Introduction
Imagine harnessing the power of GPT-powered natural language to seamlessly investigate and respond to the ever-evolving landscape of security incidents, threats, and vulnerabilities within your organization. Today, let’s explore the capabilities of Microsoft’s Security Copilot, an innovative security AI assistant endowed with extensive cybersecurity expertise from Microsoft. This cutting-edge tool empowers users to efficiently tackle common security-related tasks using generative AI.
Security Copilot isn’t just a standalone solution; it seamlessly integrates with various Microsoft services, providing embedded experiences within the new Microsoft Defender XDR, Microsoft Intune for endpoint management, Microsoft Entra for identity and access management, and Microsoft Purview for comprehensive data security, among others.
Works with the Signal in Your Environment
Microsoft Security Copilot is designed to be an enterprise-grade natural language interface to your organization’s security data. Unlike ordinary instances of GPT, Security Copilot is stateful, allowing users to easily return to previous investigation sessions.
Manage Plugins
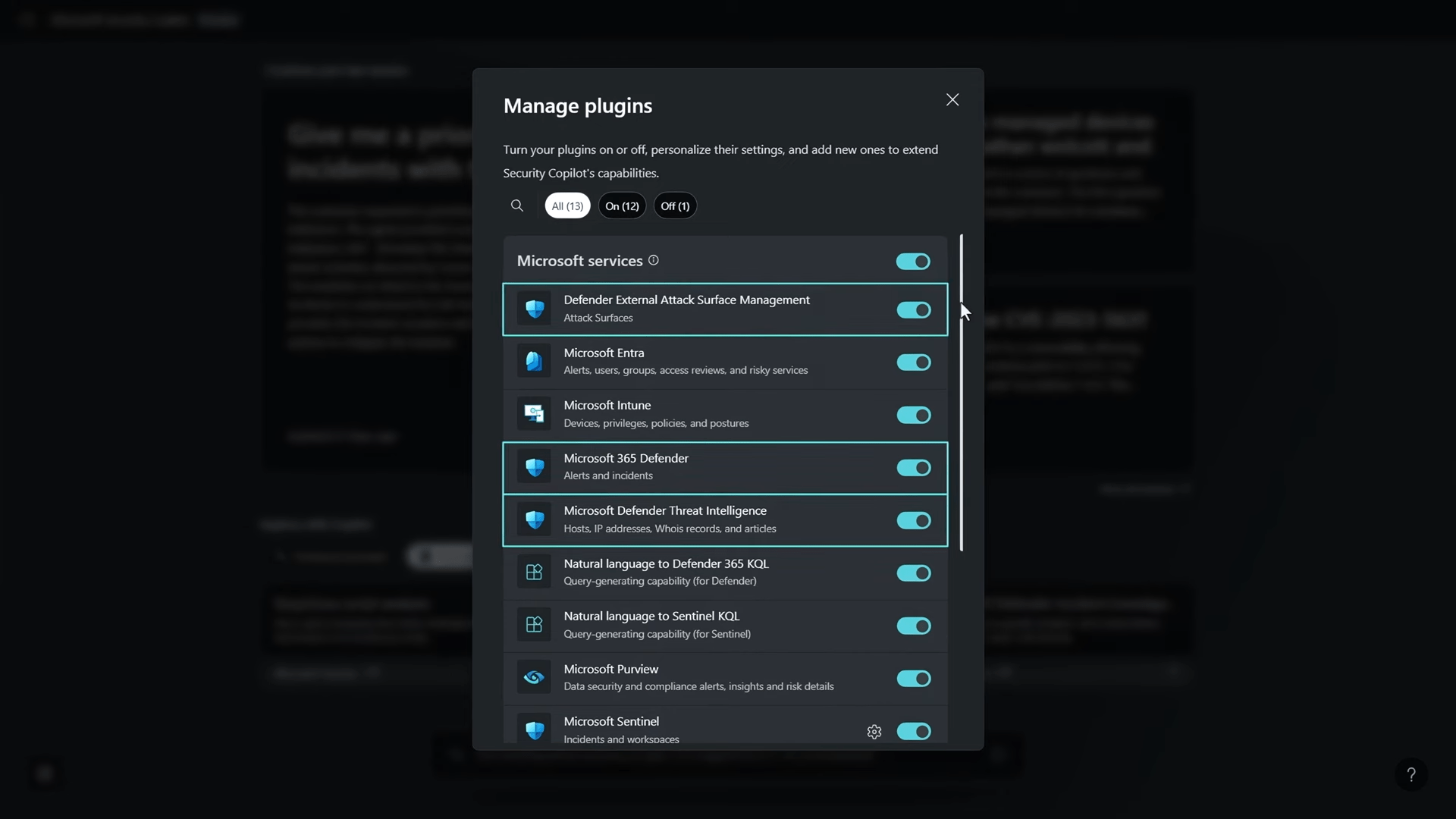
It utilizes managed plugins, such as Microsoft Entra for identity, Microsoft Intune for device endpoints, Microsoft Defender plugins for incidents, Threat Intelligence, Microsoft Purview for data security, and more.
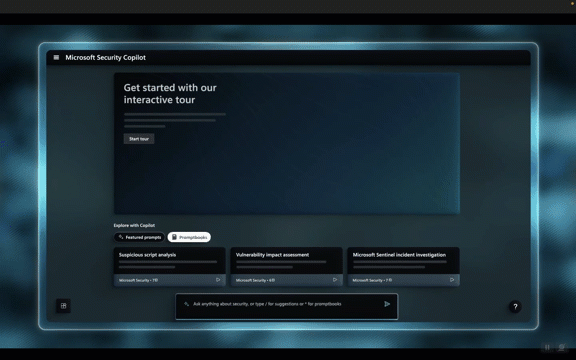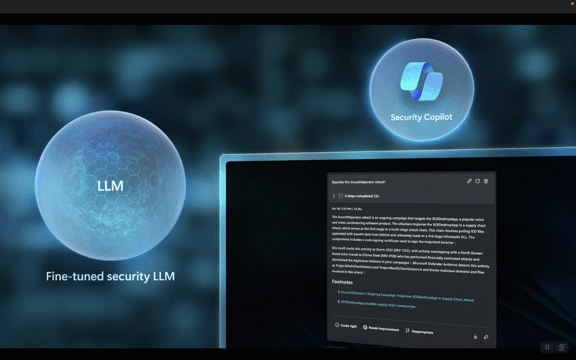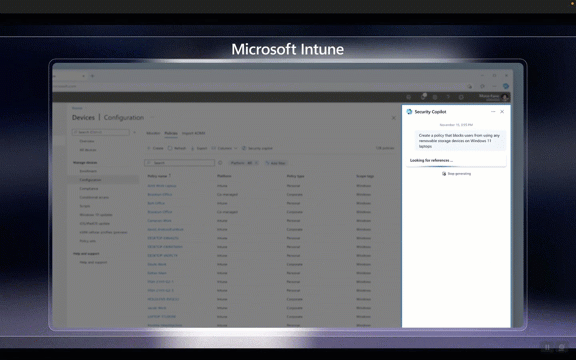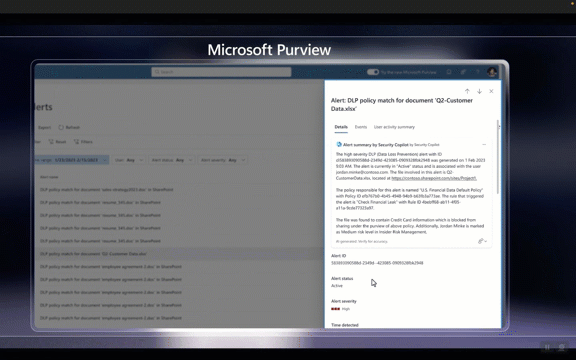
Prompt Experience
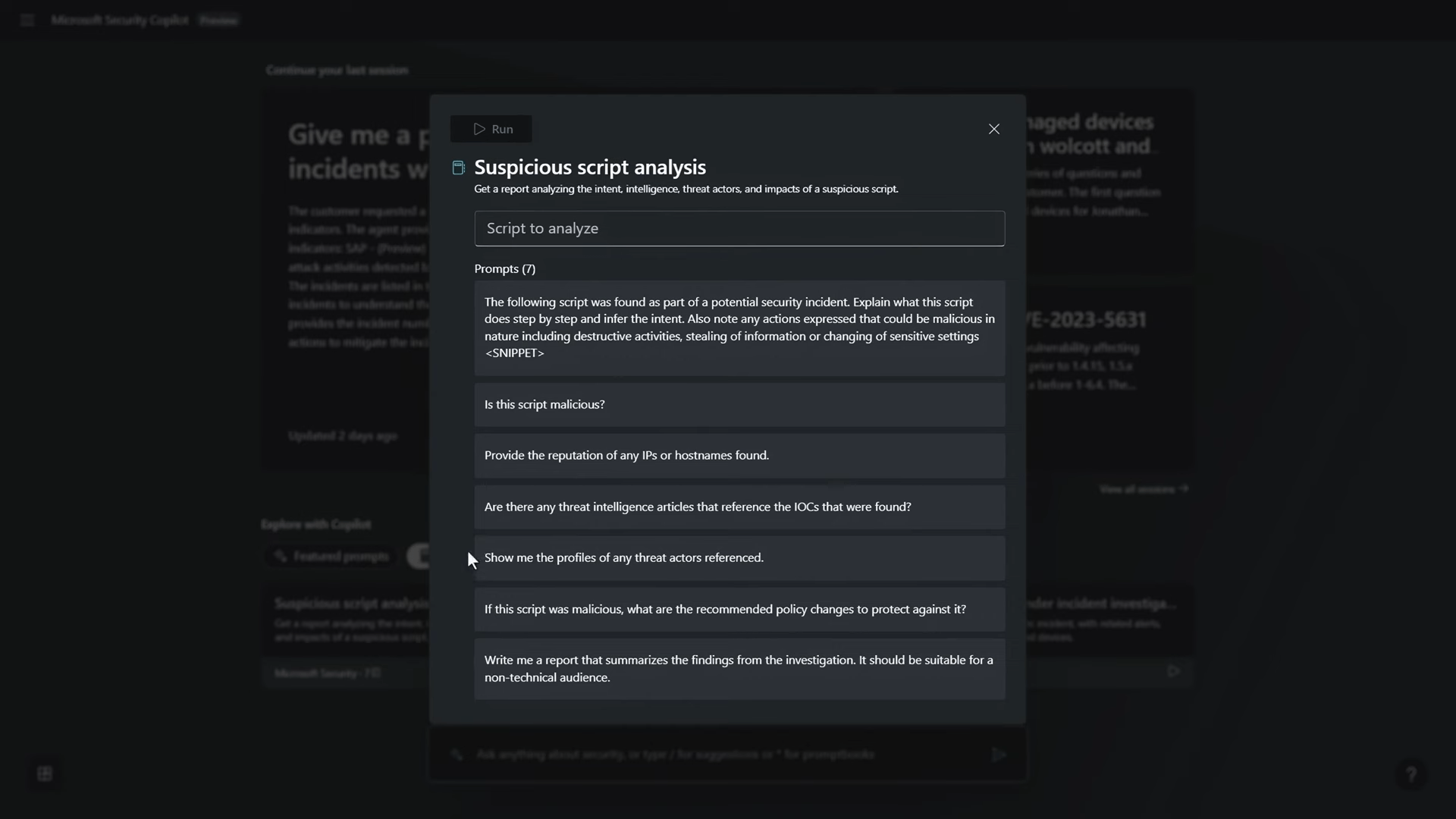
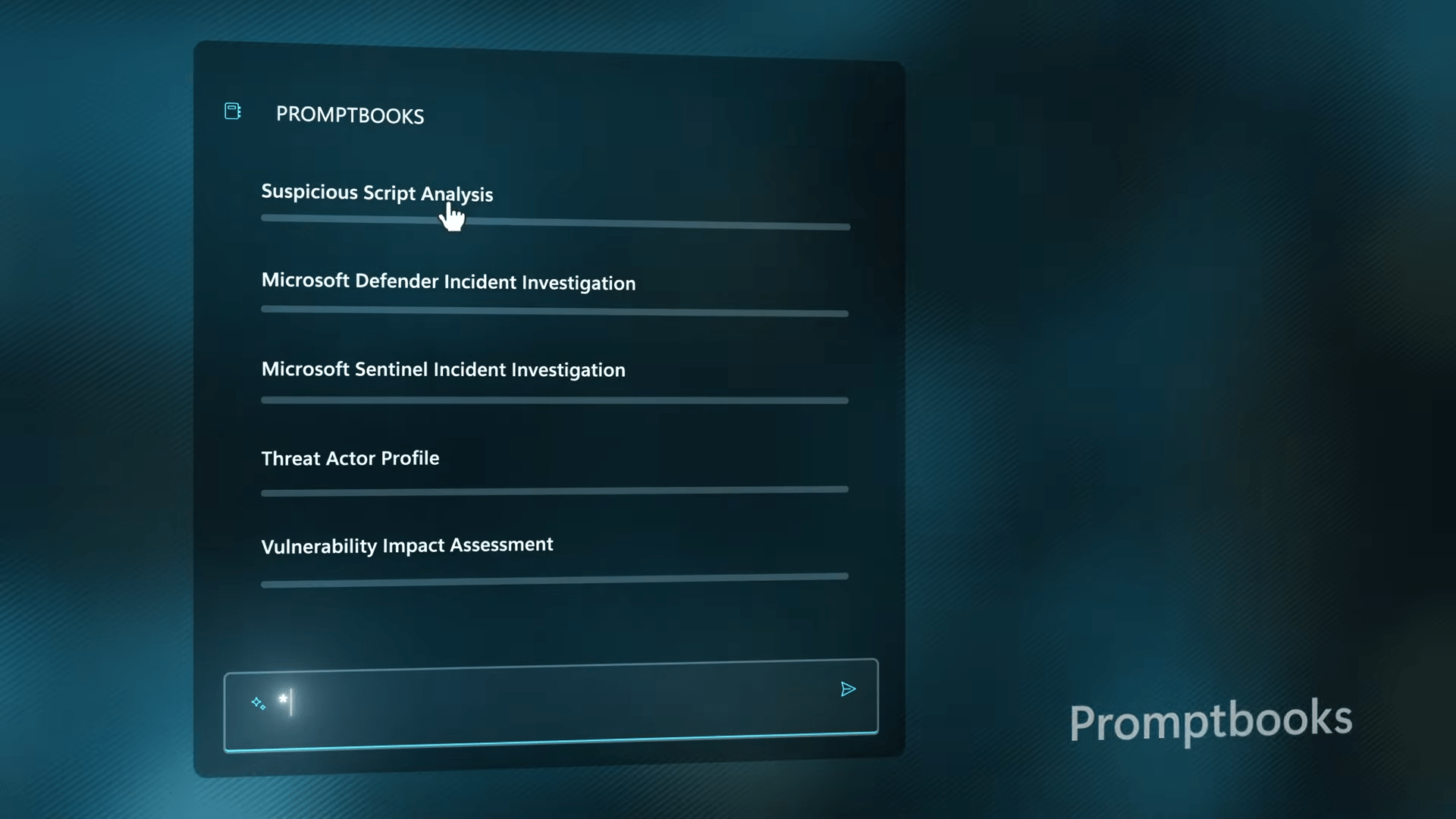
The prompt experience is a key feature of Security Copilot. It proactively suggests prompts to help users get started, making the process more intuitive. Users can interact with the AI using natural language prompts, and the system understands the context based on the connected plugins. Multi-step sequences using Promptbooks enable users to automate security processes, such as suspicious script analysis.
