Table of Contents
In this blog, I’m going to show you how to configure profiles in Azure Windows virtual desktop, and how to set up FSLogix profile service with Azure Windows virtual desktop. Okay first a little bit about FSlogix, FSlogix is now part of Microsoft and Microsoft is making the product available for profile management in Windows virtual desktops, this is a good thing per Microsoft documentation user profile disks are being depreciated.
Benefits of Installing FSLogix on WVD
- FSLogix profile containers are high performance and resolve performance issues that have historically blocked cached exchange mode.
- Without FSLogix profile containers, OneDrive for Business is not supported in non-persistent RDSH or VDI environments.
- Maintain user context in non-persistent environments
- Minimize sign in times for non-persistent environments
- Optimize file IO between host/client and remote profile store
- Native (Local) profile experience, eliminating many compatibility issues with solutions using visible redirection, such as User Profile Disk (UPD).
- Simplify the management of applications and ‘Gold Images’
- Specify the version of Java to be utilized by specific URL and applications
I’m going to go over the basics of FSlogix installation using file shares to hold profile containers this is the process outlined in Microsoft documentation. So this is the plan I have a managed image with all my software just like we did in the last blog ( WVD Golden image Customization and updates using Shared Image Gallery ) I’m going to deploy that to a new VM and configure FS logic that will then be turned into a managed image.
So with that here’s what I’m going to cover in the demo
