Introduction
Welcome to the third installment of our Azure Web Application Firewall (WAF) Security Lab series. In this comprehensive tutorial, we’ll dive deep into vulnerability exploitation, specifically focusing on Cross-Site Scripting (XSS) attacks and how Azure WAF protects against them.
Series Overview
- Part 1: Lab Setup – Building Your Azure WAF Testing Environment
- Part 2: Reconnaissance Playbook – Testing Azure WAF Protection
- Part 3: Vulnerability Exploitation Playbook – Azure WAF vs XSS (This post)
- Part 4: Data Disclosure and Exfiltration Playbook
Why XSS Matters
Cross-Site Scripting (XSS) remains one of the most prevalent and dangerous web application vulnerabilities. Attackers can use XSS to inject malicious scripts into trusted websites, potentially compromising user data, hijacking sessions, or even taking control of the application. Understanding how Azure WAF mitigates these threats is crucial for maintaining robust web application security.
What You’ll Accomplish
By the end of this tutorial, you will:
- Set up Burp Suite for intercepting and analyzing web traffic
- Perform a Server-Side XSS attack against the OWASP Juice Shop application
- Compare the results of XSS attempts with and without Azure WAF protection
- Analyze Azure WAF’s response using the Azure Monitor Workbook
Prerequisites
- Completed Azure WAF security lab setup from Part 1
- Familiarity with basic web security concepts and XSS attacks