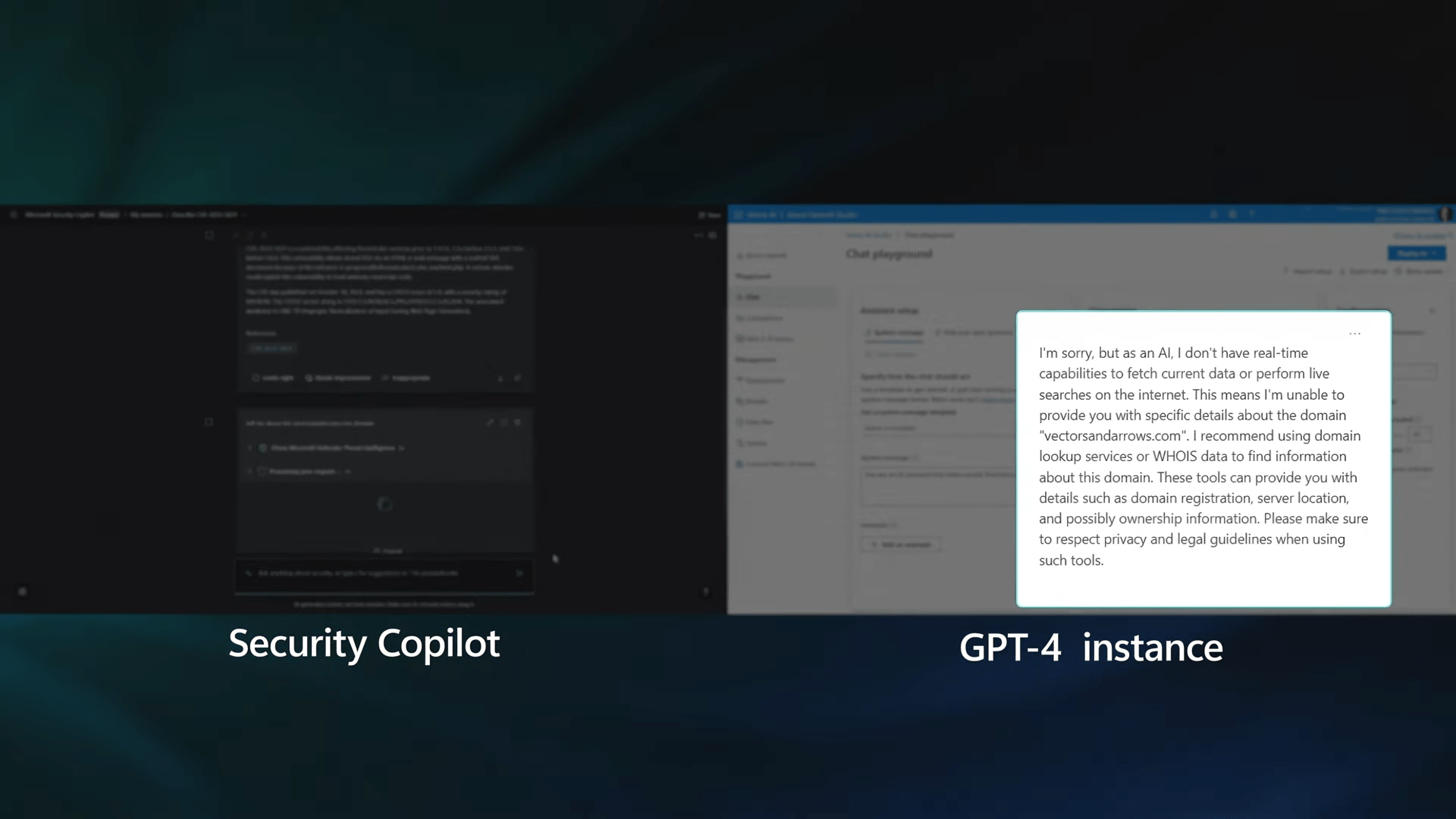
Off-the-Shelf LLM vs. Security Copilot
While off-the-shelf large language models (LLMs) may be used with the right prompts, Security Copilot offers a distinct advantage. The training of Security Copilot involves augmenting the large language model with security skills, resulting in a model specifically tuned for cybersecurity analysis, detection, response, summarization, and more. This fine-tuning is performed using the Low-Rank Adaptive fine-tuning (LoRA) method, ensuring a specialized process tailored to security tasks.
LoRA Fine-Tuning
The LoRA fine-tuning method is a specialized process employed by Microsoft to train the LLM specific to cybersecurity skills. It goes beyond general training, providing the LLM with the necessary knowledge and understanding of security-related tasks. The training is performed on an AI supercomputer with a specialized hardware and software stack in Azure, ensuring optimal performance.
The security analyst can leverage Promptbooks to navigate through complex scenarios, gaining a clear and understandable understanding of potential threats. The power lies in the ability to orchestrate multi-step sequences tailored to specific security processes, enhancing the efficiency and depth of the analysis.
Security Analyst Use Case
Let’s walk through a typical scenario where a security analyst uses Security Copilot to investigate an incident.
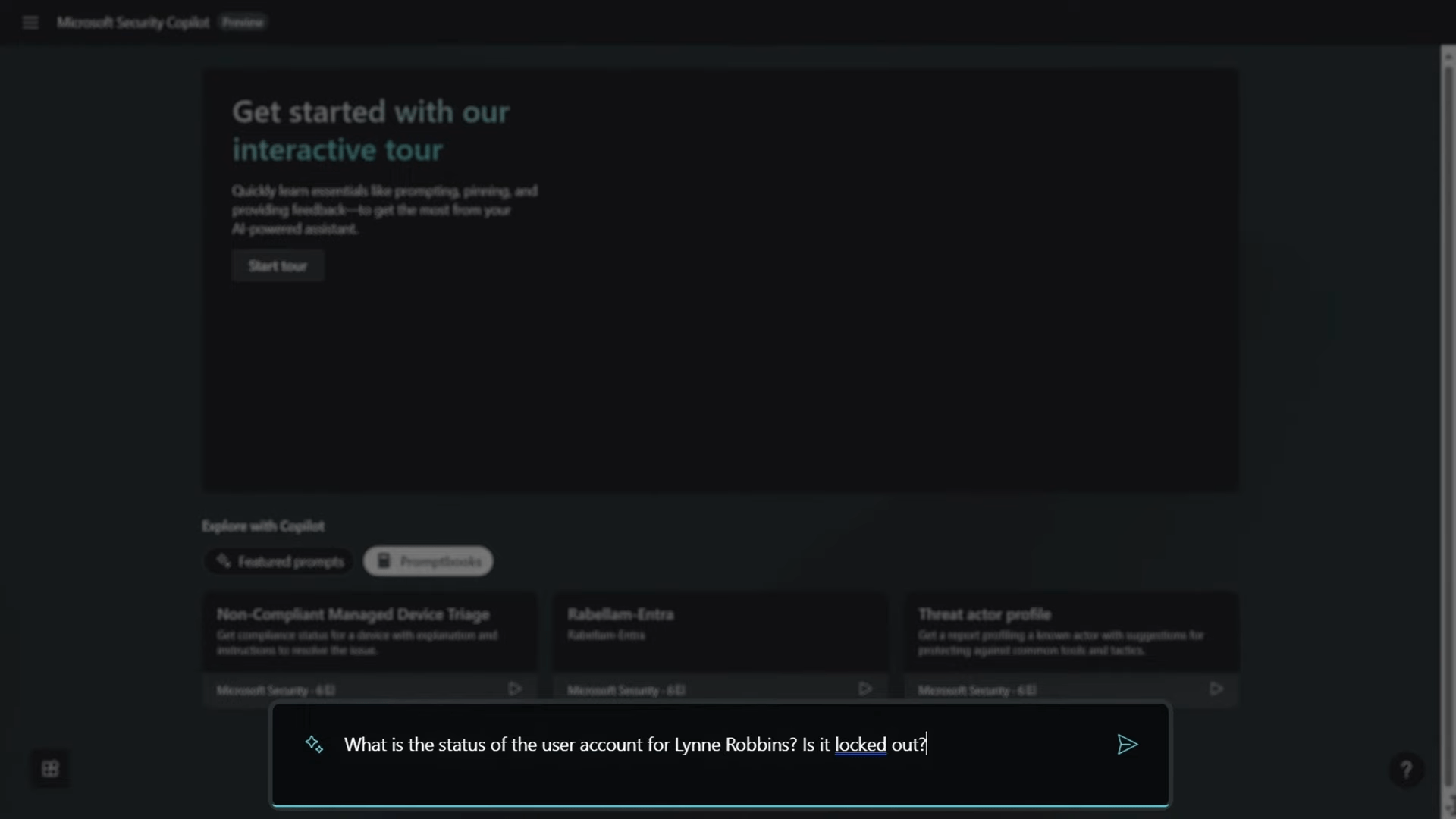
In a real-time security analyst use case, I found myself on an active call with a user, Lynne Robbins, who was experiencing difficulty accessing her device. Leveraging the capabilities of Security Copilot, I initiated the investigation with a prompt: “What is the status of the user account for Lynne Robbins? Is it locked out?”