- Prepare a virtual machine to act as a file share for user profiles
- Grant the Windows Virtual Desktop users with the required Permissions on the created share.
- Deploy a new VM from the template
- Install and configure FSlogix software
- Convert that VM to a new template
- Deploy the Windows virtual desktop pool using the new template
- Test the profiles
Prepare a virtual machine to act as a file share for user profiles
Add the Windows Virtual Desktop Active Directory users to an Active Directory security group. This security group will be used to authenticate the Windows Virtual Desktop users to the file share virtual machine you just created. 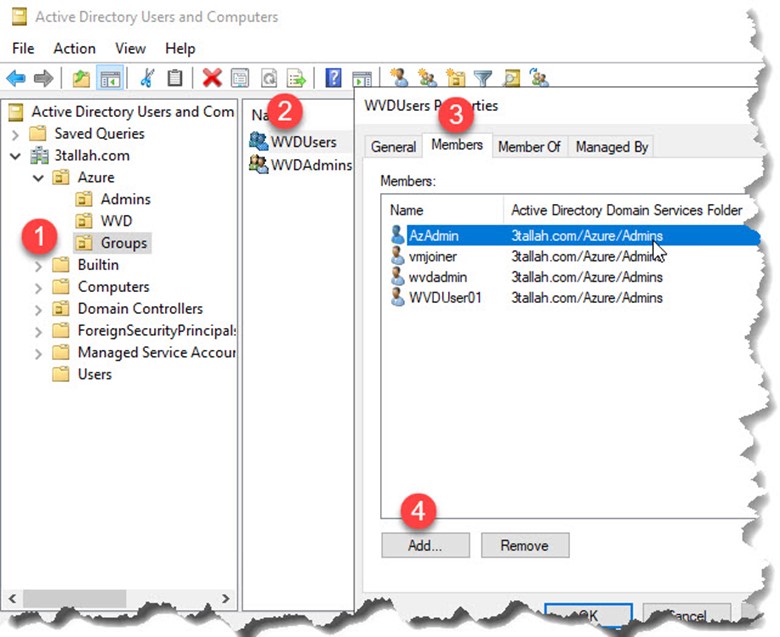
Grant the Windows Virtual Desktop users with the required Permissions on the created share
Create a new folder, Right-click the new folder, select Properties, select Sharing, then select Advanced sharing…. Select Share this folder, select Permissions…, then select Add…., Search for the security group to which you added the Windows Virtual Desktop users,
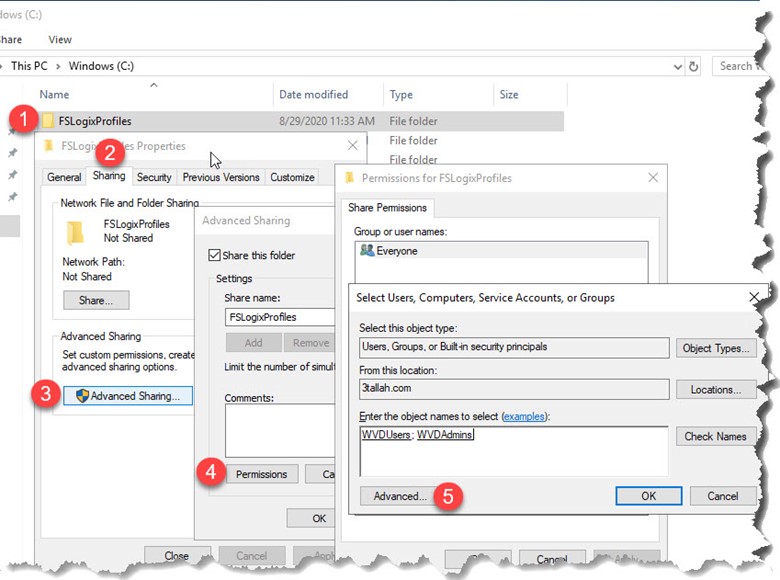
Then make sure that group has Full Control.

After adding the security group, right-click the folder, select Properties, select Sharing, then copy down the Network Path to use for later.
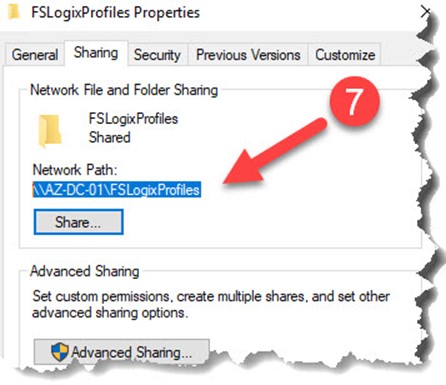
Deploy a new VM from the template
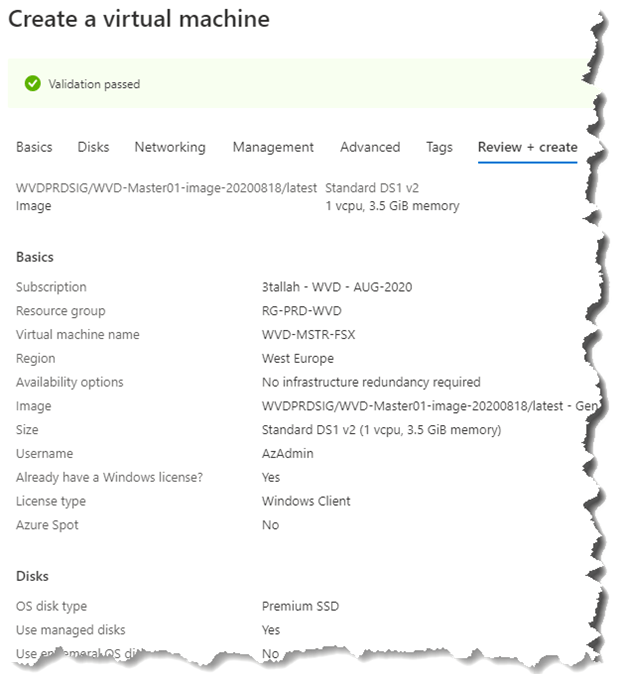
Open Create a virtual machine blade
- Subscription: Select the subscription where the new VM will be created.
- Resource group: Create a new resource group or use an existing one.
- Virtual machine name: Enter a name for the Master virtual machine (Ex. WVD-MSTR-FSX)
- Region: Select the (Region) where you want to create the host pool.