- Completion of the reconnaissance playbook tutorial (Part 2)
Setting Up Your Testing Environment
Configuring Burp Suite and Firefox
Burp Suite is a powerful web application security testing tool. We’ll use it to intercept and analyze requests and responses during our XSS attack attempts.
- Connect to your Kali Linux VM via RDP
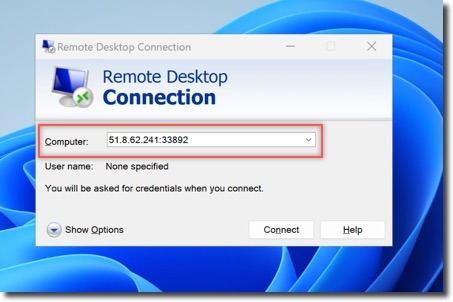
- Launch Burp Suite:
- If not installed, run
sudo apt install -y burpsuitein the terminal 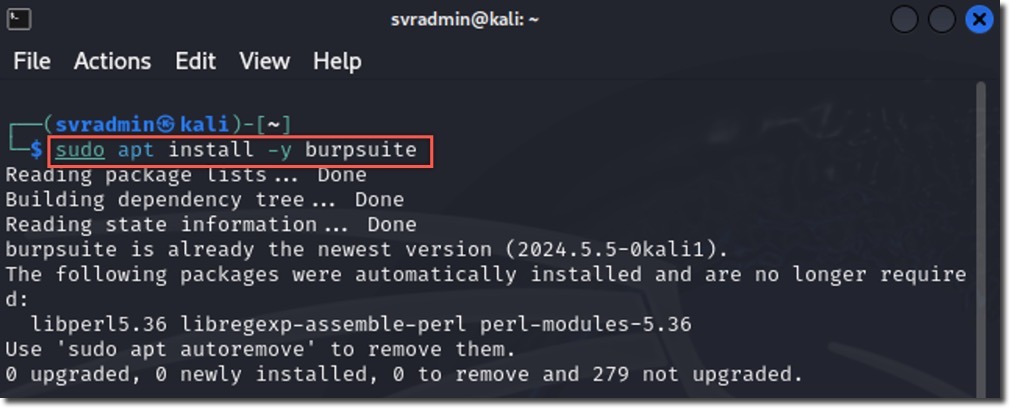
- Applications > Web Application Analysis > burpsuite
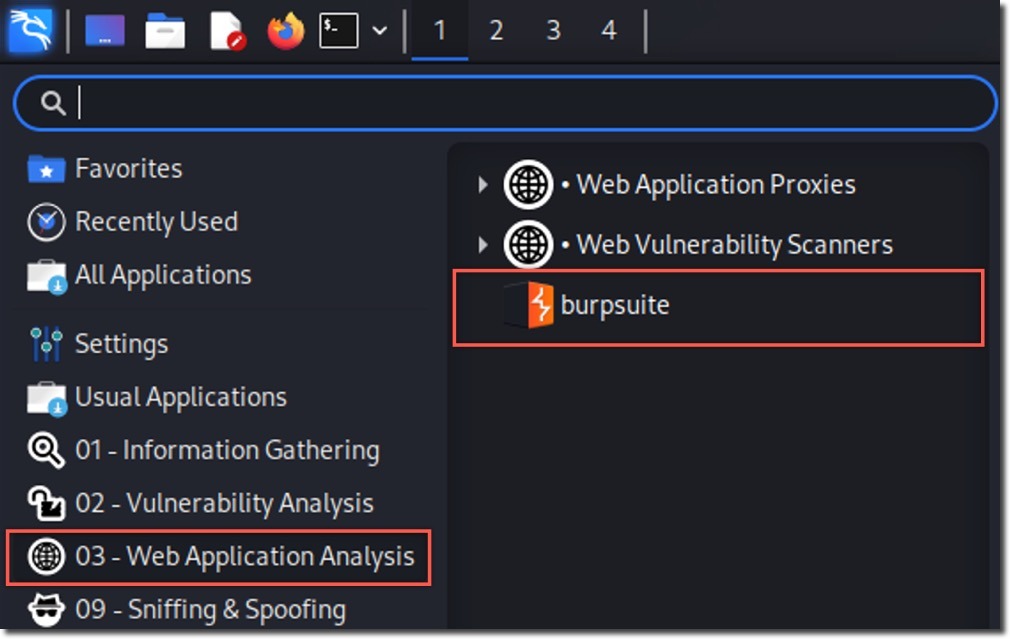
- If not installed, run
- Configure Burp Suite:
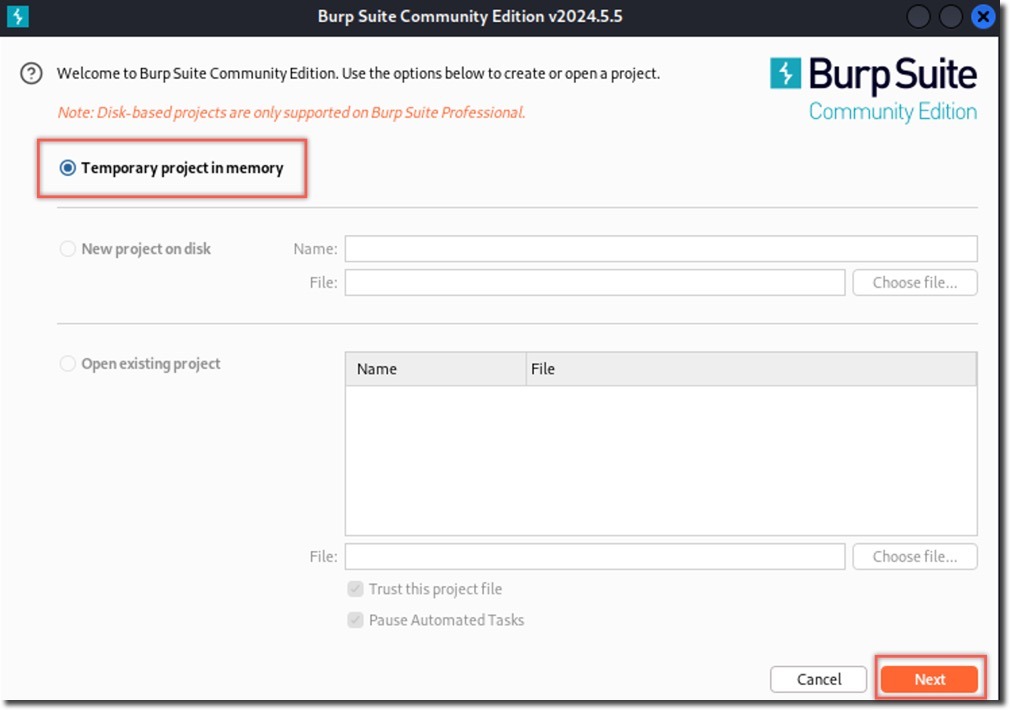
- Start a temporary project with default settings