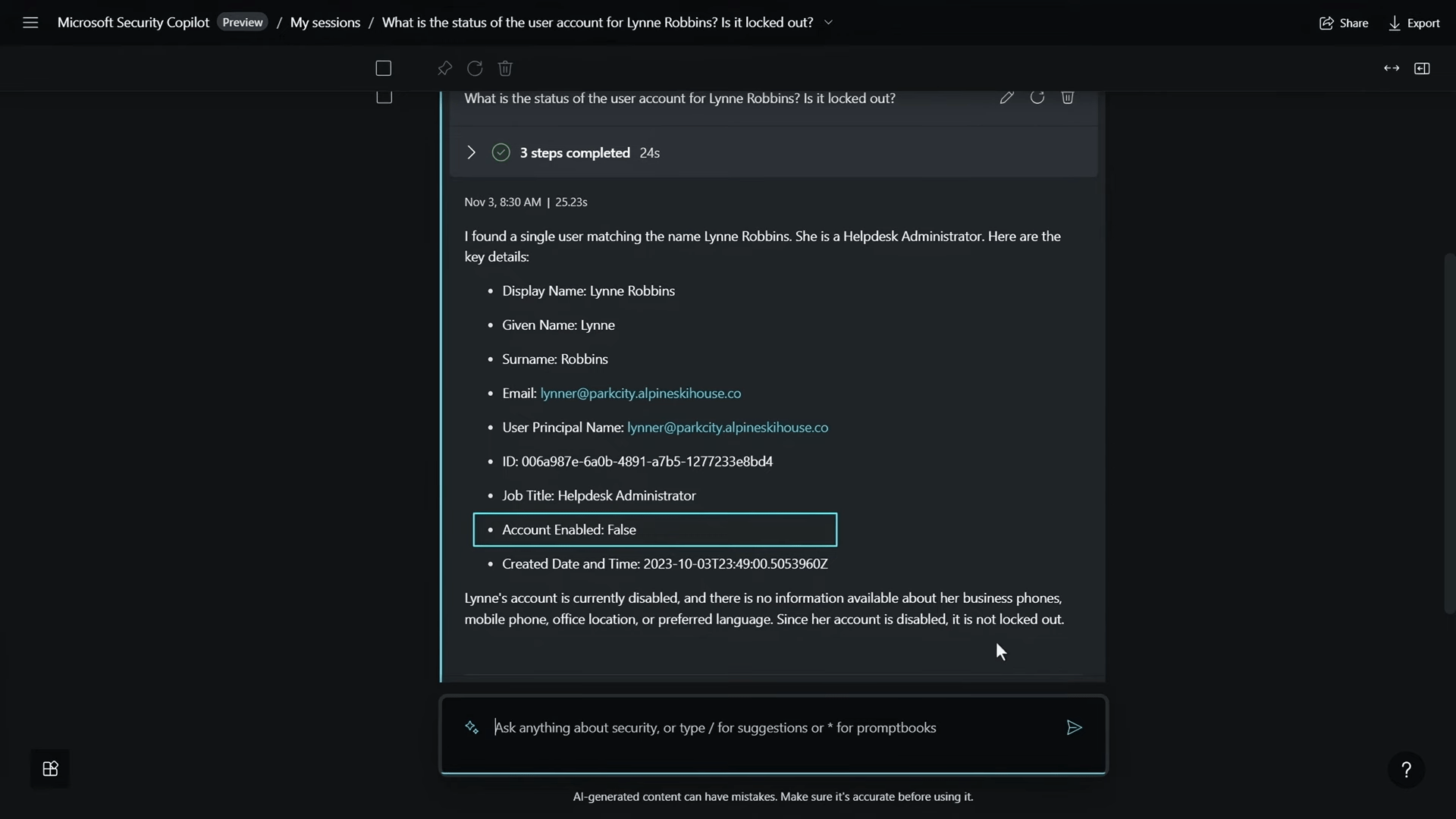
The AI, powered by connected plugins, swiftly analyzed the information and confirmed that Lynne’s account was disabled, providing additional details.
Keen to delve deeper, I queried, “What are the three most recent login attempts from the user?” Unveiling multiple failed login attempts from different devices and locations, it became evident that Lynne’s account was likely compromised.
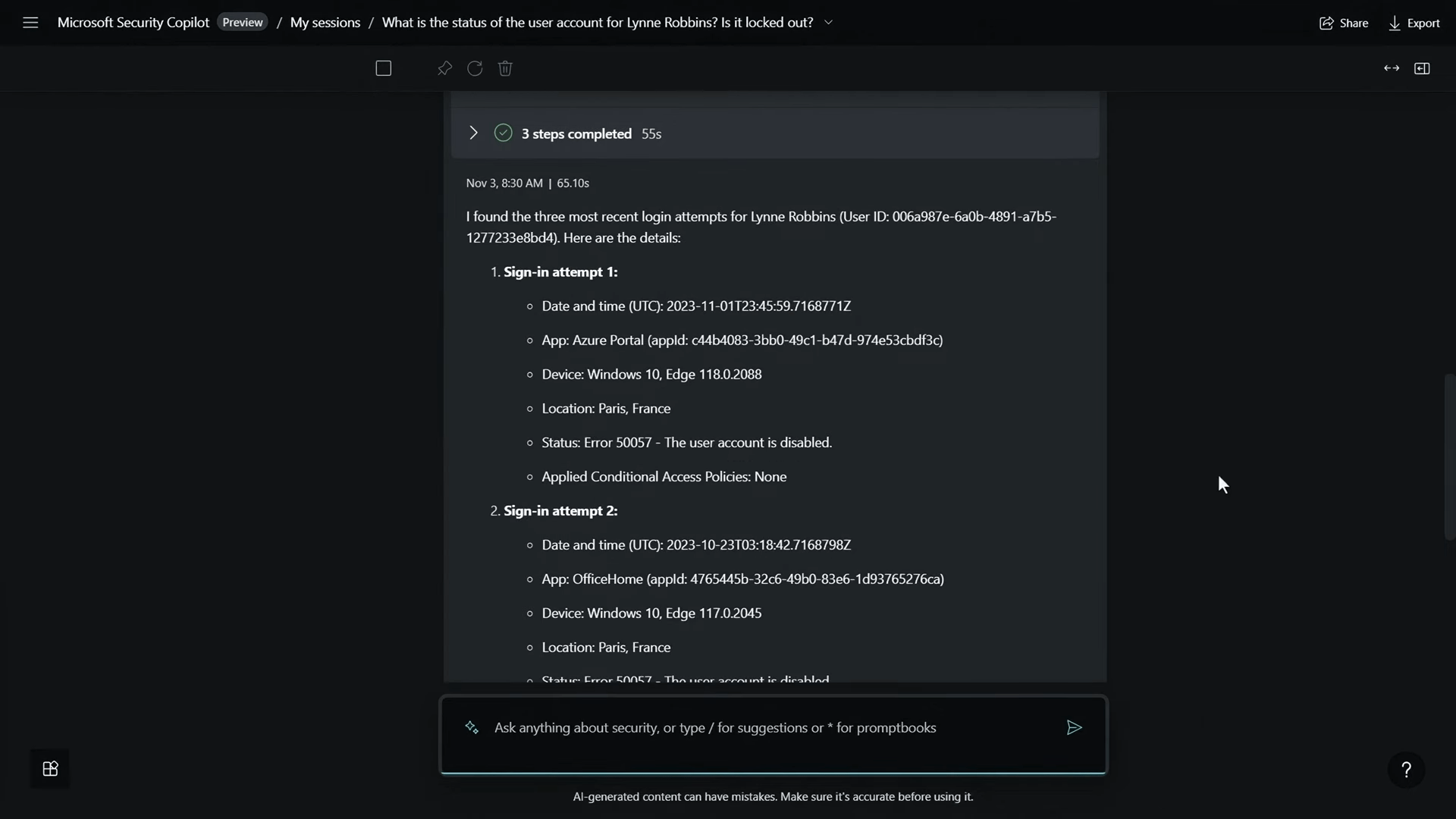
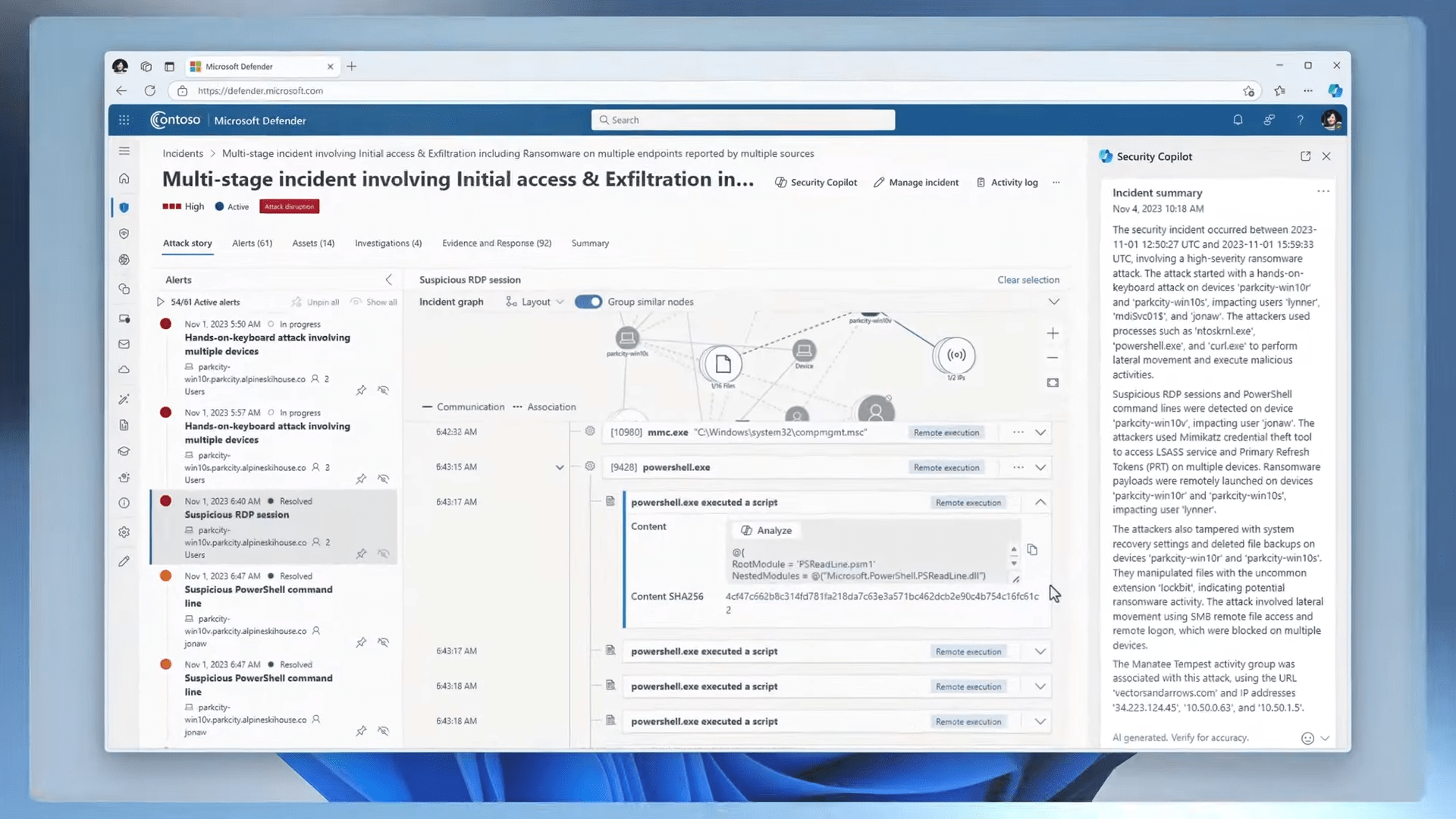