- Availability Zone: (1,2,3)
- Image: Select the image created in previous article (Azure Shared Image Gallery and Windows Virtual Desktop) (Ex. WVDPRDSIG/WVD-Master01-image-20200818/latest – Gen1)
- Size: Select VM Size (Ex. D2s_V3)
- License Type: Windows Client
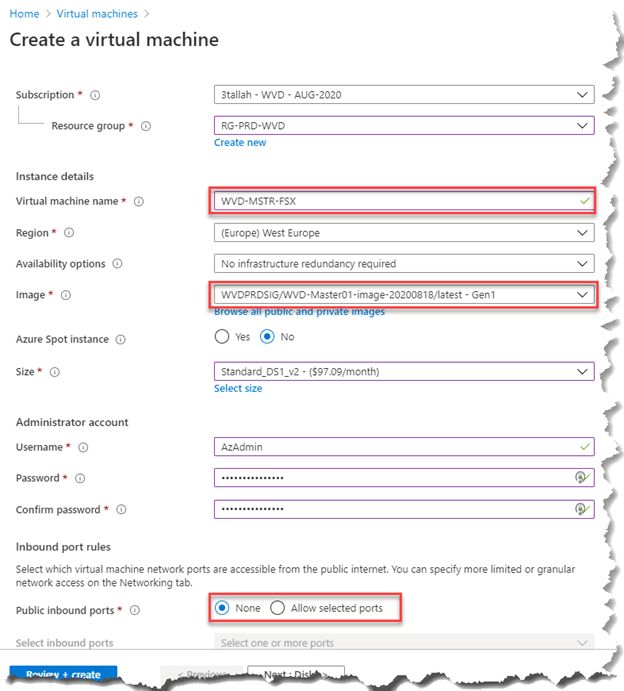
For the rest of configuration, you can follow the ( Step 2: Create VM from the created Managed Disk )
Install and configure FSlogix software
Configure FSlogix software: Option 1 (Manuel values creation using Regedit)
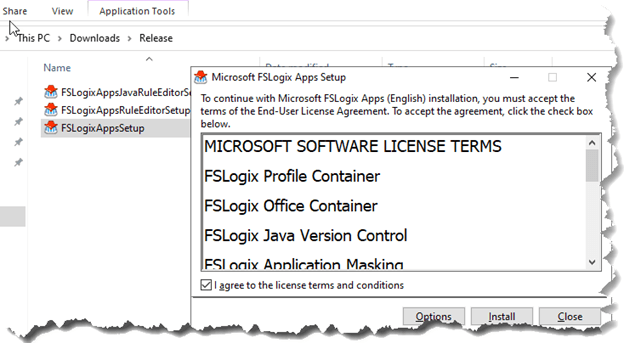
- Download the FSLogix agent using this link
- Extract the right Release (64 or 32) and run FSLogixAppsSetup to install the FSLogix agent.
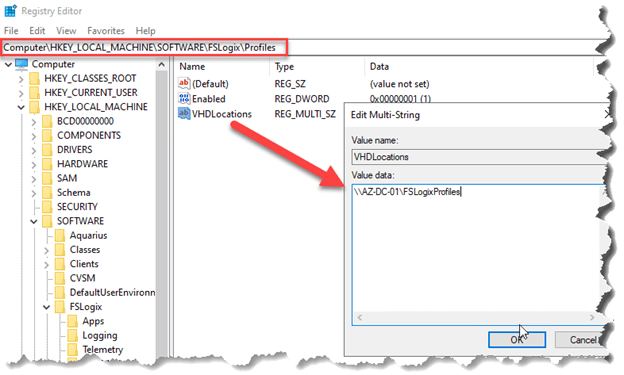
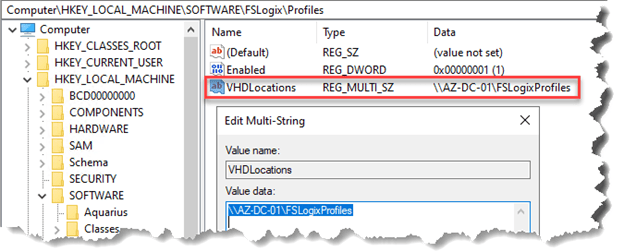
- From the start menu, run RegEdit as an administrator. Navigate to Computer\HKEY_LOCAL_MACHINE\software\FSLogix.
- Create a key named Profiles.
