Introduction
Welcome to the first installment of our four-part Azure Web Application Firewall (WAF) Security Lab series. In this tutorial, we’ll walk you through creating a comprehensive lab environment for testing Azure WAF’s protection capabilities against real-world web application attacks.
Series Overview
- Part 1: Lab Setup – Building Your Azure WAF Testing Environment (This post)
- Part 2: Reconnaissance Playbook – Testing Azure WAF Protection
- Part 3: Vulnerability Exploitation Playbook – Azure WAF vs XSS
- Part 4: Data Disclosure and Exfiltration Playbook
Why This Lab Matters
Before deploying Azure WAF in production environments, it’s crucial to understand its effectiveness in identifying, detecting, and protecting against potential threats. This lab provides a controlled setting to explore Azure WAF’s OWASP protection ruleset and logging capabilities.
What You’ll Accomplish
By the end of this tutorial, you will have:
- Deployed a demo test environment in Azure
- Set up Azure Monitor Workbook for WAF
- Enabled a desktop environment on a Linux VM
- Created host file entries to resolve hostnames
Prerequisites
Before we begin, ensure you have:
- An Azure subscription (If you don’t have one, create a free account)
- A Log Analytics workspace for diagnostic logs
- Familiarity with Azure Application Gateway WAF
- Azure Monitor Workbook for WAF deployed to your workspace
Deployment Steps
- Create a Resource Group: Ex (AzureWAFLab)
- Create a Log Analytics workspace: Ex (LAW-AzureWAFLab)
- Deploy the lab environment using this Azure WAF Attack Testing Lab Environment Deployment Template.
- This ARM deployment encompasses all necessary components for testing Azure WAF Security. Here are the key differences from the default Azure Network Security deployment template:
- A custom Docker image featuring a modified version of the OWASP Juice Shop application.
- Pre-configured Azure Firewall rules permitting inbound and outbound connectivity for the Kali VM.
- Select the pre-created resource group and fill in the log analytics workspace information
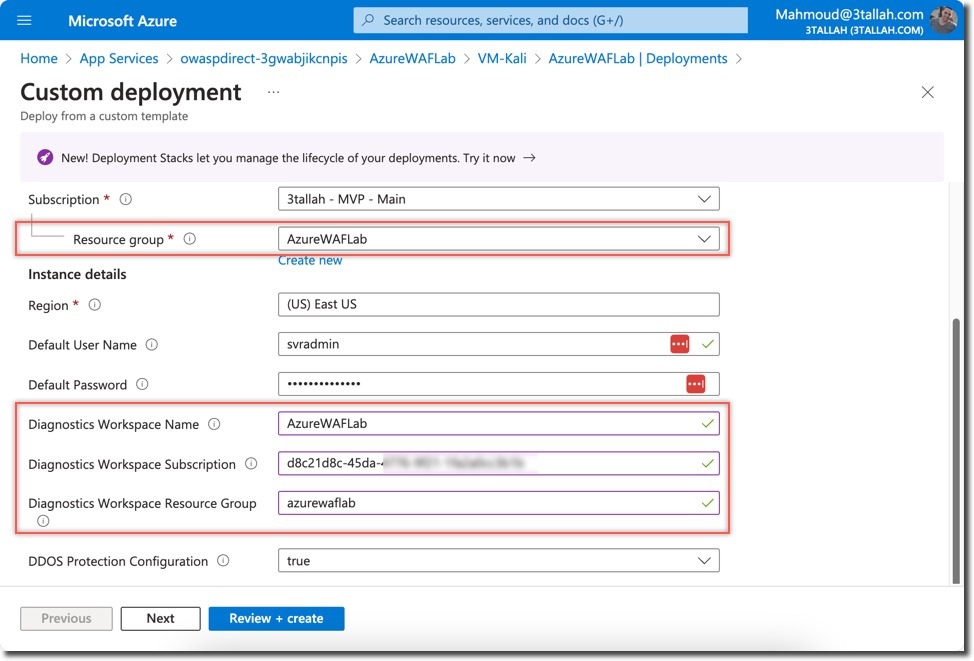
- Deploy the Azure Monitor Workbook for WAF to your Azure subscription.