To assess the risk further, I inquired, “Is the user considered risky? If so, why?” Security Copilot revealed a high-risk level, prompting the need for additional details. Utilizing a security-specific skill, I initiated Defender-hunting queries by entering a forward slash. The hunt exposed a ransomware event with lateral movement within Woodgrove.
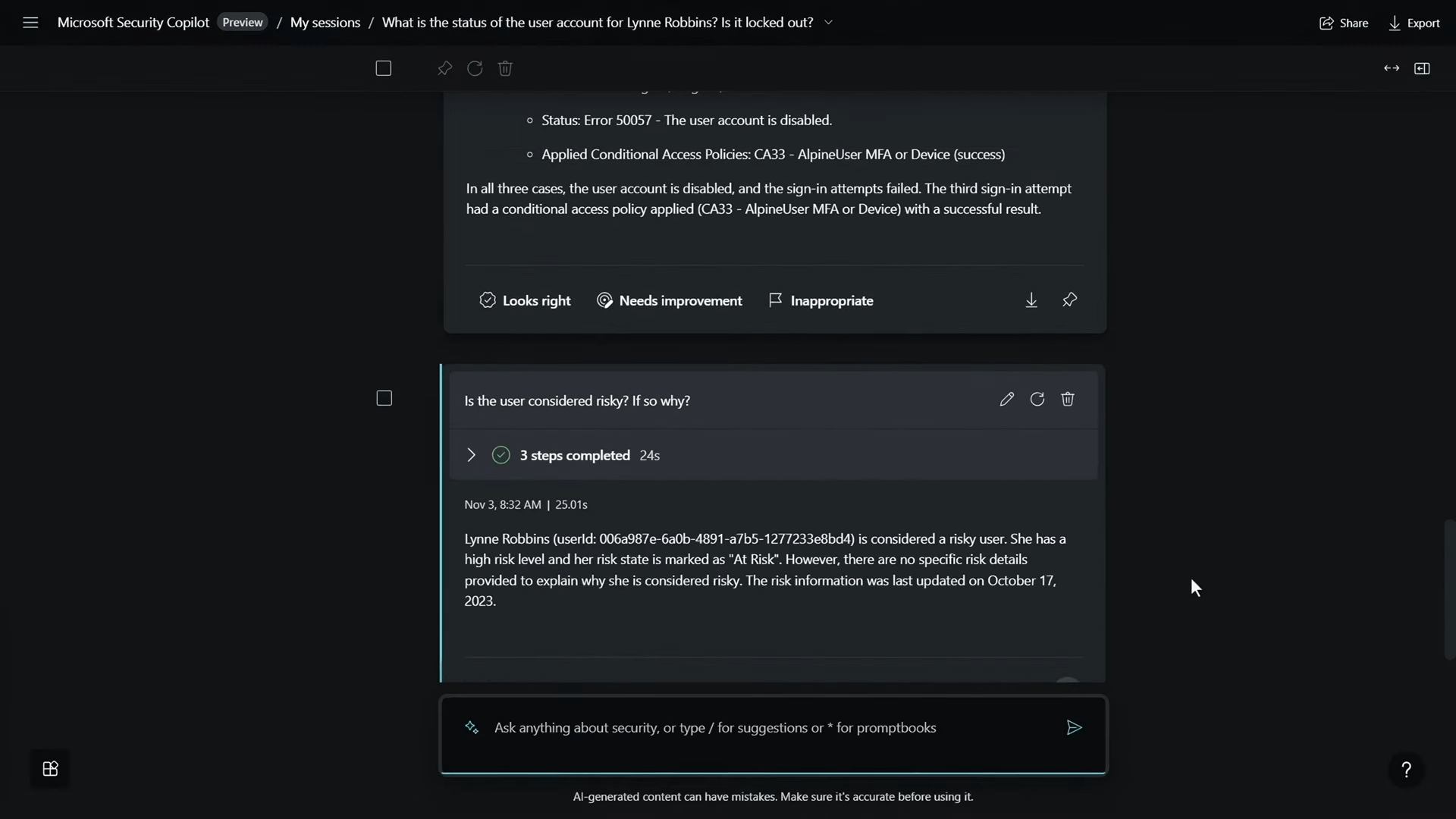
To aggregate the findings, I correlated the incident with the alerts, identified as incident 1-9-3-8-8. Requesting a summary of the incident, Security Copilot provided insights into a potential human-operated ransomware attack, emphasizing the severity of the situation.