- Create the following values for the Profiles key:
| Name | Type | Data/Value |
| Enabled | DWORD | 1 |
| VHDLocations | Multi-String Value | “Network path for file share” |
Configure FSlogix software: Option 2 (Registry file)
Just follow the Same Steps in option 1 from 1 to 4
Then you have to download and install this Registry file
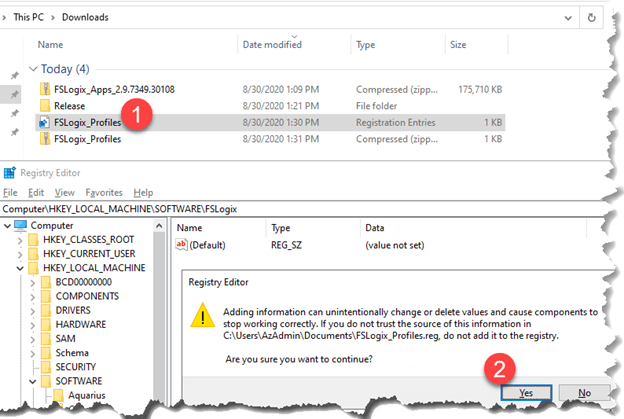
Modify VHDLocations with “Network path for file share”
Configure FSlogix software: Option 3 (Use FSLogix Group Policy (GPO) Template Files)
- Connect to Domain Controller
- Download the FSLogix agent using this link
- Extract the right Release (64 or 32)
- Copy the ADMX file (fslogix.admx) to C:\Windows\PolicyDefinitions
- Copy the ADML file (fslogix.adml) to C:\Windows\PolicyDefinitions\en-US
- Run GPEDIT.MSC
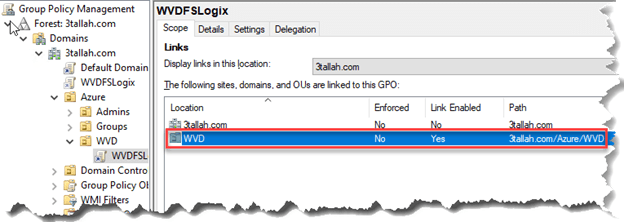
- Create New GPO and linked to WVD OU
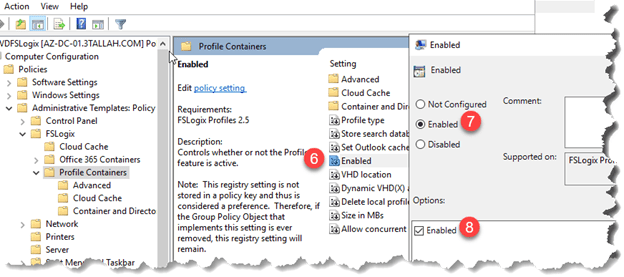
- Browse to Computer Configuration > Policies > Administrative Templates > FSLogix > Profile Containers > VHD Location (Enable it)
- Modify VHDLocations with “Network path for file share”

- Browse to Computer Configuration > Policies > Administrative Templates > FSLogix > Profile Containers > Enabled (Enable it)
NOTE: Windows Virtual Desktop doesn’t require an open inbound port 3389 for users to access the host pool’s VMs. We don’t recommend to open inbound port 3389 on your WVD VMs.