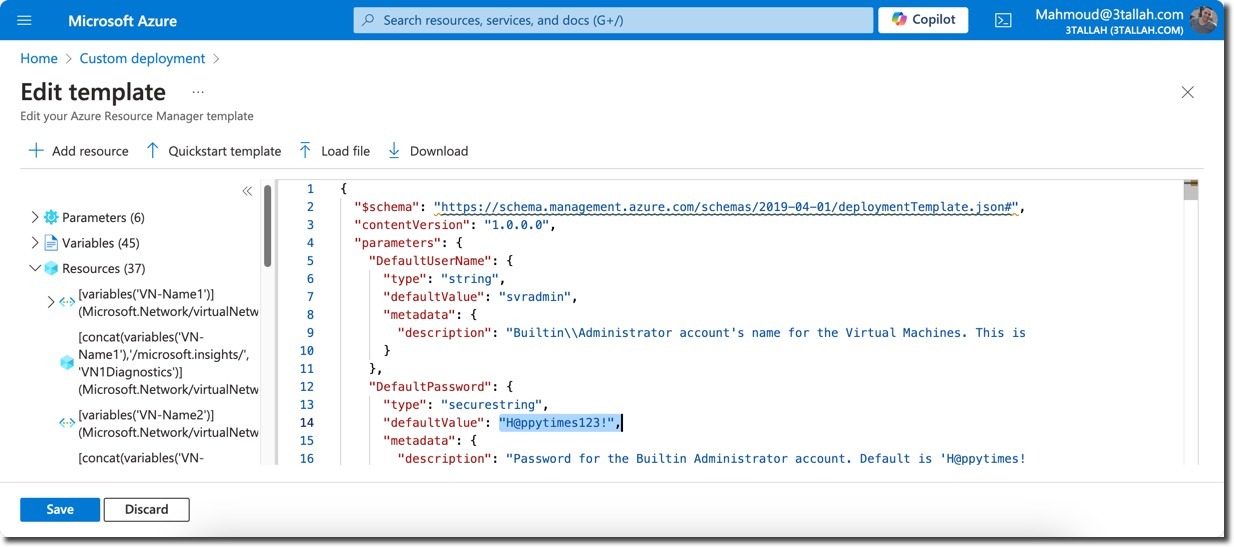
NOTE: Admin User: svradmin Admin Password: H@ppytimes123! (strongly recommend to change the default lab password after deployment)
Lab Environment Overview
Our lab setup includes:
- A customized OWASP Juice Shop web application
- Azure Application Gateway with WAF
- A Kali Linux VM as the attacker machine
- Azure Firewall for traffic routing
Here’s a visual representation of our lab environment:
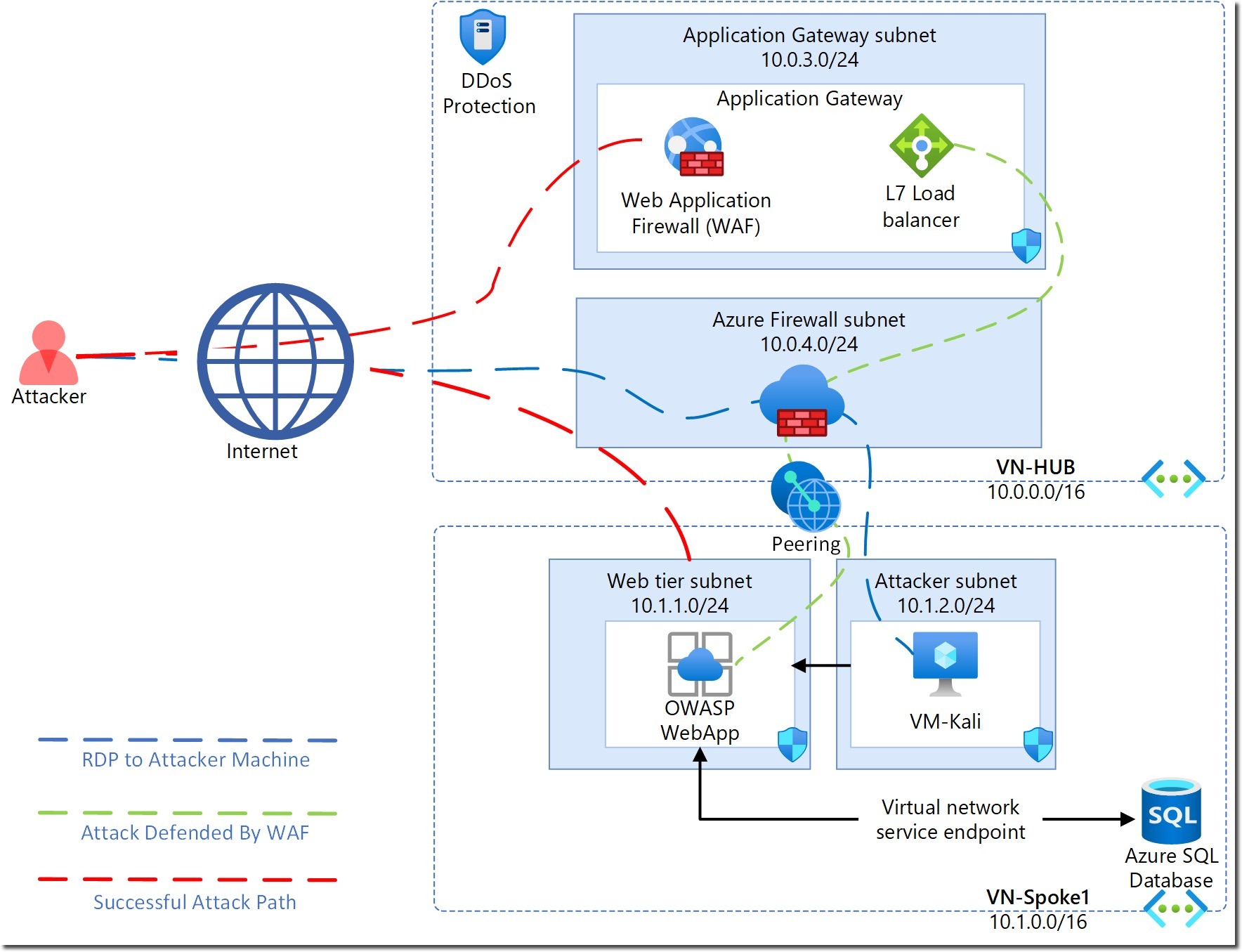
Key components include:
- VM-Kali: Attacker VM with pre-installed penetration testing tools
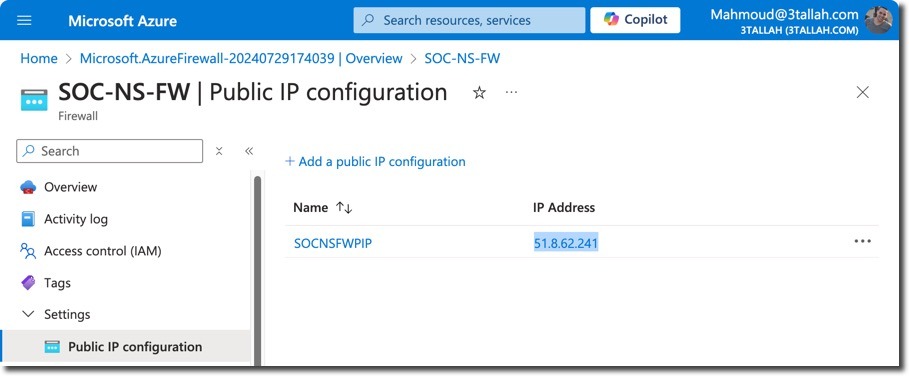
- SOC-NS-FW: Azure Firewall for traffic inspection
- SOC-NS-AG-WAFv2: Azure WAF on Application Gateway
- OWASP WebApp: Vulnerable web application for testing
Configuration Steps
1. Update Kali Linux and Install Desktop Environment
Connect to the Kali VM via SSH:
ssh svradmin@<Public IP Address of Azure Firewall>
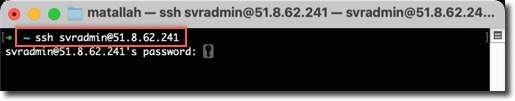
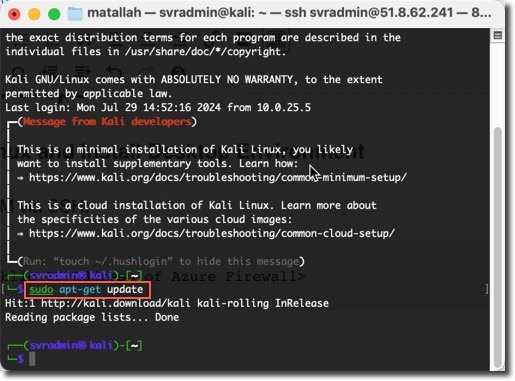
Update the Kali Linux distribution:
sudo apt-get update
Install and configure the remote desktop server:
sudo apt-get install -y kali-desktop-xfce xorg xrdp
sudo systemctl enable xrdp
echo xfce4-session >~/.xsession
sudo service xrdp restart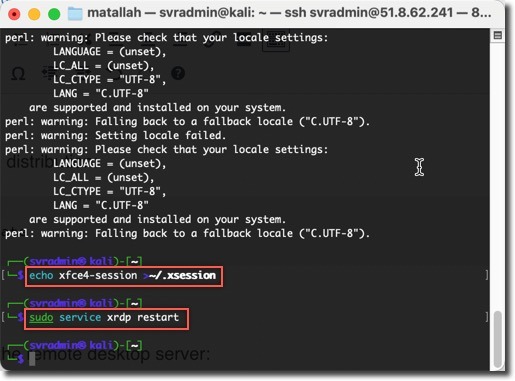
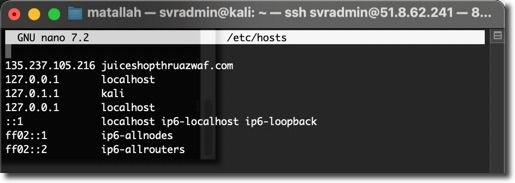
2. Configure Hosts File on Kali VM
Add an entry to map the OWASP Juice Shop site to the Application Gateway’s public IP:
sudo nano /etc/hosts
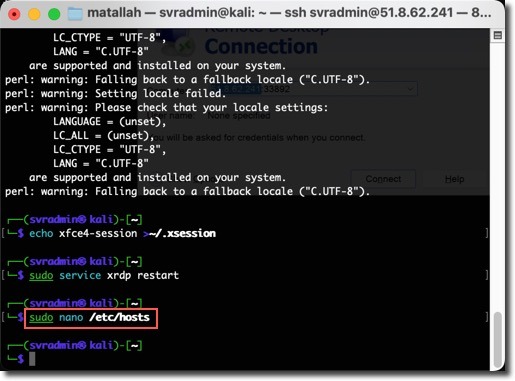
Add the following entry:
127.0.1.1 localhost
127.0.1.1 kali
<Public IP Address of the Application Gateway> juiceshopthruazwaf.com
Save the hosts file and exit
- Use Ctrl+S to save and Ctrl+X to exit
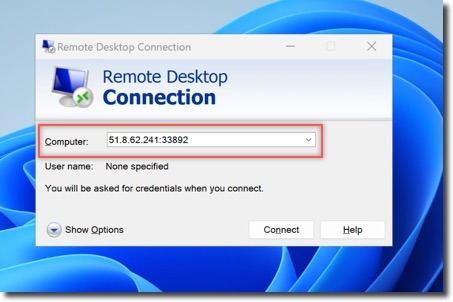
3. Connect to Kali VM via RDP
Use your RDP client to connect to:
<Public IP Address of Azure Firewall>:33892
Next Steps
Before moving on to the next tutorial:
- Review the OWASP Juice Shop publishing rule on Application Gateway
- Examine the Web Application Firewall configuration
- Test connectivity to the OWASP Juice Shop website:
- Access it directly
- Access it through the Application Gateway
Tip: Find the public URL of the Juice Shop app in the Azure Portal under Resource Group > owaspdirect- > URL
Conclusion
Congratulations! You’ve now set up a comprehensive Azure WAF testing environment. This lab will serve as the foundation for our upcoming tutorials, where we’ll explore reconnaissance techniques, vulnerability exploitation, and data exfiltration scenarios.
Part 2: Reconnaissance Playbook and start putting your new lab environment to the test!
Credits
- ARM Template Auther: @tobystic