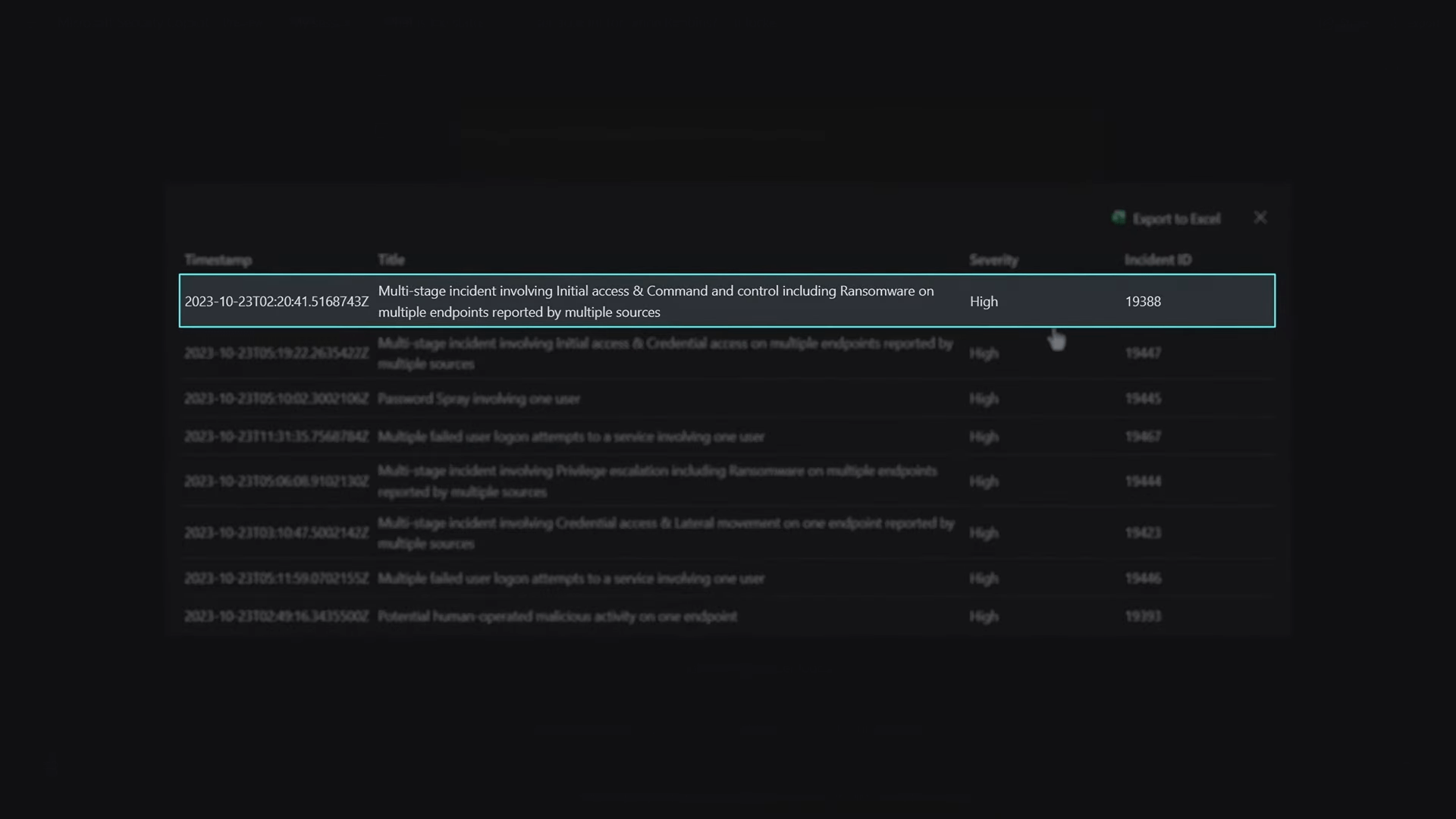
Acknowledging the urgency, my colleague pointed out the significance of Security Copilot’s ability to expedite the investigation, particularly in containing threats promptly. To demonstrate its efficiency further, we transitioned to a previously run incident, showcasing details such as detection time, alert generation, associated devices, threat actors, protocols used, processes, login attempts, and actions taken for remediation.
In the remediation phase, Security Copilot seamlessly generated a PowerShell script to check the state of the device’s SMB configuration, a critical step in addressing lateral movement. The script generation capability was highlighted as a valuable tool, eliminating the need to rely on short-term memory for complex command details.
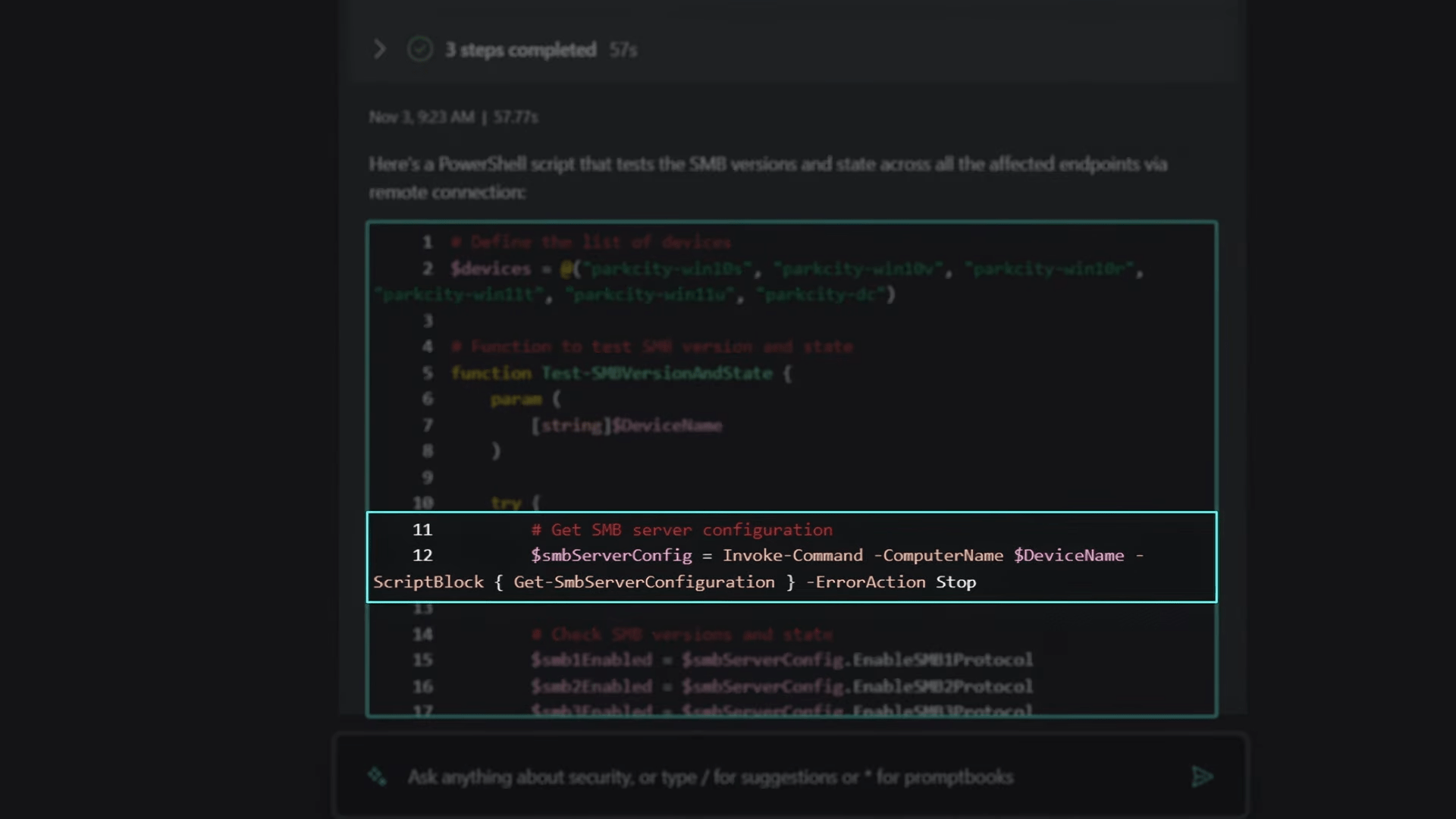
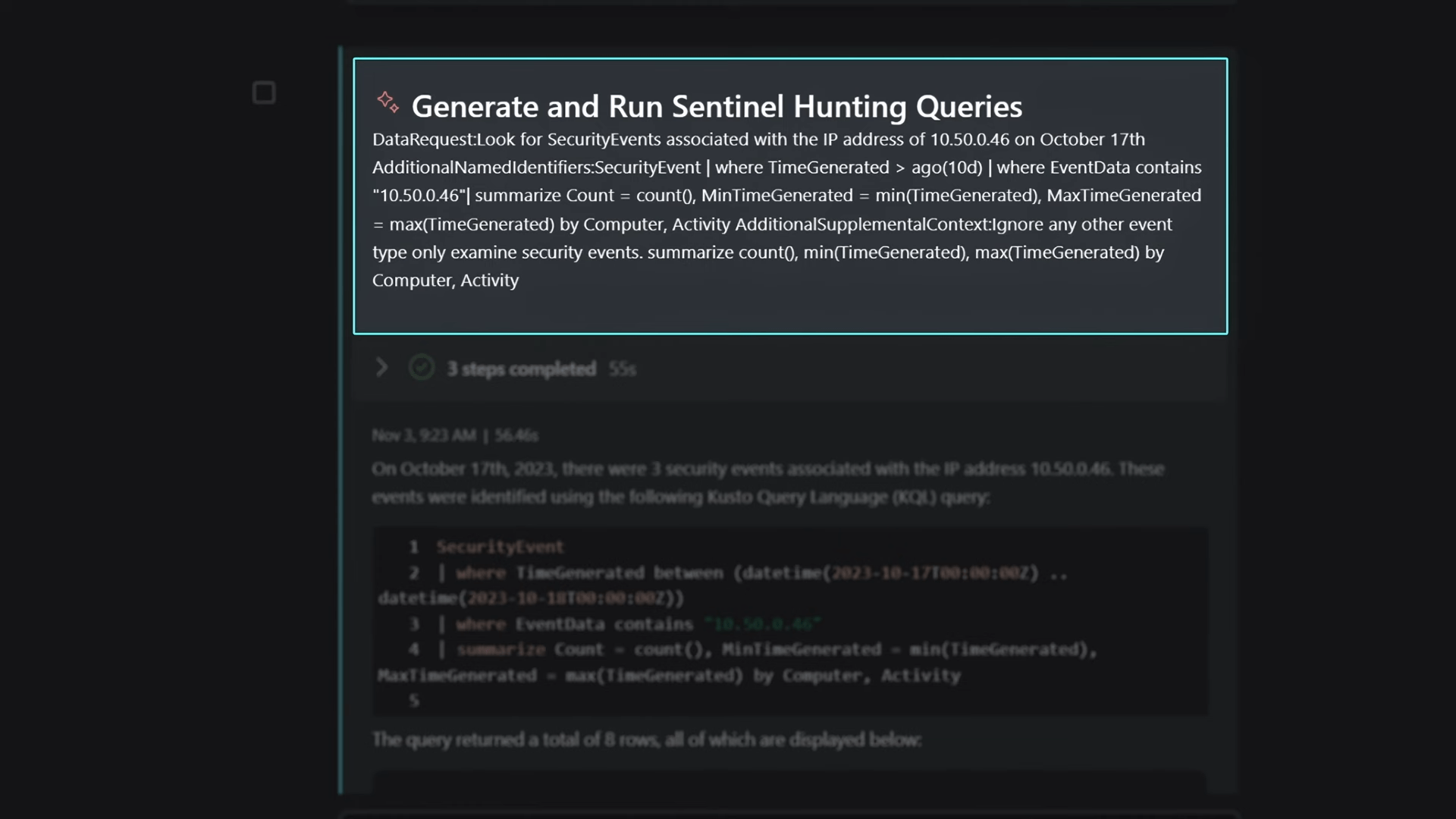
The focus then shifted to the initial machine compromised, utilizing another skill to find host name access records. Security Copilot retrieved access records, exposing lateral movement and the generation of a primary refresh token. A hunting query in Microsoft Sentinel was initiated to understand the attack vector and associated security events, providing a comprehensive view of the attack’s infiltration across the network.