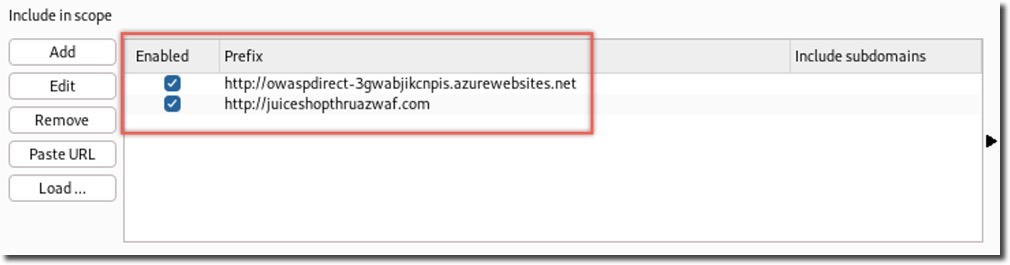
- In Target > Scope, add these URLs:
http://owaspdirect-<deployment guid>.azurewebsites.net http://juiceshopthruazwaf.com 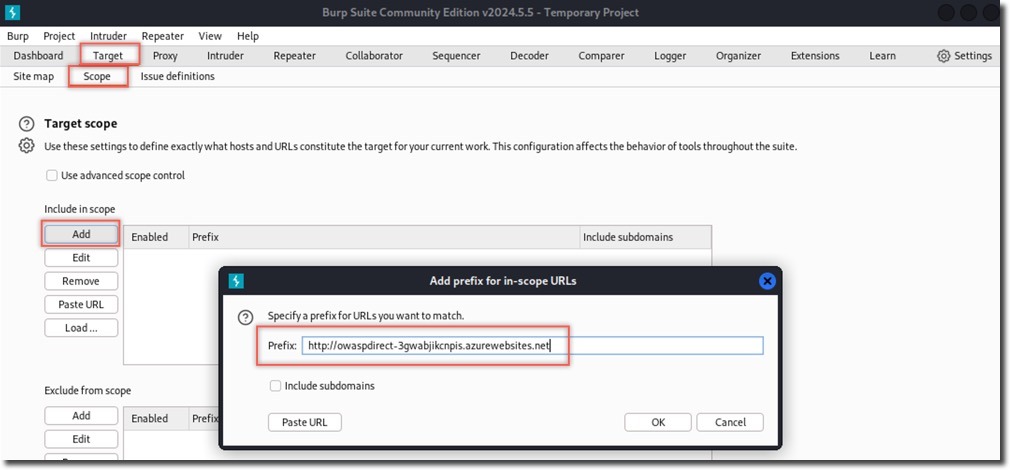
- Optionally exclude
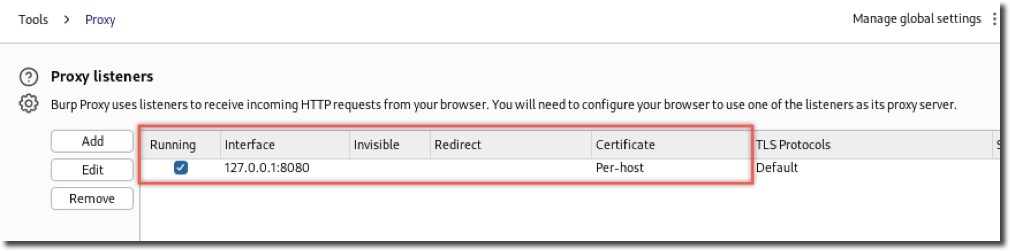
/socket.io/paths to reduce noise - Verify Proxy is running on 127.0.0.1:8080 (Proxy > Options)
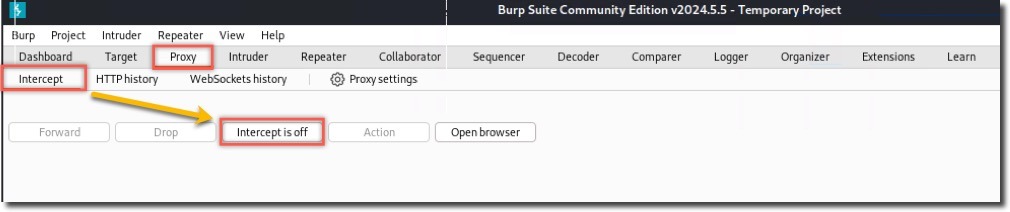
- Turn off intercept (Proxy > Intercept)
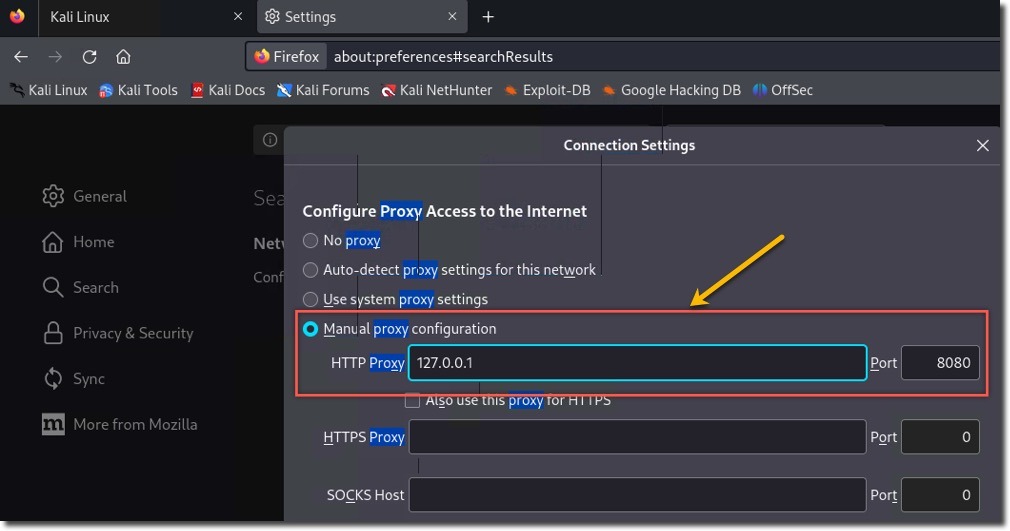
- Configure Firefox to use Burp Suite as a proxy:
- Menu > Preferences > Network Proxy > Settings
- Manual proxy configuration: 127.0.0.1:8080
Performing the XSS Attack
We’ll attempt a Server-Side XSS (Stored XSS) attack against the OWASP Juice Shop application in two scenarios:
Scenario 1: Direct Attack (Without WAF)
- Browse to
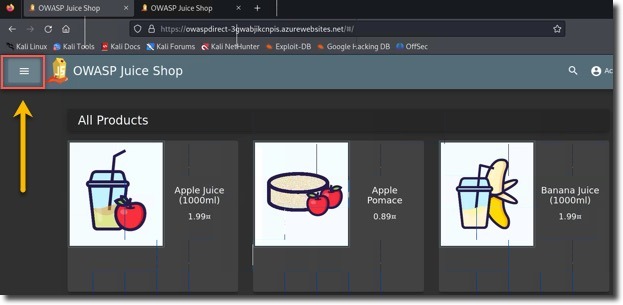
http://owaspdirect-<deployment guid>.azurewebsites.net - Navigate to Customer Feedback
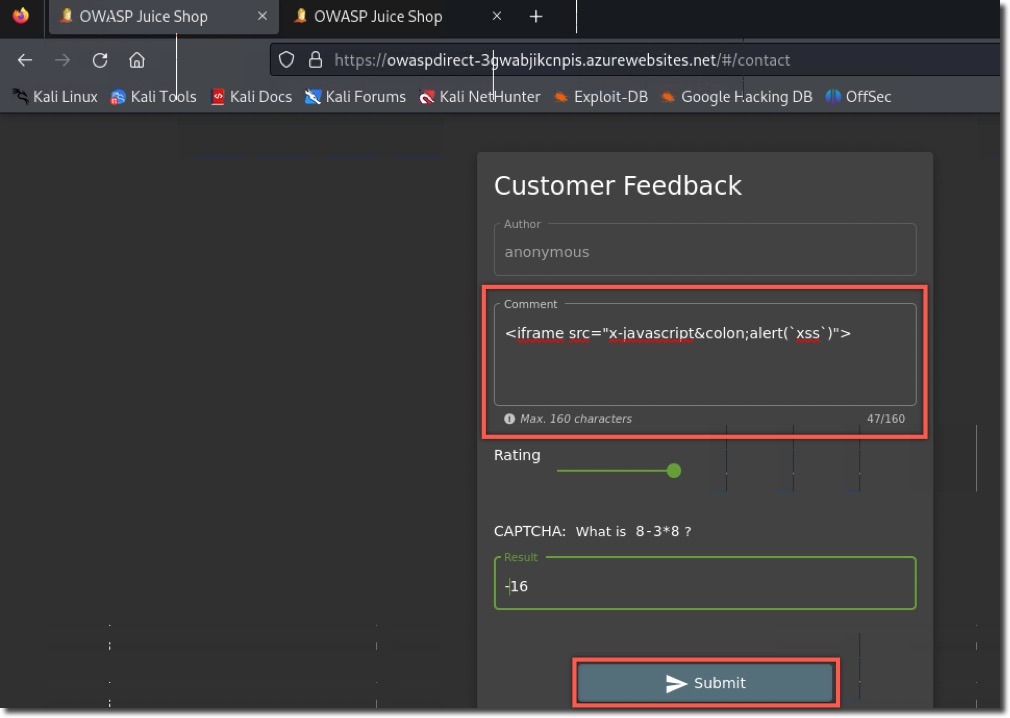
- In the Comment box, paste this XSS payload:
<iframe src="x-javascript:alert(`xss`)"> - Complete the form and submit
Analysis:
- Observe the “Thank you” message after submission
- In Burp Suite, examine the request and response:
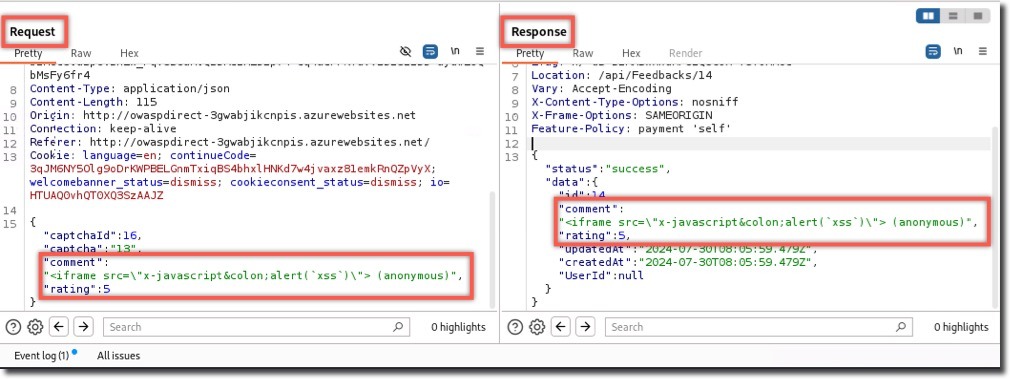
- Request shows the XSS payload in the comment field
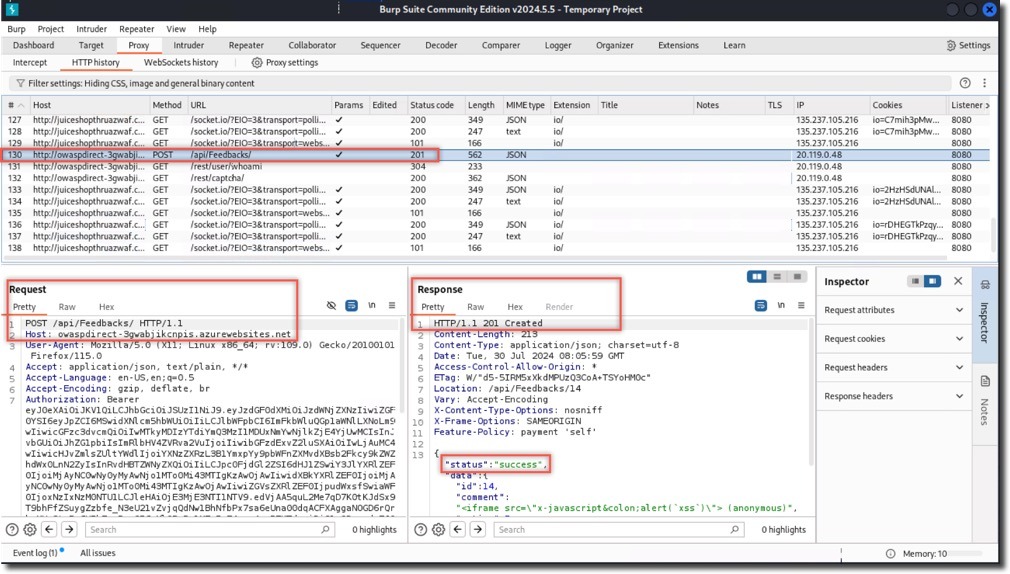
- Response shows a 201 Created status, indicating successful response
- Verify the exploit:
- Navigate to the “About Us” page
- Observe the XSS alert pop-up, confirming the vulnerability
Scenario 2: Attack Through Azure WAF
- Open a new Firefox instance
- Browse to
http://juiceshopthruazwaf.com - Repeat the same steps to submit the XSS payload
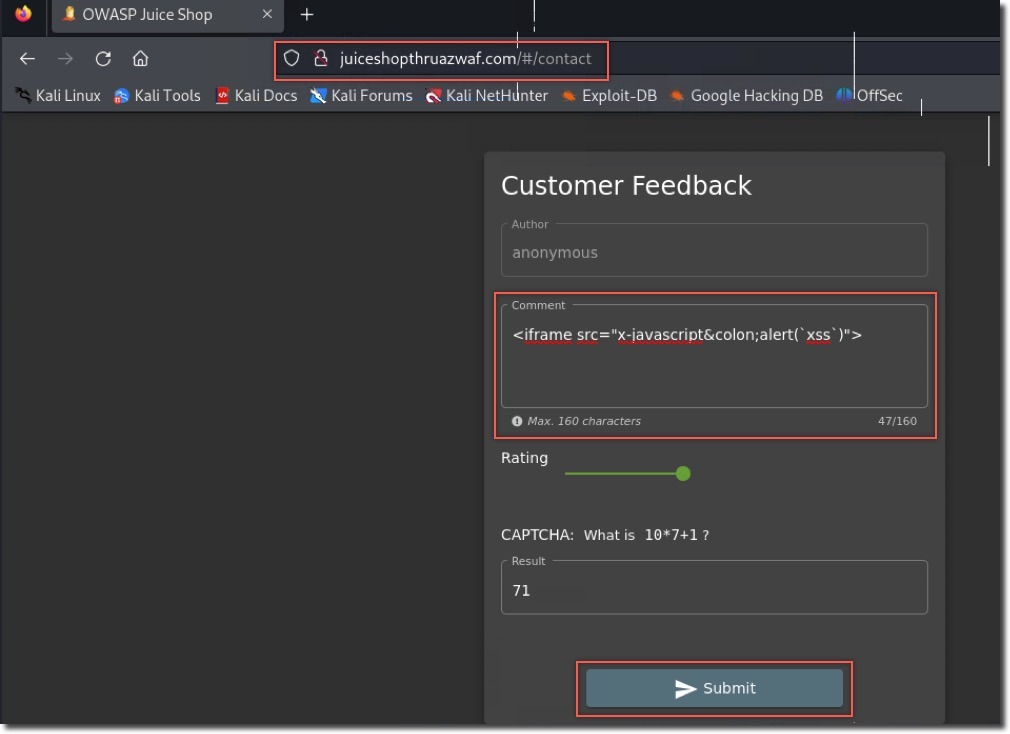
Analysis:
- Notice the absence of a “Thank you” message
- In Burp Suite, examine the request and response:
- Request is identical to Scenario 1
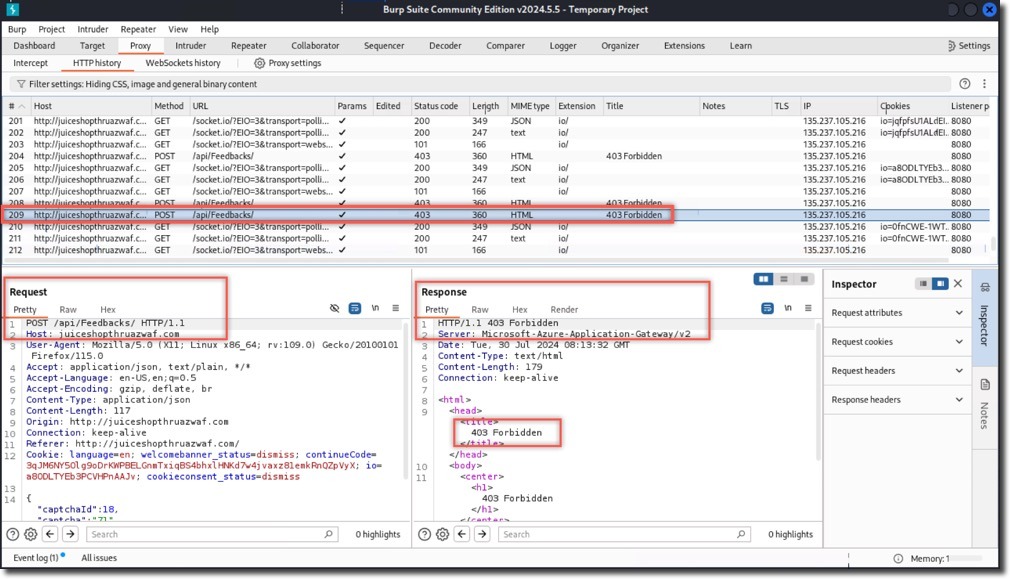
- Response shows a 403 Forbidden status from Azure Application Gateway
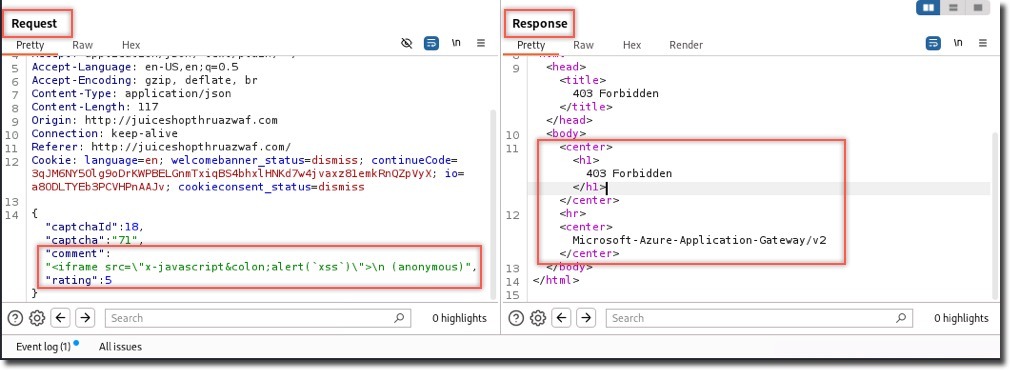
Understanding WAF’s Response
To dive deeper into how Azure WAF handled the XSS attempt, we’ll use the Azure Monitor Workbook for WAF.