Convert that VM to a new template
Follow the same Step that we highlighted earlier in Azure Shared Image Gallery and Windows Virtual Desktop to
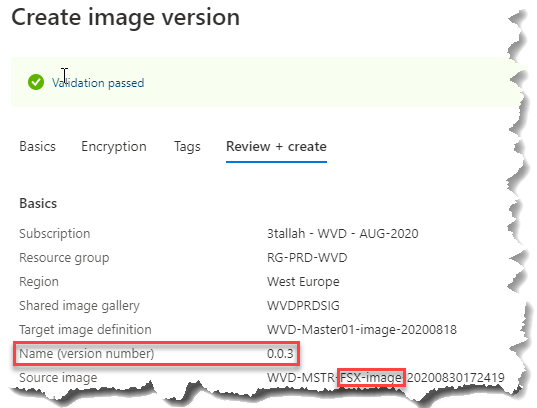
Deploy the Windows virtual desktop pool using the new template
Just like we have done before in this article (Deploy a Windows Virtual Desktop Host pool with the custom image) Please follow this section to Creating your new host pool
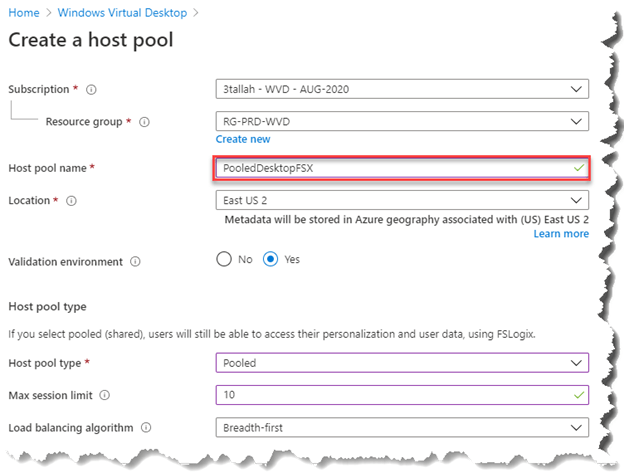
- Select Image Type Gallery
- Click on Browse all images and disks > My Items > Click on the Latest Image (Ex. WVD-MSTR-FSX-image-20200830172419)
- Rest of Steps are same like previous article (Creating your new host pool)


Verify FSLogix Profile Container on File Share.
Access Assignments
Go to Assignments under Newly created Hostpool Application group and assign WVD Users Group.

Access Testing Profile Creation Varication
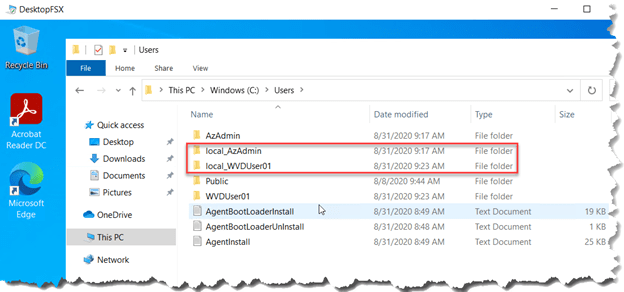
Logon as a specific user and check if the Profile Container is being created on the File Share. See the example below.

Verify Profile Creation through WVD Session host.
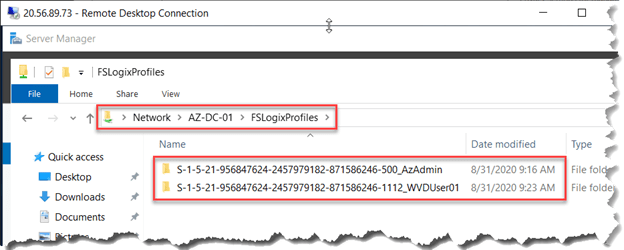
Verify Profile Creation through File Share.
Azure Files integration with Azure Active Directory Domain Service
FSLogix profile containers’ performance and features take advantage of the cloud. On August 7th, 2019, Microsoft Azure Files announced the general availability of Azure Files authentication with Azure Active Directory Domain Service (AD DS). By addressing both cost and administrative overhead, Azure Files with Azure AD DS Authentication is a premium solution for user profiles in the Windows Virtual Desktop service.
Best practices for Windows Virtual Desktop
Windows Virtual Desktop offers full control over size, type, and count of VMs that are being used by customers. To ensure your Windows Virtual Desktop environment follows best practices:
- Azure Files storage account must be in the same region as the session host VMs.
- Azure Files permissions should match permissions described in Requirements – Profile Containers.
- Each host pool must be built of the same type and size VM based on the same master image.
- Each host pool VM must be in the same resource group to aid management, scaling and updating.
- For optimal performance, the storage solution and the FSLogix profile container should be in the same data center location.
- The storage account containing the master image must be in the same region and subscription where the VMs are being provisioned.
Check out my Udemy course for AZ-140 Azure Virtual Desktop
Use This link for 80% OFF 





2 Comments
Comments are closed.