Continuing the investigation, attention turned to devices associated with Lynne. Checking compliance status for the PARKCITY Win10S device, Security Copilot seamlessly accessed device information, revealing non-compliance with Defender for Endpoint policies. The analyst emphasized the value of Security Copilot’s ability to navigate through different aspects of the investigation seamlessly.
Generate a Hunting Query Using Microsoft Sentinel
Security Copilot seamlessly integrates with Microsoft Sentinel, allowing analysts to generate hunting queries using natural language prompts. In the example, the analyst identifies a ransomware event and lateral movement within the organization, correlating the information with an incident to gain a comprehensive view.
Threat Intelligence
The AI capabilities of Security Copilot extend to threat intelligence. Analysts can query the system for information about specific threat actor groups, gaining insights into the techniques used for exploits. This information is crucial for understanding and mitigating potential threats.
Embedded Copilot Experiences
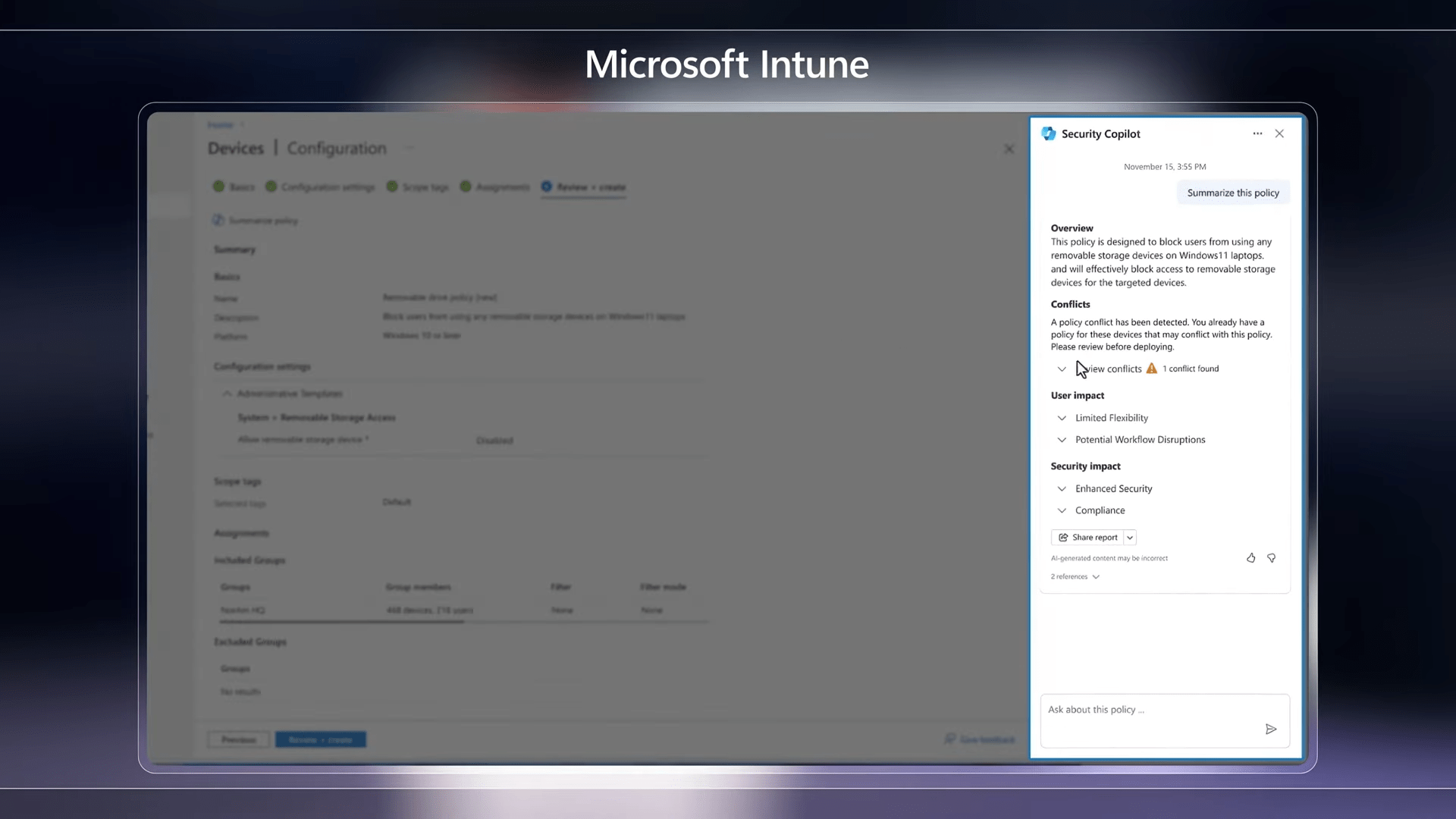
Security Copilot is integrated into various Microsoft admin portals, offering embedded experiences for endpoint management (Microsoft Intune), identity and access management (Microsoft Entra), and data security (Microsoft Purview). These integrations allow users to stay in context within the tools they use every day, simplifying policy management, risk assessment, and incident response.
