introduce SQLi concepts and attack techniques
- Guide you through executing SQLi attacks on the vulnerable application
- Demonstrate Azure WAF’s effectiveness in preventing data exfiltration
- Show you how to analyze WAF logs and Azure Monitor Workbook for SQLi attempts
- Discuss best practices for configuring WAF rules against SQLi
Who Should Follow This Series?
This tutorial series is ideal for:
- IT Security Professionals looking to evaluate Azure WAF
- Azure Administrators wanting to enhance their security skills
- DevOps teams considering integrating WAF into their CI/CD pipelines
- Anyone interested in practical, hands-on web application security testing
Prerequisites and Important Notes
To get the most out of this series, you should:
- Have basic familiarity with Azure resource deployment and administration
- Understand fundamental web application security concepts
- Be comfortable with command-line interfaces and basic scripting
- An Azure subscription to deploy the Azure WAF Attack Testing Lab
Please note:
- This lab focuses specifically on the OWASP protection ruleset and logging capabilities of Azure WAF.
- While we cover application security concepts, this is not a comprehensive guide to application security testing.
- Always perform security testing in controlled, authorized environments.
Getting Started
Ready to dive in? Our first post in the series will walk you through setting up your Azure WAF Attack Testing Lab. We’ll cover everything from resource deployment to tool installation, ensuring you’re fully prepared for the hands-on exercises that follow.
Stay tuned for Part 1: “Setup an Azure WAF Attack Testing Lab“