- Access the WAF workbook in Azure Portal
- Set appropriate filters:
- Time Range
- WAF Type
- WAF Items
- Analyze the key sections:
- WAF actions filter
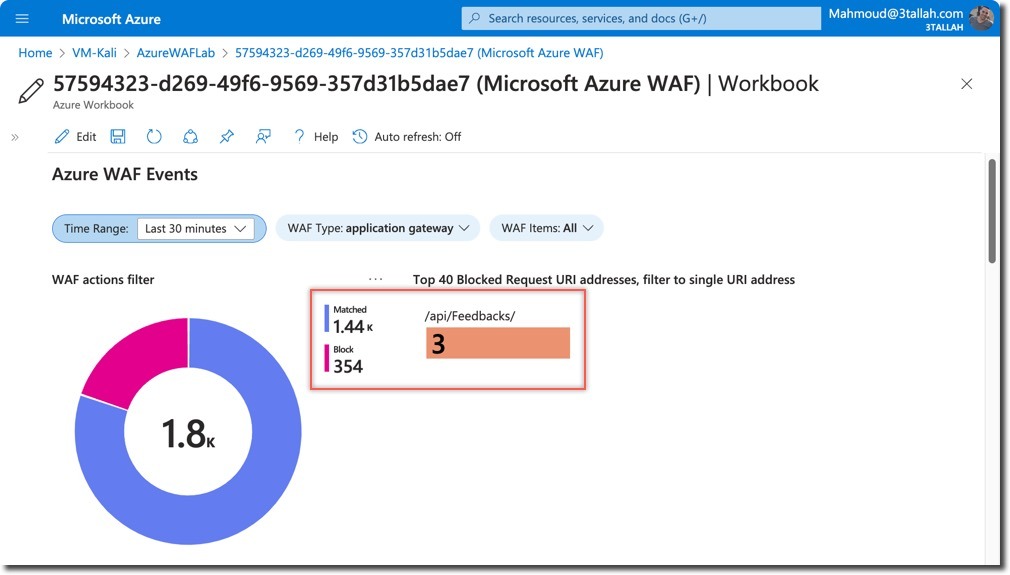
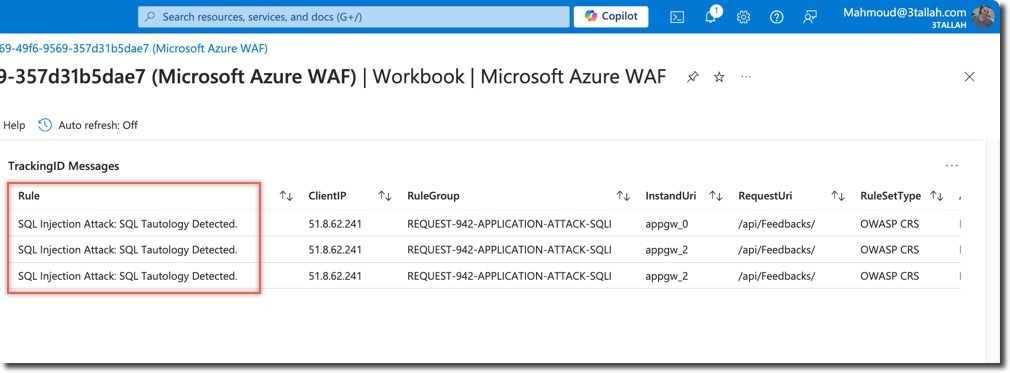
- Top Blocked Request URI addresses
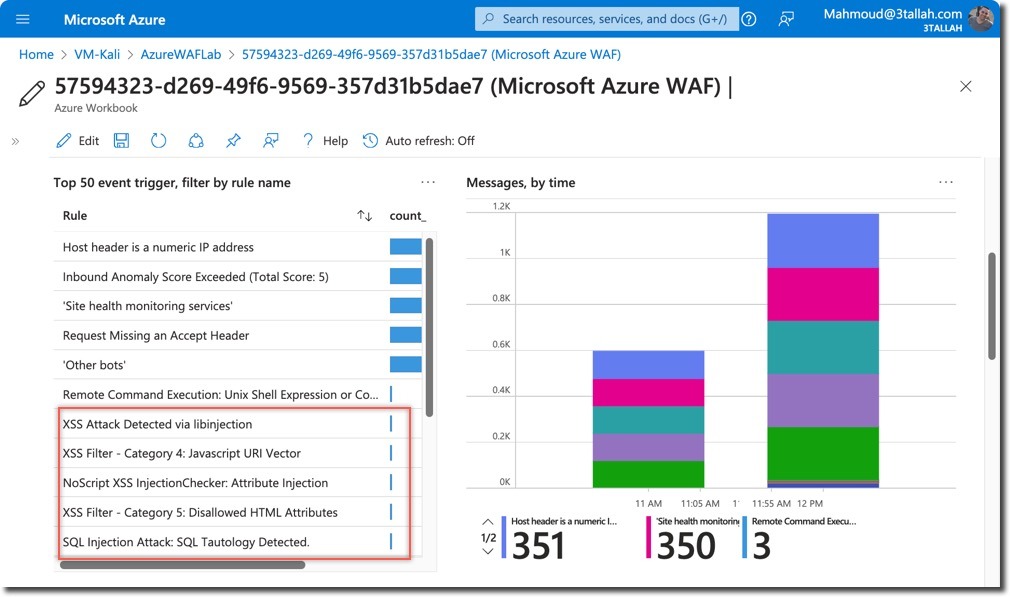
- Top event triggers by rule name
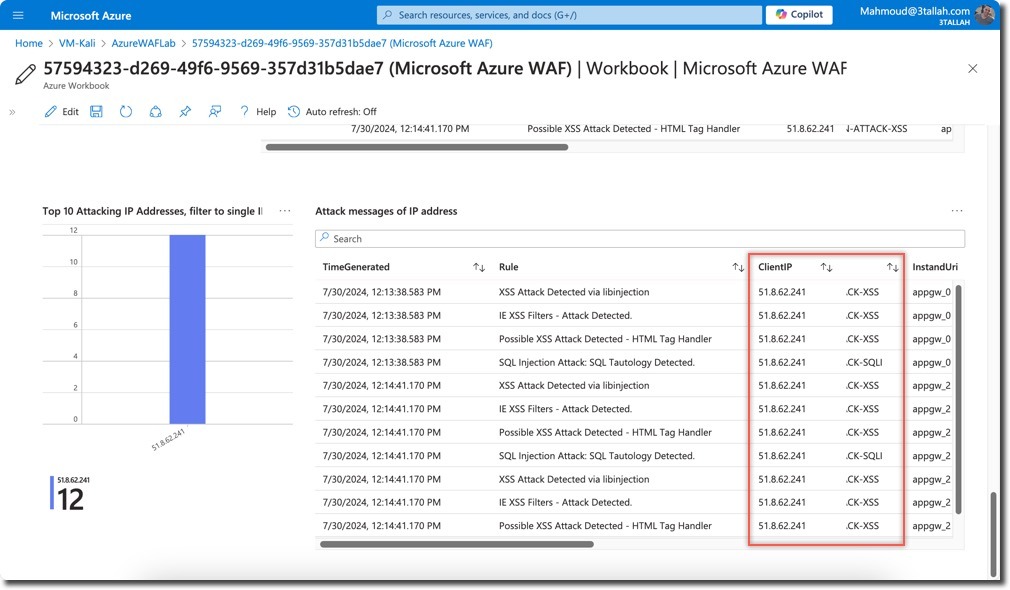
- Client and Attack details
Key Findings:
- Two requests to
/api/Feedbacks/were blocked - Multiple WAF rules were triggered, including:
- XSS Attack Detected via libinjection
- XSS Filter – Category 4: Javascript URI Vector
- NoScript XSS InjectionChecker: HTML Injection
- IE XSS Filters – Attack Detected
- The traffic was blocked due to exceeding the Anomaly Score threshold (Total Score: 53, XSS=35)
In-Depth Analysis of WAF’s XSS Protection
Azure WAF employs a multi-layered approach to detect and block XSS attempts:
- Pattern Matching: WAF looks for known XSS patterns in requests, like
<script>tags or JavaScript events. - Anomaly Scoring: Each potential threat is assigned a score. When the cumulative score exceeds a threshold, the request is blocked.
- Context-Aware Filtering: WAF analyzes where and how potentially malicious content appears in the request.
- Libinjection: This library helps detect SQL injection and XSS attempts by tokenizing and analyzing input.
- Recursive Inspection: WAF can decode and analyze content multiple times to catch obfuscated attacks.
In our test, the XSS payload triggered multiple rules, demonstrating the effectiveness of this layered approach.
Key Takeaways
- XSS vulnerabilities can be easily exploited in unprotected applications, potentially leading to severe security breaches.
- Azure WAF effectively detects and blocks XSS attempts at the network edge, before they reach the application.
- The out-of-the-box ruleset in Azure WAF provides robust protection against various XSS techniques, including obfuscated payloads.
- WAF’s multi-layered approach (pattern matching, anomaly scoring, context analysis) provides comprehensive protection against evolving XSS threats.
- Regularly reviewing WAF logs and fine-tuning rules can further enhance your application’s security posture.
Next Steps
Now that we’ve seen how Azure WAF handles XSS attacks, we’re ready to explore even more sophisticated threats. In our next and final tutorial, we’ll dive into the “Data Disclosure and Exfiltration Playbook” where we’ll test Azure WAF’s capabilities against SQL Injection attacks.
Stay tuned, and keep your lab environment ready for the grand finale of our Azure WAF Security Lab series!