For endpoint administrators utilizing Microsoft Intune, Security Copilot becomes a valuable ally in simplifying policy management. This entails the ability to generate policies effortlessly through natural language prompts, gain deeper insights into settings and options, and understand the potential impacts of chosen configurations. Additionally, administrators can swiftly access critical details about managed devices, streamlining the overall endpoint management process.
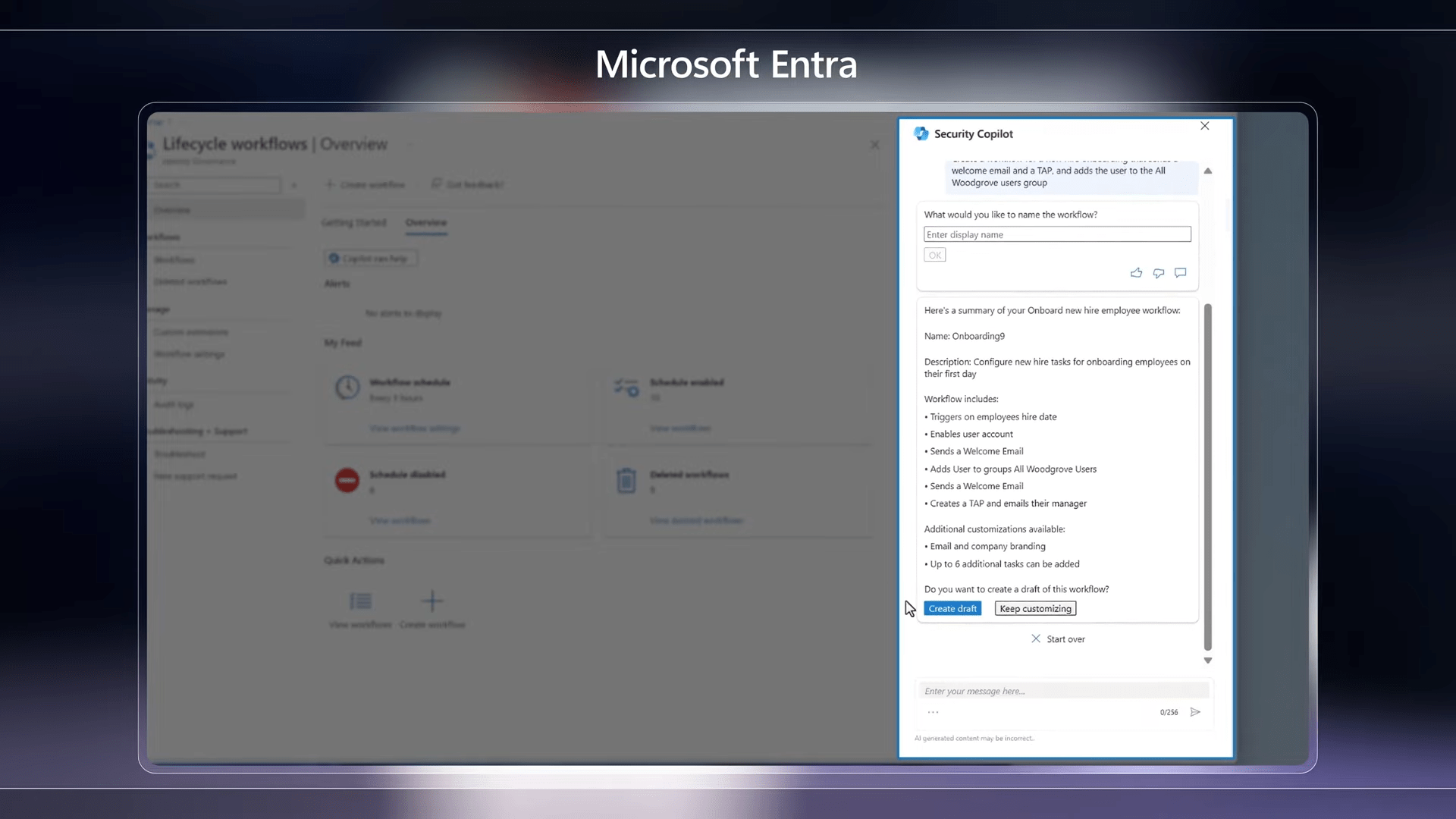
In the realm of identity administration, Security Copilot extends its capabilities through Microsoft Entra. Here, identity admins can harness natural language to inquire about users, groups, sign-ins, and permissions. Instantaneously, they receive a comprehensive risk summary along with step-by-step guidance for remediation, ensuring swift action for each identity at risk. Furthermore, Security Copilot within ID Governance facilitates the creation of lifecycle workflows, automating common tasks and enhancing operational efficiency.
Actionable Queries with Security Copilot
Security Posture Management
- Query: “Can Security Copilot assess our organization’s susceptibility to known vulnerabilities and exploits?”
- Actionable Response: Receive a prioritized list of risks along with guided recommendations to address vulnerabilities.
- Query: “What are the current high-risk vulnerabilities in our system?”
- Actionable Response: Get a detailed report on high-risk vulnerabilities, including prioritization and recommended actions.
- Query: “How can we enhance our security posture against specific threats?”
- Actionable Response: Receive actionable recommendations to strengthen security measures based on identified threats.
Incident Response
- Query: “Is there an ongoing cyberattack in our environment? What’s the scale?”
- Actionable Response: Receive real-time information on ongoing cyberattacks, including an assessment of the scale, and get instructions for remediation.
- Query: “What steps should we take to mitigate a potential ransomware attack?”
- Actionable Response: Get a step-by-step guide to mitigate the impact of a potential ransomware attack based on proven methods from real-world cybersecurity incidents.
- Query: “Has Security Copilot detected any unauthorized access to our sensitive data?”
- Actionable Response: Receive immediate insights into unauthorized access and actionable steps to respond and secure sensitive data.
Security Reporting
- Query: “Summarize the recent cybersecurity events for our executive team.”
- Actionable Response: Get a concise summary of recent cybersecurity events, incidents, or threats tailored for an executive audience.
- Query: “Prepare a customizable report on the latest threat intelligence for our security team.”
- Actionable Response: Receive a customizable report with the latest threat intelligence, allowing your security team to stay informed and take proactive measures.
- Query: “Can Security Copilot generate a report on the effectiveness of recent security measures?”
- Actionable Response: Obtain a report assessing the effectiveness of recent security measures, along with recommendations for improvement.
Wrap Up
Security Copilot significantly accelerates the investigation process, providing security teams with expert advice and insights. Its ability to use natural language prompts, integrate with various Microsoft services, and generate detailed reports makes it a valuable tool for addressing cybersecurity challenges.
How to Get Started
If you’re interested in incorporating generative AI into your security practices, you can join the early access program for Security Copilot at aka.ms/SecurityCopilot. By participating, you can also contribute to shaping the capabilities of Security Copilot.
In conclusion, Microsoft Security Copilot represents a powerful advancement in leveraging generative AI for cybersecurity, offering a comprehensive solution for investigating and responding to security incidents effectively.
Source: https://www.youtube.com/watch?v=0lg_derTkaM